Background
Azure has a bunch of built in roles but sometimes you need someone or something to be able to do a single task and don’t want to over permission their account.
Azure RBAC allows you to define a custom role with really granular permissions. To do this you can use PowerShell to pull one of Azure’s pre-defined templates, modify it in a text editor using JSON, then push it back as a custom defined role to assign to your user.
My example will be to create a user role that’s able to read BGP status information from the subscription. Initially I created a user and gave it the ‘Reader’ role but I hit the following error.
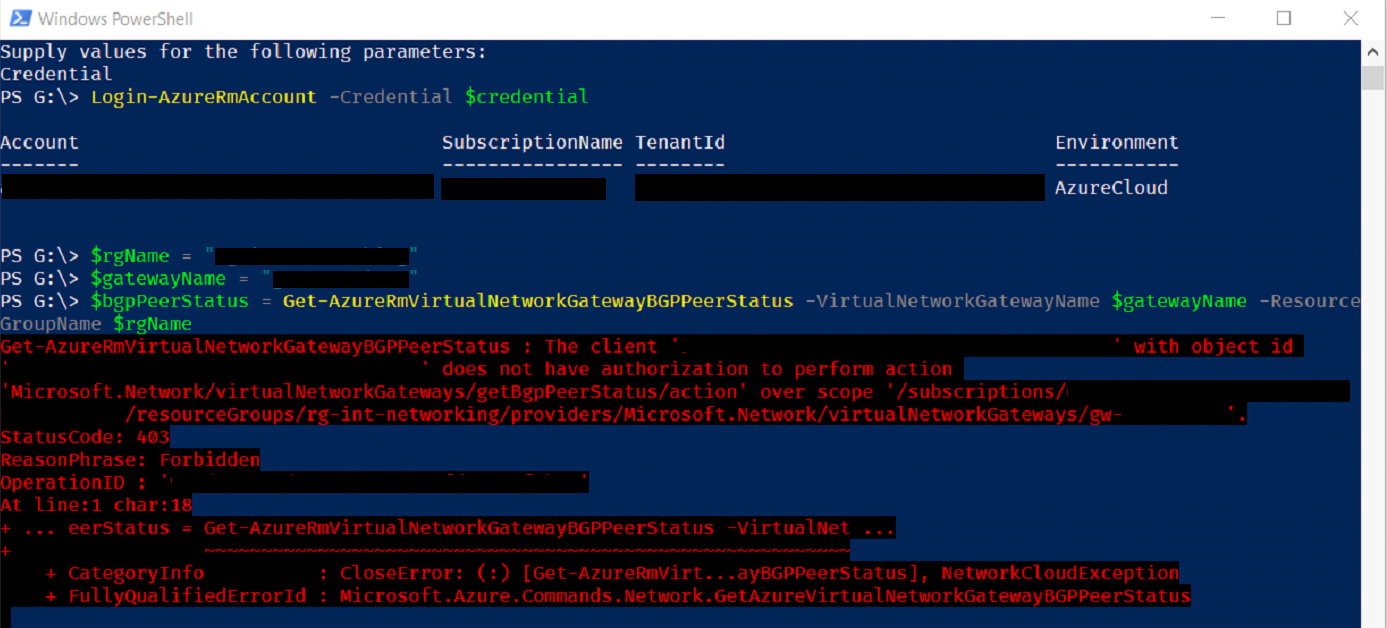
Take a note of the permission (Action) required, as this will be used to create the new role definition.
'Microsoft.Network/virtualNetworkGateway/getBgpPeerStatus/action'
Find a suitable role to copy
Check the list of RBAC roles by attempting to add role to a user on a subscription, resource group or resource in the portal. You can also run the following PowerShell command to get a list of all the resources in your subscription.
Get-AzureRmRoleDefinition
Once you’ve selected a template that’s similar to what you want, then get the definition and view the current permissions. I’m just using the ‘Reader’ role as it’s really simple and I only need a couple of additional permissions.
Get-AzureRmRoleDefinition "Reader"
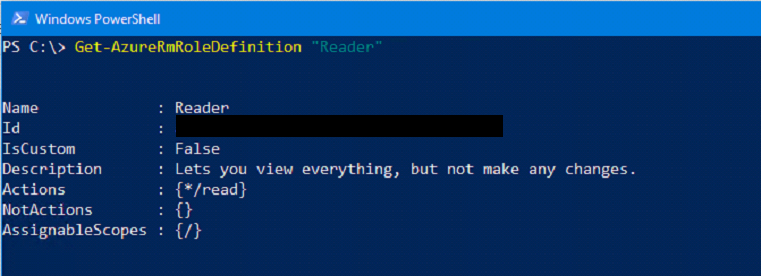
You can now export the definition to a JSON file for editing
Get-AzureRmRoleDefinition "Reader" | ConvertTo-Json | Out-File C:\Temp\CustomReader.json
Edit the file in a text editor. You need to remove the id tag and change IsCustom to true. Change the Name, Description and add in the Actions required.
