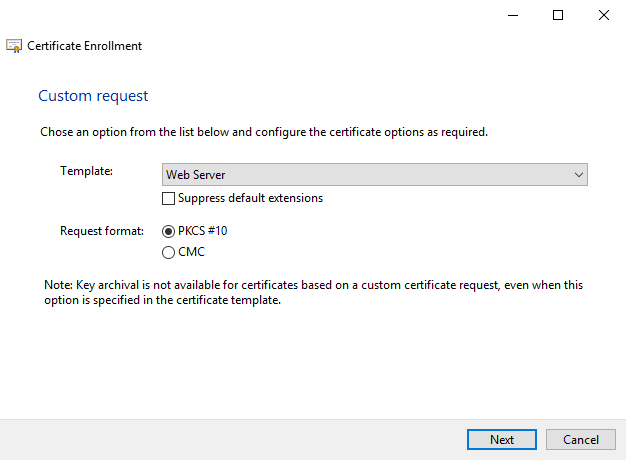
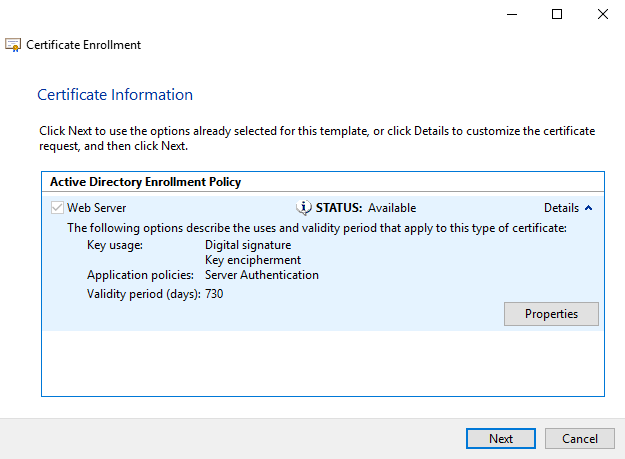
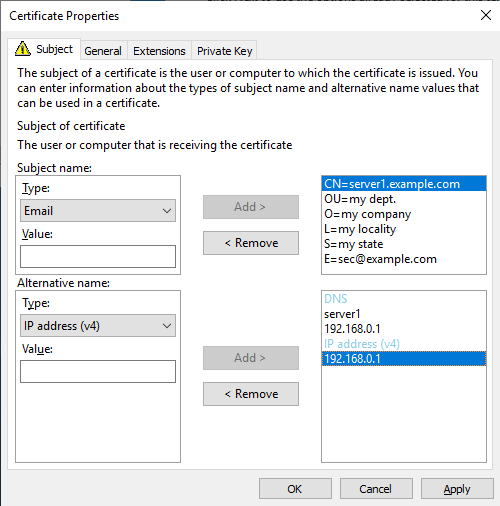
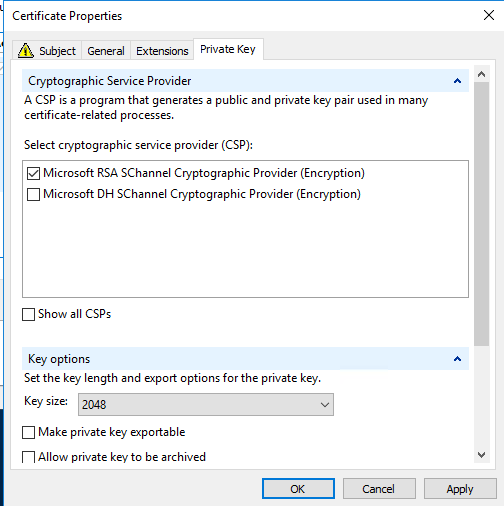
What’s the issue?
Nutanix CE requires an Intel CPU according to Nutanix. (portal.nutanix.com) Although it’s not supported you can modify an installation to run on a modern AMD CPU. I’m using an AMD Ryzen 3700X system running VMware Workstation 15.
You can probably modify this config to run on bare metal just by changing the minimum_reqs.py to allow AMD.
System Used
- AMD Ryzen 3700X
- 32 GB 3200Mhz RAM
- Windows 10 1909
- VMware Workstation 15
- Nutanix CE 2019.11.22 image
Thanks
- The VMware part of this guide is made possible by the work of Tim Smith and his post here (tsmith.co)
Get Started
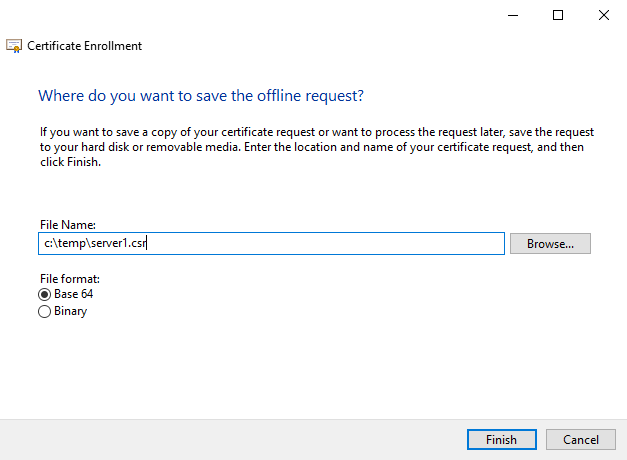
- Download the “Disk Image-based Full Install” from here (next.nutanix.com)
- Extract
ce-2019.11.22-stable.imgfromce-2019.11.22-stable.img.gz. I used 7-Zip.
