Windows Process Command Line Logging
Introduction
There are many reasons to gather process launch information in a Windows environment. Troubleshooting, Security forensics, Performance Analysis to name a few. By default, Windows does not log process launch information so it will need to be configured using local or group policy.
There are some security consequences of enabling process command line logging. Some commands, including some legacy AD commands require using a password or secret key as a parameter. Ideally we wouldn’t want these secrets appearing in logs, unfortunately the the only way to exclude them is to disable command line logging which substantially reduces the usefulness of enabling process logging in the first place.
Reading the logs requires local administrator rights on the system, however this could lead to privilege escalation; for instance if a logged command line included a Domain Admin password. The usefulness in forensics though, may be more benefit than the risk of having secrets in the Windows Event log. It may be prudent to configure log forwarding to a hardened server and regular log rotation on client and server systems.
Required Policy Settings
Warning: Enabling the Audit: Force audit policy subcategory settings policy will override any basic policy settings that are configured on the system. These should be translated to the equivalent advanced audit settings if they are required.
In order for Windows to log event ID 4688 so that you can see Windows process creation events and their command lines, there are several policy settings to configure:
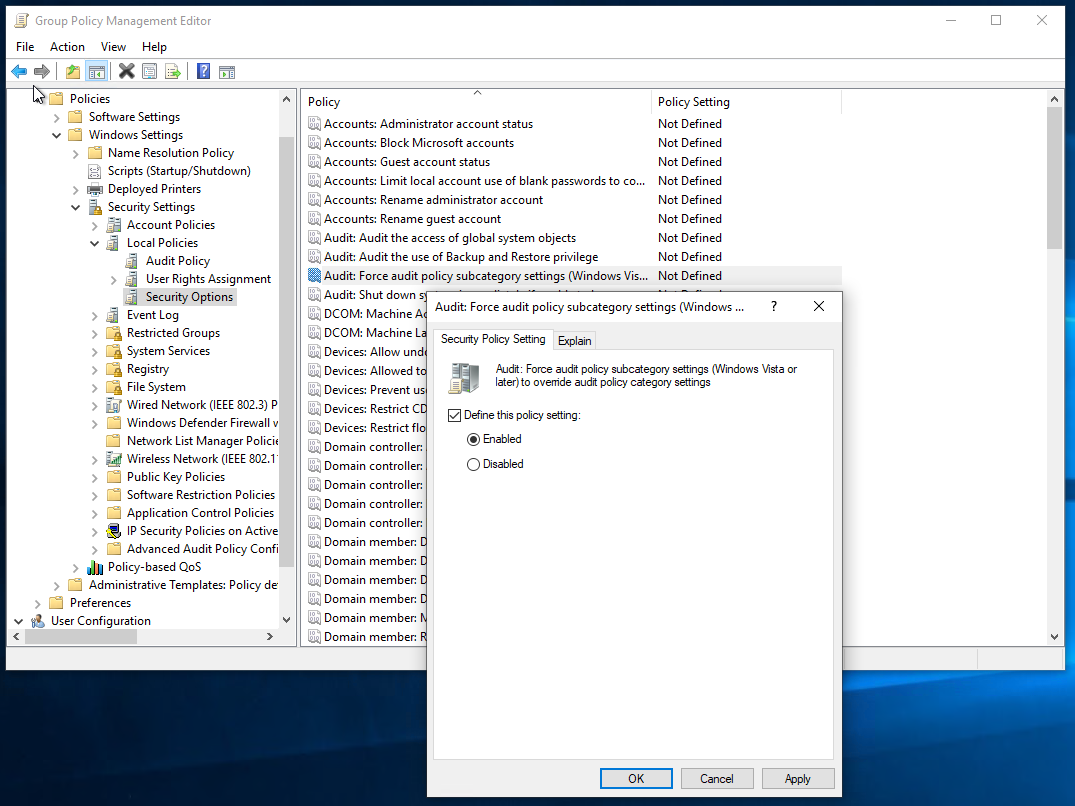
Enable Audit: Force audit policy subcategory settings policy in Computer Configuration\Policies\Windows Settings\Local Policies\Security Options
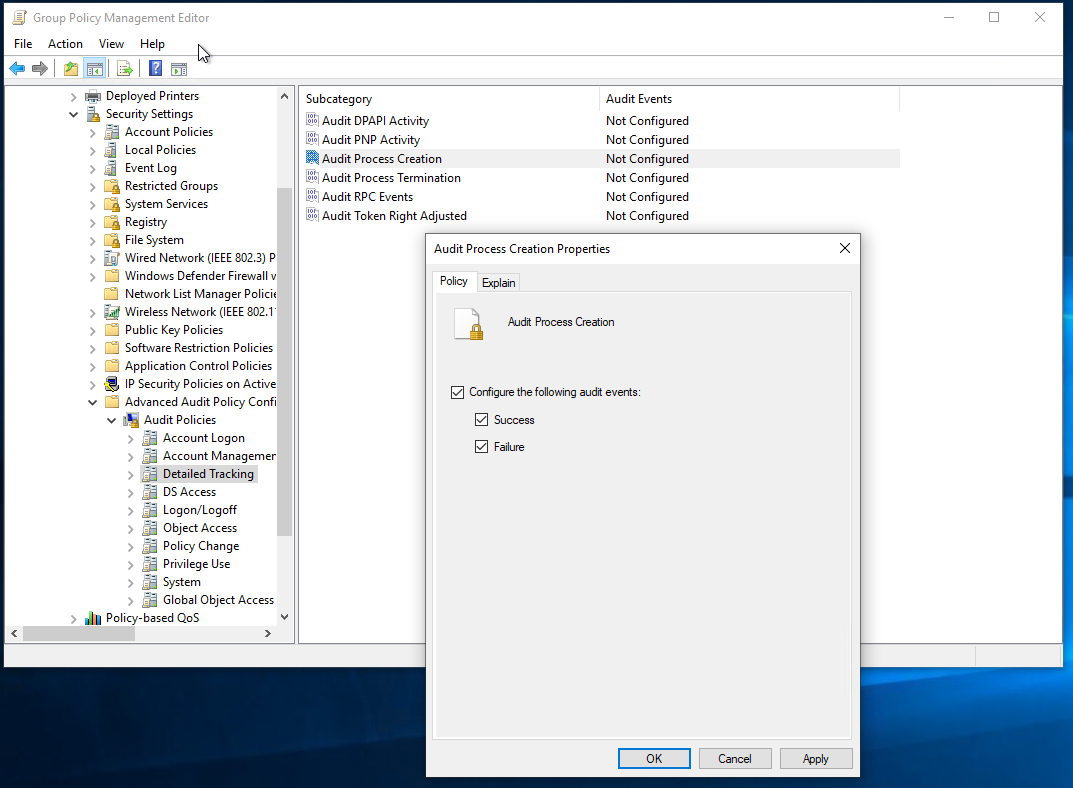
Enable the Audit Process Creation policy in Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Configuration\Audit Policies\Detailed Tracking
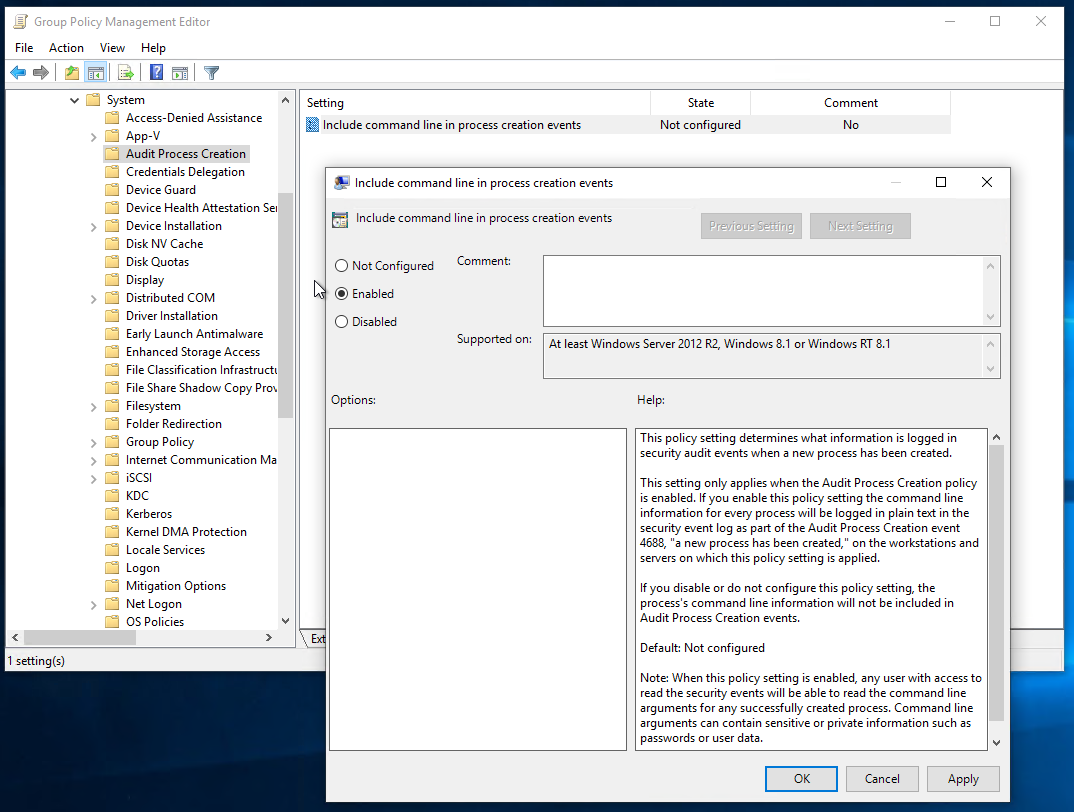