{
"Name": "Reader",
"Id": "f3323452-47a2-4221-bc0c-d66f17e14e98",
"IsCustom": false,
"Description": "Can read all monitoring data.",
"Actions": [
"*/read"
],
"NotActions": [
],
"AssignableScopes": [
"/"
]
}
And here is my custom file, note I have set this to be limited to a subscription. Also, I have modified the Action to include all actions for virtualNetworkGateways.
{
"Name": "BGP Status Reader",
"IsCustom": true,
"Description": "Can read BGP Status data.",
"Actions": [
"*/read",
"Microsoft.Network/virtualNetworkGateways/*/action"
],
"NotActions": [
],
"AssignableScopes": [
"/subscriptions/ae015742-7715-42e3-bfbd-5beb36e89d18"
]
}
Once you’re happy with the modifications, you can use it to create a custom role definition.
New-AzureRmRoleDefinition -InputFile C:\Temp\CustomReader.json
You can now assign this role definition to your user account.
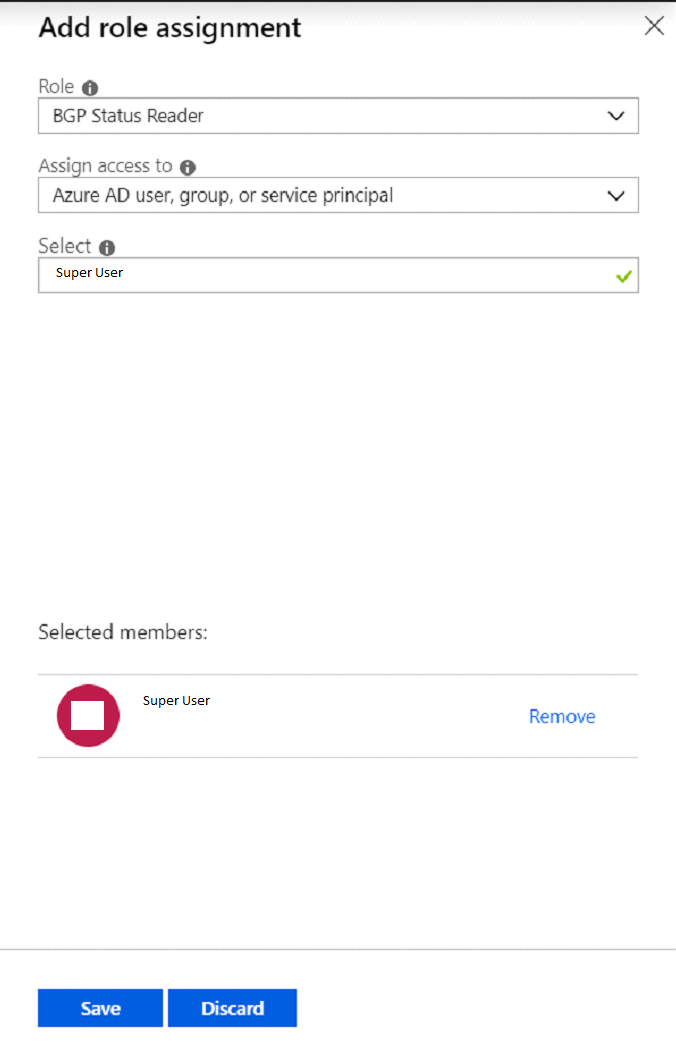
And re-run the problematic command.
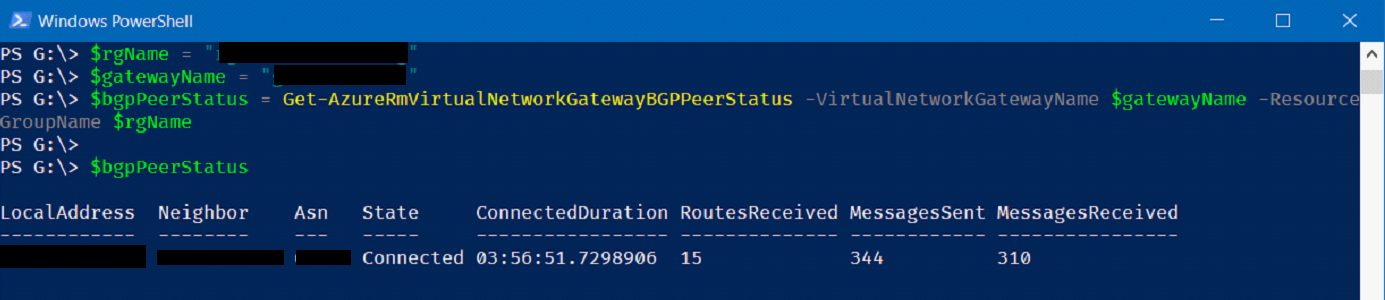
If you have difficulty and need to remove your custom role, you can run the following command.
Get-AzureRmRoleDefinition |
Where-Object { $_.isCustom } |
Where-Object { $_.Name -eq 'BGP Status Reader' } |
Remove-AzureRmRoleDefinition
Once the role is removed you can recreate it with the above commands. There is also a Set-AzureAzureRmRoleDefinition but this may require modifying your JSON.
Written with StackEdit.