Create the Nutanix CE virtual machine
- Create a new folder for your vm, I called mine nutanix
- Move
ce-2019.11.22-stable.imginto the folder - Rename
ce-2019.11.22-stable.imgtoce-flat.vmdk - Create a new file called
ce.vmdkand insert the following:
The ce.vmdk disk descriptor file, more information here (kb.vmware.com)
# Disk DescriptorFile
version=1
encoding="UTF-8"
CID=4a23b86a
parentCID=ffffffff
createType="vmfs"
# Extent description
RW 14540800 VMFS "ce-flat.vmdk" 0
# The Disk Data Base
#DDB
ddb.adapterType = "lsilogic"
ddb.geometry.cylinders = "905"
ddb.geometry.heads = "255"
ddb.geometry.sectors = "63"
ddb.longContentID = "39ab32063800e361c1c248034a23b86a"
ddb.uuid = "60 00 C2 91 19 55 99 b4-0c 1e 38 af 74 3f 10 2d"
ddb.virtualHWVersion = "14"
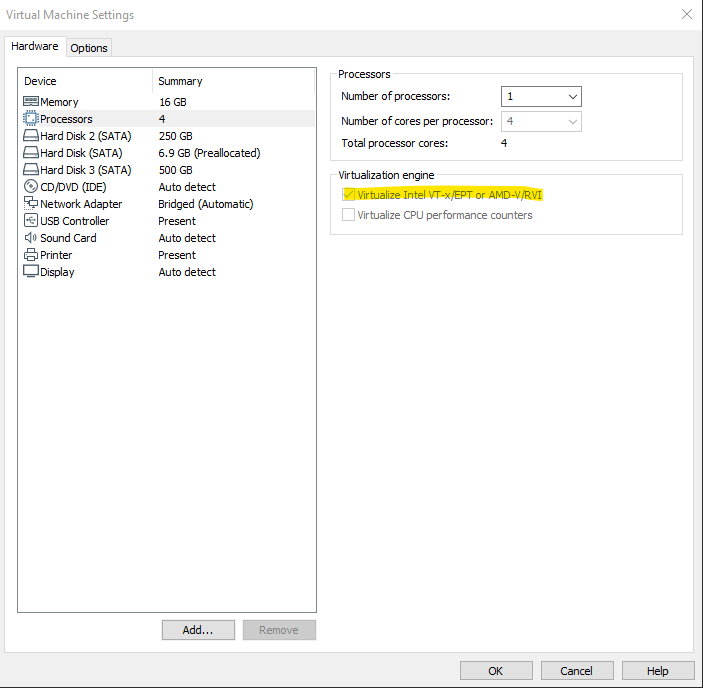
- Open VMware Workstation and create a new virtual machine with the following specs:
- 1 vCPU, 4 Cores
- 16 GiB RAM
- Virtualize Intel VT-x/EPT or AMD-V/RVI enabled (see fig 2.1)
- Attach the ce.vmdk as the first hard disk, select SATA as the bus
- Add a new 250 GiB disk on an SSD backed volume, select SATA as the bus
- Add a new 500 GiB disk, select SATA as the bus
fig 2.1:
- Start her up
AMD Specifics
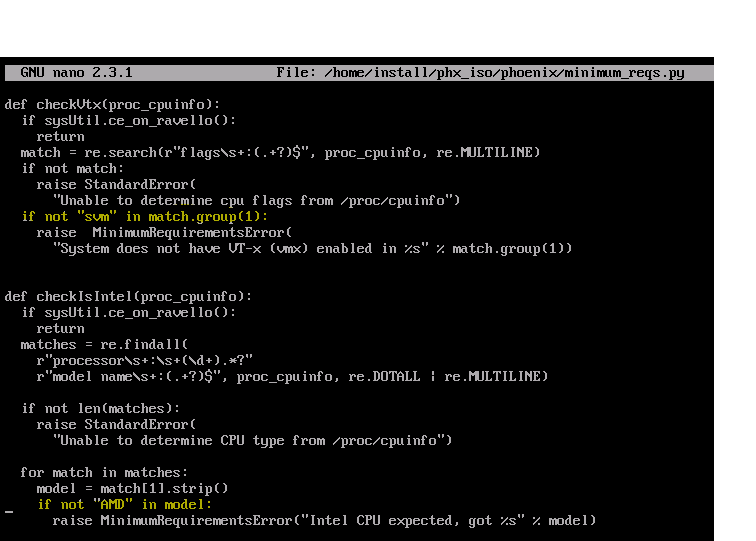
- Once the system is booted, login with
rootandnutanix/4u - Edit the
minimum_reqs.py
code:
nano -c /home/install/phx_iso/phoenix/minimum_reqs.py