Enable the Include command line in process creation events setting in Administrative Templates\System\Audit Process Creation
Audit: Force audit policy subcategory settings
Audit Process Creation
Include command line in process creation events
If using Group Policy, once the policy is saved, run gpupdate /force on the targeted system. Once applied, running auditpol /get /category:* should show the appropriate audit policies being applied.
Troubleshooting
While deploying this group policy, I noticed that Process Creation was not being set when running auditpol /get /category:*. After enabling an unrelated advanced audit policy such as Account Lockout in the Logon/Logoff category, the Process Creation policy was applied. I was then able to remove Account Lockout while still keeping Process Creation. I’m not exactly sure why this issue ocurred, but I think it happened due to the order the policy elements were applied.
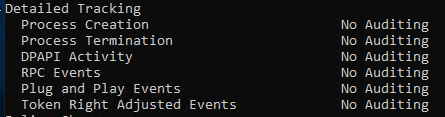
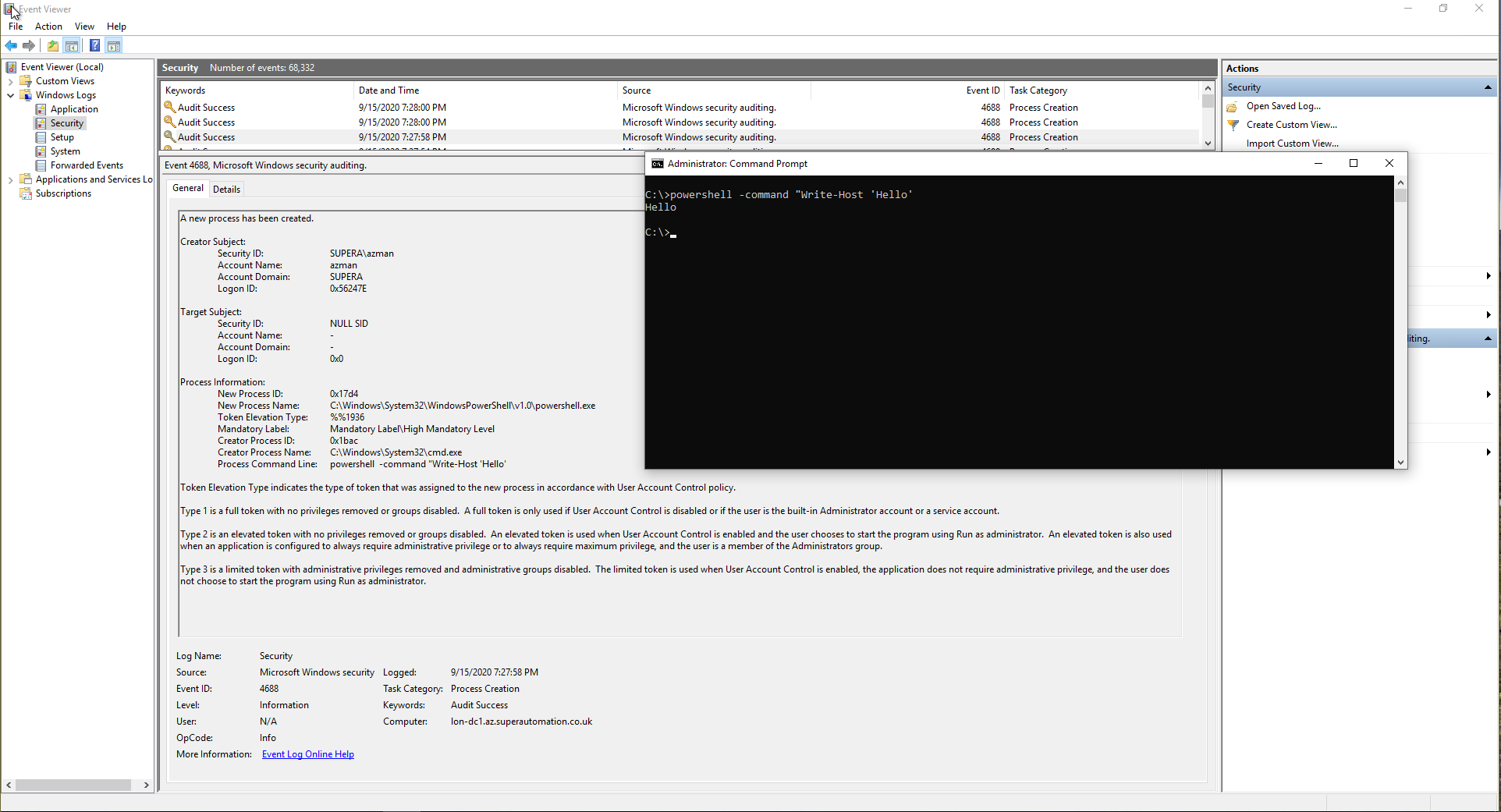
Reviewing the Windows Event Log