- Find line 52, replace
vmxwithsvm - Find line 70, replace
IntelwithAMD:)
fig 2.2:
VMware Specifics
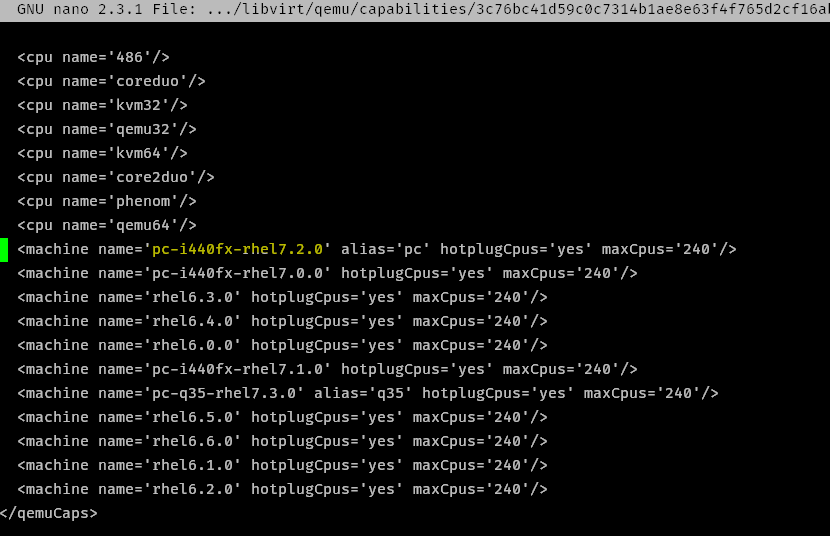
- Modify the capabilities xml file:
code:
nano /var/cache/libvirt/qemu/capabilities/3c76bc41d59c0c7314b1ae8e63f4f765d2cf16abaeea081b3ca1f5d8732f7bb1.xml
- Delete the line pc-i440fx-rhel7.2.0 near the very bottom (CTRL+K)
- Edit the line containing
pc-i440fx-rhel7.3.0modify topc-i440fx-rhel7.2.0
fig 2.3:
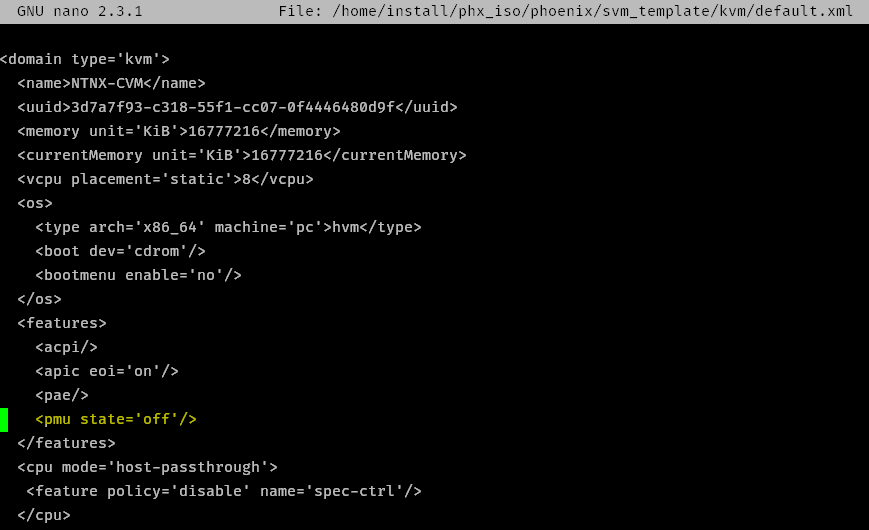
- Modify the CVM default.xml
code:
nano /home/install/phx_iso/phoenix/svm_template/kvm/default.xml
- Add
<pmu state='off'/>to the<features>section
I believe this is disabling the “Performance Monitoring Unit” (linux-kvm.org) in libvirt
fig 2.4:
Install Nutanix
- type
exitto go back to the login screen, login withinstallno password, then follow the instructions
Troubleshooting
- If the VM doesn’t boot and errors with
dracut-initqueue timeoutcomplaining it can’t find disk by UUID. Make sure your disks are all set to SATA on the bus - If the CVM won’t start after running install make sure you made the relevant VMware specific modifications.
- If the installer won’t run complaining Intel VT-x is not running, make sure you have nested virt enabled on the vCPU - see fig 2.1. Also make sure you made the right changes to the
minimum_reqs.pyfile.
Written with StackEdit.