Once the above policy and audit settings are in place then the system will begin logging event ID 4866 in the System event log
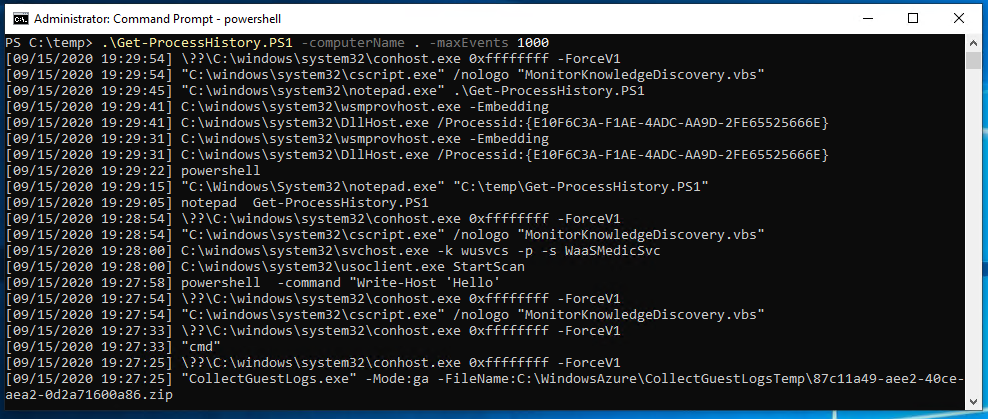
Gathering Process History for a machine in PowerShell
Looking at windows event logs can be time consuming and tedious, so here is a short PowerShell script to parse the event log on a target machine for recent commands:
Script Output:
Extending with SysInternals Sysmon
While logging process creation events with the full command line is a powerful forensic tool, there is much more detailed logging available in SysInternals Sysmon. Next time I will be installing and configuring Sysmon to generate more verbose forensic logs including process creation and termination, generation of suspicious file modification and deletion logs, Registry modification and even WMI event logging.
Gathering Domain Controller Audit Policy
I’ve also written a quick script to gather the audit policy for all Domain Controllers in the domain. You can find it here.
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)